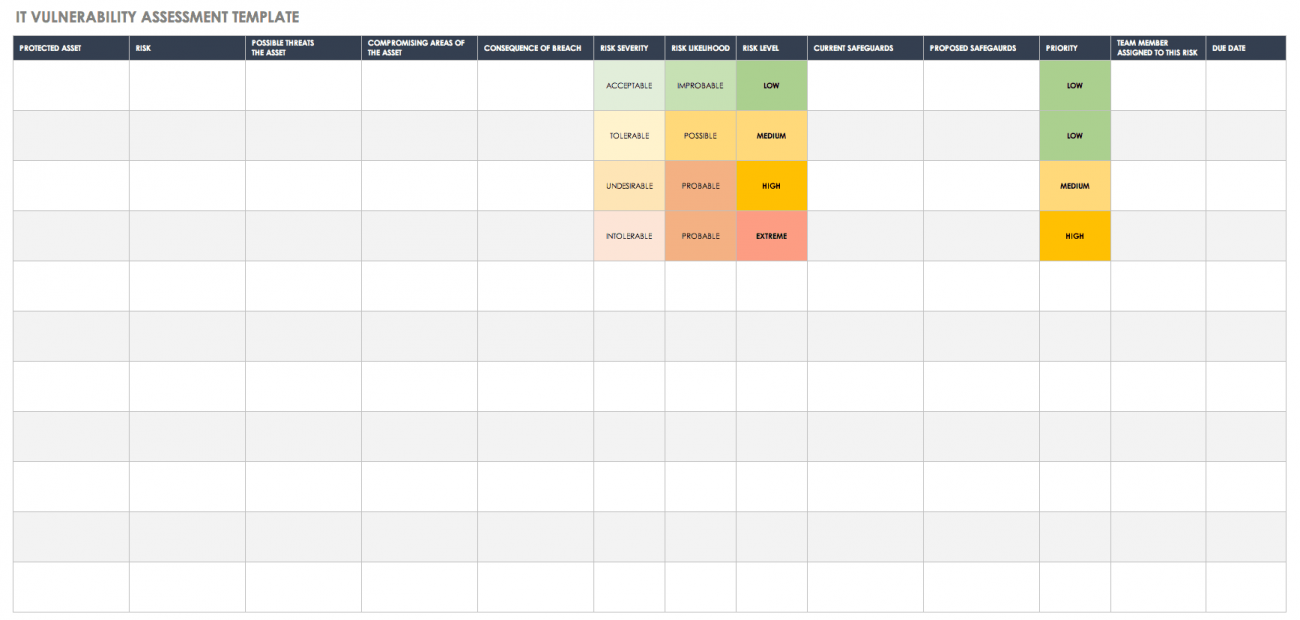
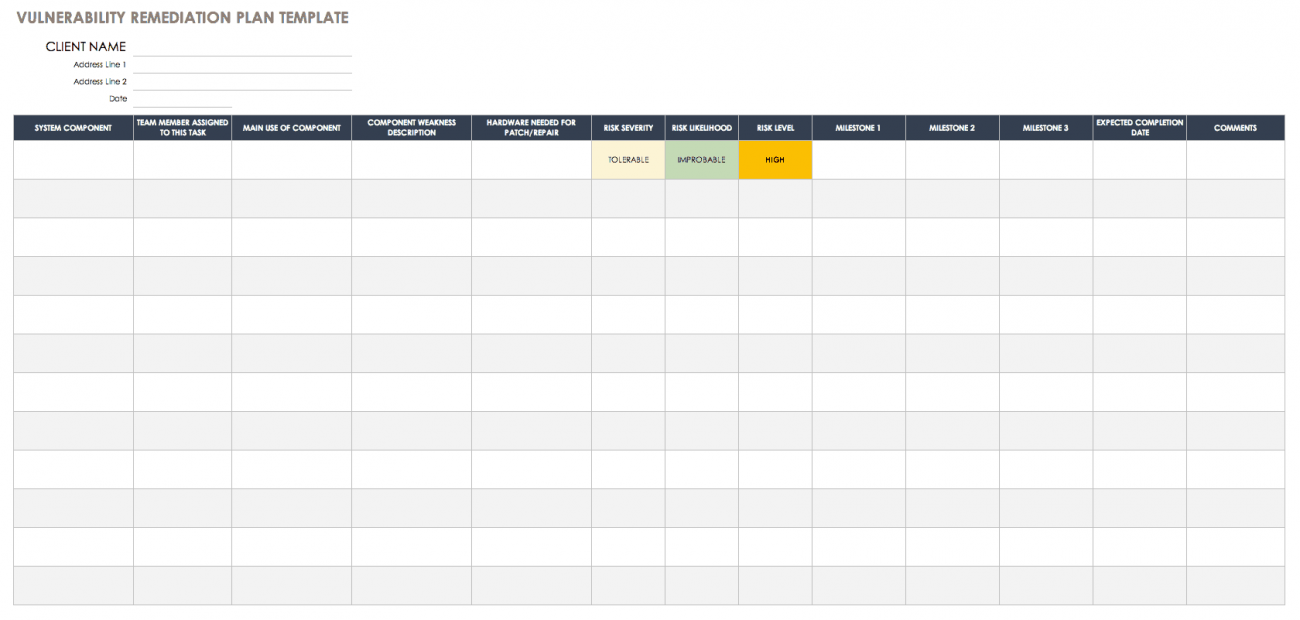
Vulnerability Tracking Spreadsheet Template
Vulnerability Tracking Spreadsheet Template - In this method, all the data is brought together in a single. Web vulnerability remediation processes include detecting trends, managing possible risks and overseeing assignment groups. Be sure you don’t put [attacks] or [controls] in this category. Access 24/7 experts for managed detection & response. 2 how to document remediation? Pci dss, iso 27001, soc, hipaa and hitrust. The discovery of vulnerabilities and the analysis of pertinent vulnerabilities. Track every stock move from purchase to warehouse bin to sales order. Our security scanner will help you keep up with the latest patches for all your servers Web control catalog spreadsheet (new) the entire security and privacy control catalog in spreadsheet format; 3 how to track remediation? Web 1 why document and track remediation? Web get free smartsheet templates. A4, us download now project assessment template. In this article, you’ll find the most comprehensive selection of free vulnerability assessments, available in microsoft excel and word, pdf, and google sheets formats. In this article, you’ll find the most comprehensive selection of free vulnerability assessments, available in microsoft excel and word, pdf, and google sheets formats. Web enhance vulnerability management with our iso 27001 tracking spreadsheet. Web free vulnerability assessment templates get free smartsheet templates by andy marker | april 5, 2019 in this article, you’ll find that most comprehensive selection are. The discovery of vulnerabilities and the analysis of pertinent vulnerabilities. Web vulnerability management requires an organization to understand and assess two specific capabilities: Web creating and implementing an vulnerability management policies and procedures is a vital component of any company’s cyber security strategy, and is required by several standards including: We've created a susceptibility leitung policy template to find organizations. Ad learn how businesses defend against threats with mdr for microsoft 365. Web tracking the results of scanning over time so that you can run reports on the types of vulnerabilities you’re identifying, which vulnerabilities have been addressed and how long they take to fix. Defines reports to verify compliance with this policy; List weaknesses at be addressed along because. This is meant as a substitution for organizations that do not currently have any software or service management. Pci dss, iso 27001, soc, hipaa and hitrust. Web tracking the results of scanning over time so that you can run reports on the types of vulnerabilities you’re identifying, which vulnerabilities have been addressed and how long they take to fix. Web. 2 how to document remediation? Be sure you don’t put [attacks] or [controls] in this category. Web every vulnerability should follow this template. Web 1 why document and track remediation? Web get free smartsheet templates. Web vulnerability management requires an organization to understand and assess two specific capabilities: Ad trace lots and serial numbers everywhere in your supply chain. Track, prioritise, and remediate vulnerabilities for robust information security. 2 how to document remediation? Web vulnerability remediation processes include detecting trends, managing possible risks and overseeing assignment groups. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Empower your team with huntress mdr. 6 here’s what else to consider. Web enhance vulnerability management with our iso 27001 tracking spreadsheet. The discovery of vulnerabilities and the analysis of pertinent vulnerabilities. 6 here’s what else to consider. Ad learn how businesses defend against threats with mdr for microsoft 365. In this method, all the data is brought together in a single. Access 24/7 experts for managed detection & response. Pci dss, iso 27001, soc, hipaa and hitrust. Empower your team with huntress mdr. In this article, you’ll find the most comprehensive selection of free vulnerability assessments, available in microsoft excel and word, pdf, and google sheets formats. 6 here’s what else to consider. Web tracking the results of scanning over time so that you can run reports on the types of vulnerabilities you’re identifying, which vulnerabilities have. We've created a susceptibility leitung policy template to find organizations assess and patch security frailties. Defines reports to verify compliance with this policy; Web we've created a vulnerability management policy template until help organizations assess and patch security vulnerabilities. Pci dss, iso 27001, soc, hipaa and hitrust. Access 24/7 experts for managed detection & response. Web download patching plus vulnerability management plan template. Our security scanner will help you keep up with the latest patches for all your servers Web control catalog spreadsheet (new) the entire security and privacy control catalog in spreadsheet format; In this method, all the data is brought together in a single. Create an vulnerability assessment activity schedule template that focuses on remediation. Web free vulnerability assessment templates get free smartsheet templates by andy marker | april 5, 2019 in this article, you’ll find that most comprehensive selection are liberate vulnerability assessments, available in microsoft excel and word, pdf, and. 2 how to document remediation? Ad trace lots and serial numbers everywhere in your supply chain. Be sure you don’t put [attacks] or [controls] in this category. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. The discovery capability requires the expertise to assess the assets and associated. 6 here’s what else to consider. Provides penalties for failure to comply with this policy Web vulnerability remediation processes include detecting trends, managing possible risks and overseeing assignment groups. The discovery of vulnerabilities and the analysis of pertinent vulnerabilities.Free Vulnerability Assessment Templates Smartsheet
Vulnerability Tracking Spreadsheet inside Vulnerability Tracking
Vulnerability Tracking Spreadsheet pertaining to Excel Spreadsheet
Vulnerability Tracking Spreadsheet for Vulnerability Management Metrics
Vulnerability Tracking Spreadsheet in Outstanding Remediations Tracking
Vulnerability Tracking Spreadsheet Spreadsheet Downloa vulnerability
Free Vulnerability Assessment Templates Smartsheet
Vulnerability Tracking Spreadsheet intended for Security Report Example
Vulnerability Tracking Spreadsheet Spreadsheet Downloa vulnerability
Vulnerability Tracking Spreadsheet with Financial Planning Spreadsheet
Related Post: