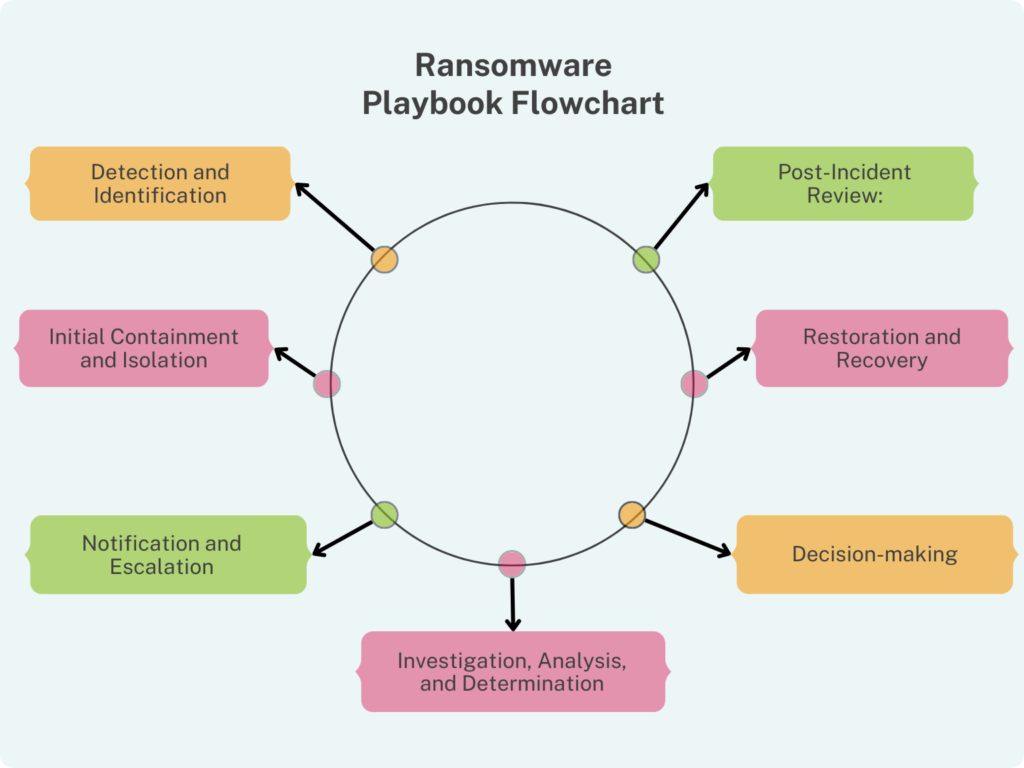
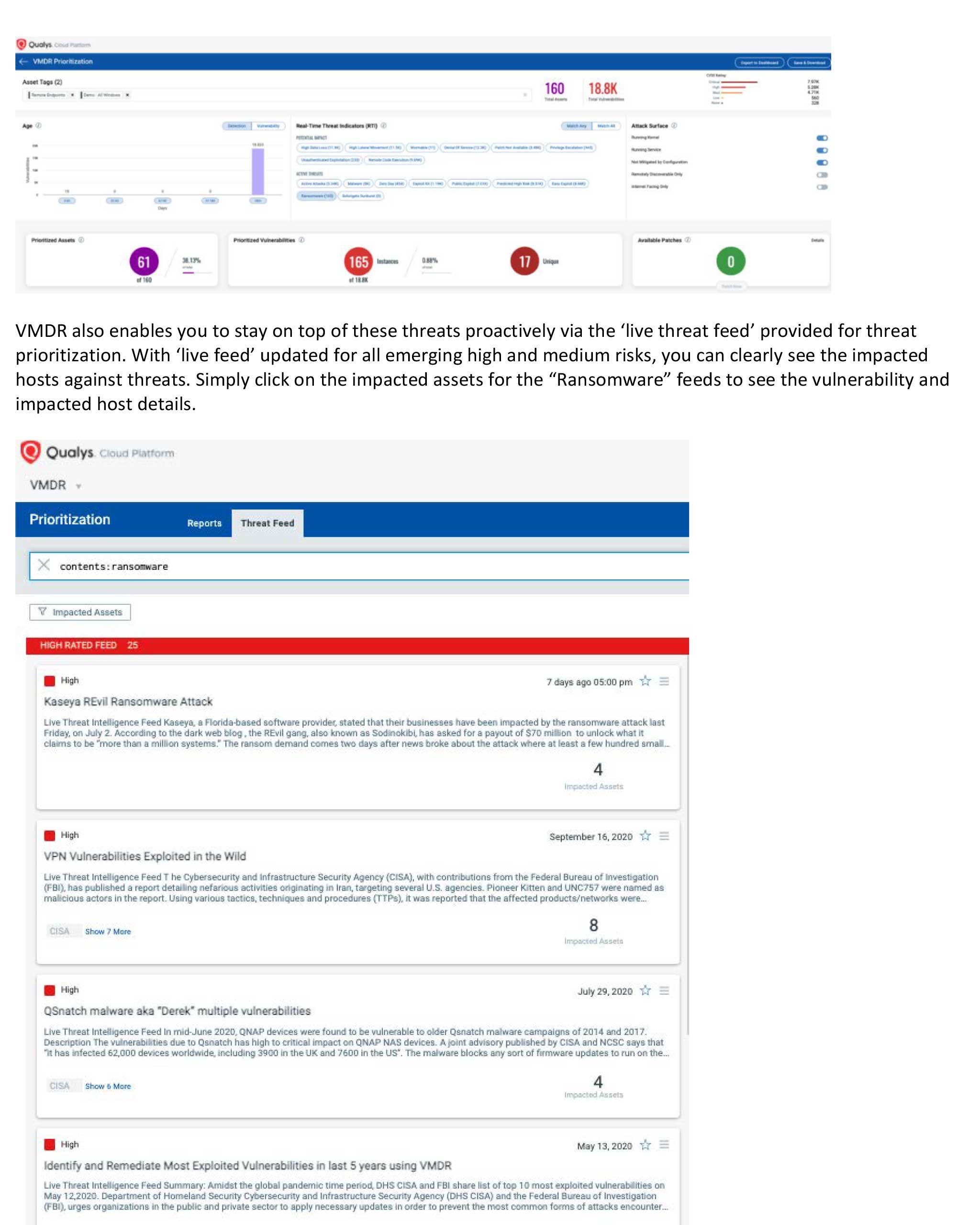
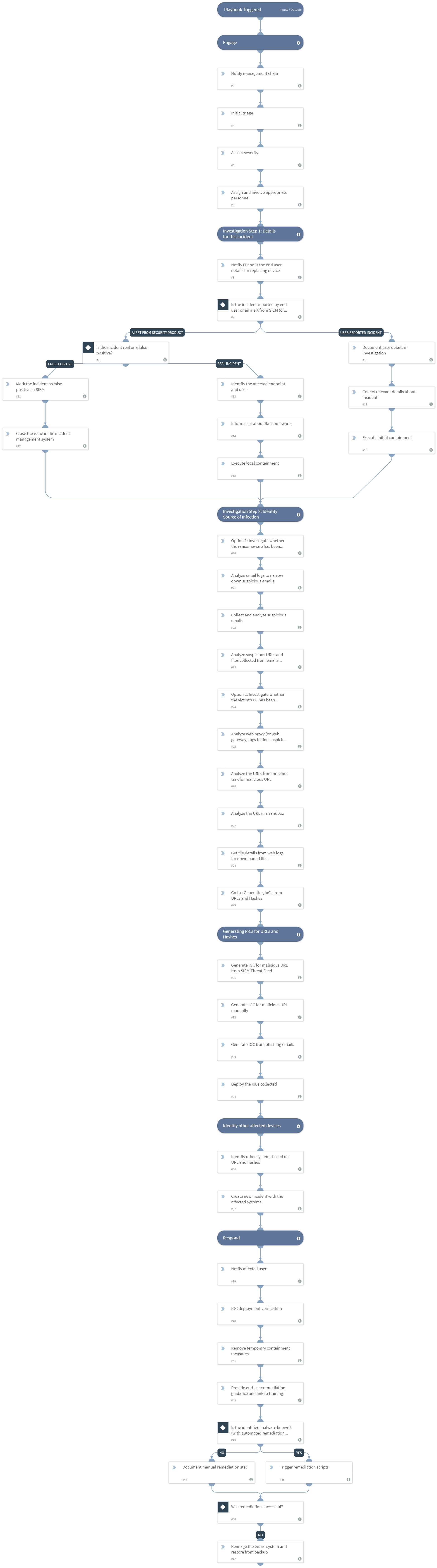
Ransomware Playbook Template
Ransomware Playbook Template - Trusted by over 30 million users worldwide. This includes protecting data and devices from ransomware and being ready to respond. This playbook template is intended to outline a structured and specific approach in response. Assess the scope of the incident run through this list of questions and tasks to discover the extent of the attack. Web this playbook covers steps that can be used to deal with ransomware. Defend against ransomware with our comprehensive defense & response guide. Ad download free virus protection to protect your devices againest viruses and malware. Used in cyberattacks that can paralyze organizations, ransomware is malicious. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. Web institute ransomware playbook how to prepare for, respond to, and recover from a ransomware attack cyber readiness institute 2020 | [email protected]. Assess the scope of the incident run through this list of questions and tasks to discover the extent of the attack. Fast, free antivirus software 2023. This playbook is a manual playbook. 2) detection, identification, and analysis; Web 3 contributors feedback you need to respond quickly to detected security attacks to contain and remediate its damage. Web nist releases tips and tactics for dealing with ransomware. Web up to 20% cash back an incident response plan or playbook should cover all four stages of a breach: Trusted by over 30 million users worldwide. Ad download free virus protection to protect your devices againest viruses and malware. Ad stop ransomware attacks in their tracks. Web the following diagram provides a visual representation of how ransomware can infect your networks and devices, highlighting the three main access vectors. Ad stops viruses, spyware, malware and ransomware with six powerful layers of protection. This playbook is a manual playbook. Web up to 20% cash back an incident response plan or playbook should cover all four stages of. Web how to create a runbook template for uniform documentation. Web the following diagram provides a visual representation of how ransomware can infect your networks and devices, highlighting the three main access vectors. 2) detection, identification, and analysis; Ad stop ransomware attacks in their tracks. Introduction ransomware offers a unique and pressing threat to the business. This playbook is a manual playbook. This toolkit provides the necessary. Web nist releases tips and tactics for dealing with ransomware. Ad eliminate the ransomware protection security gap. 06 december 2021 summary ransomware attacks require a unique approach to handling the associated incident response. Enjoy a lifetime of powerful & essential free antivirus protection. This includes protecting data and devices from ransomware and being ready to respond. Ad stops viruses, spyware, malware and ransomware with six powerful layers of protection. Assess the scope of the incident run through this list of questions and tasks to discover the extent of the attack. Introduction ransomware offers. Web how to create a runbook template for uniform documentation. Resources enhance your skills with access. Web this playbook covers steps that can be used to deal with ransomware. This toolkit provides the necessary. Web institute ransomware playbook how to prepare for, respond to, and recover from a ransomware attack cyber readiness institute 2020 | [email protected]. As new widespread cyberattacks happen,. Web the following diagram provides a visual representation of how ransomware can infect your networks and devices, highlighting the three main access vectors. Discover the missing link in today's ransomware protection stack Introduction ransomware offers a unique and pressing threat to the business. 2) detection, identification, and analysis; Web up to 20% cash back an incident response plan or playbook should cover all four stages of a breach: Fast, free antivirus software 2023. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. Discover the missing link in today's ransomware protection stack Web 3 contributors feedback you need. Attackers may also steal an. Ad eliminate the ransomware protection security gap. 2) detection, identification, and analysis; Microsoft 365 defender can provide a. As new widespread cyberattacks happen,. Web how to create a runbook template for uniform documentation. Web fortunately, organizations can take steps to prepare for ransomware attacks. Web up to 20% cash back an incident response plan or playbook should cover all four stages of a breach: Attackers may also steal an. Web 3 contributors feedback you need to respond quickly to detected security attacks to contain and remediate its damage. 06 december 2021 summary ransomware attacks require a unique approach to handling the associated incident response. Microsoft 365 defender can provide a. 2) detection, identification, and analysis; Resources enhance your skills with access. Ad stops viruses, spyware, malware and ransomware with six powerful layers of protection. To avoid inconsistencies and disaster, implement a runbook template to strengthen your existing. This playbook template is intended to outline a structured and specific approach in response. Used in cyberattacks that can paralyze organizations, ransomware is malicious. Download template purpose to serve as a ransomware incident response guide. Web ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access. Web this playbook covers steps that can be used to deal with ransomware. Web containment is critical in ransomware incidents, prioritize accordingly.</strong> Defend against ransomware with our comprehensive defense & response guide. Introduction ransomware offers a unique and pressing threat to the business. Web the following diagram provides a visual representation of how ransomware can infect your networks and devices, highlighting the three main access vectors.Ransomware Playbook Disaster Recovery ACUTEC
Free Ransomware Response Playbook ORNA
Quick Facts from the Ransomware Playbook Cyber Readiness Institute
Ransomware Playbook Cyber Readiness Institute
Incident Response Playbook StatusCast
Ransomware Defense Playbook
Ransomware Playbook Cyber Readiness Institute
Ransomware Playbook ACUTEC
Complimentary Infographic + Ransomware Playbook Qualys, Inc.
content/playbookransomware_README.md at master · demisto/content · GitHub
Related Post: