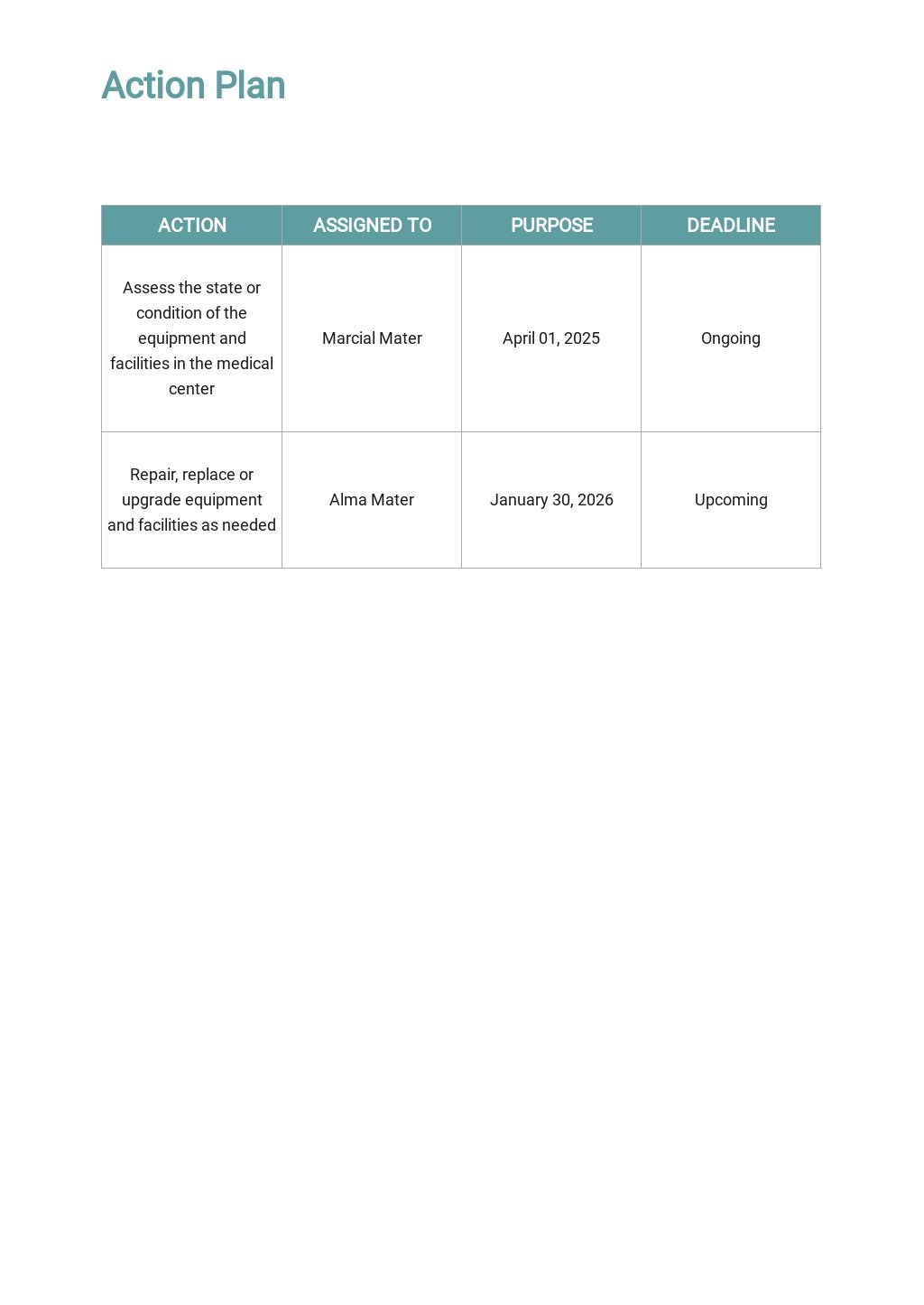
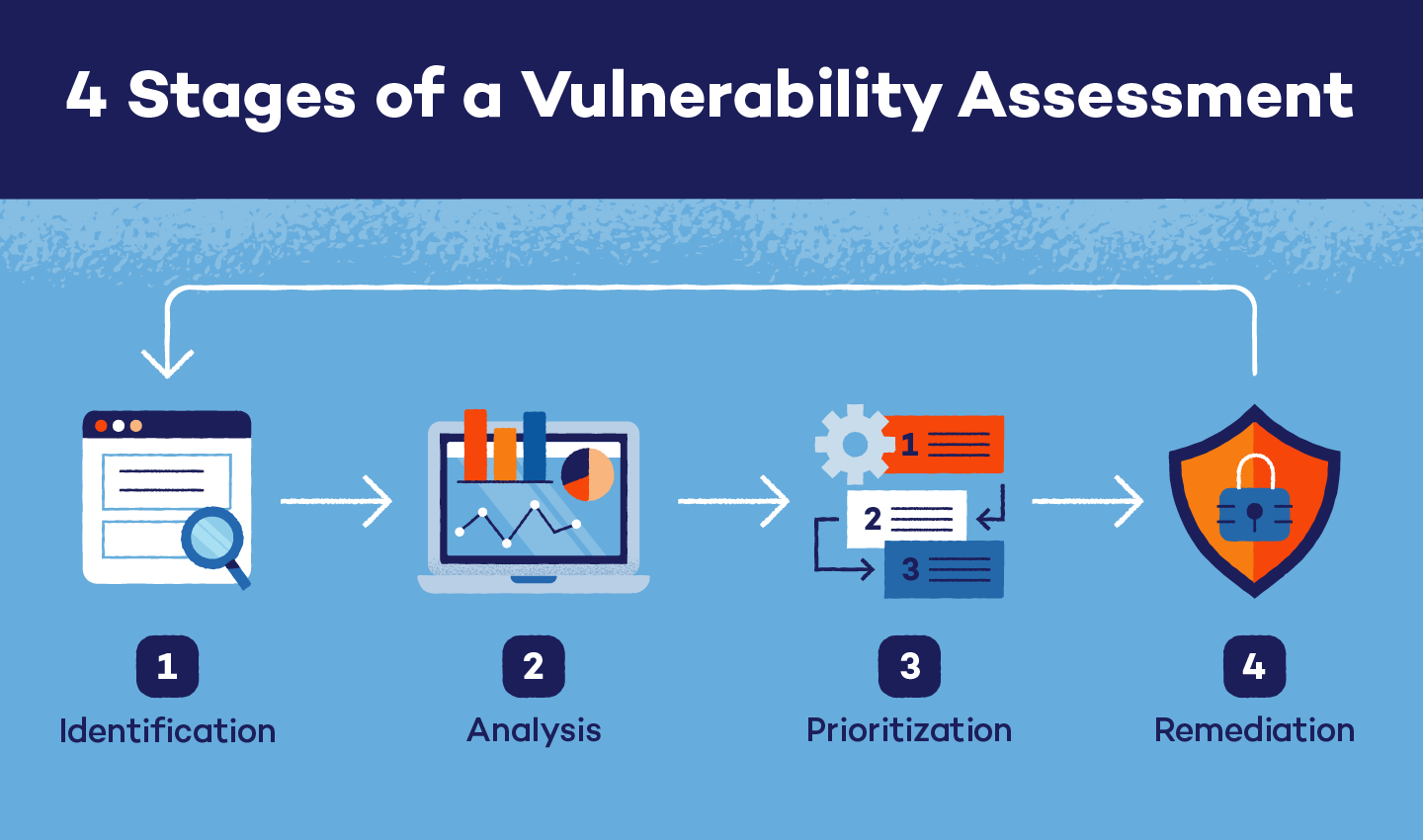
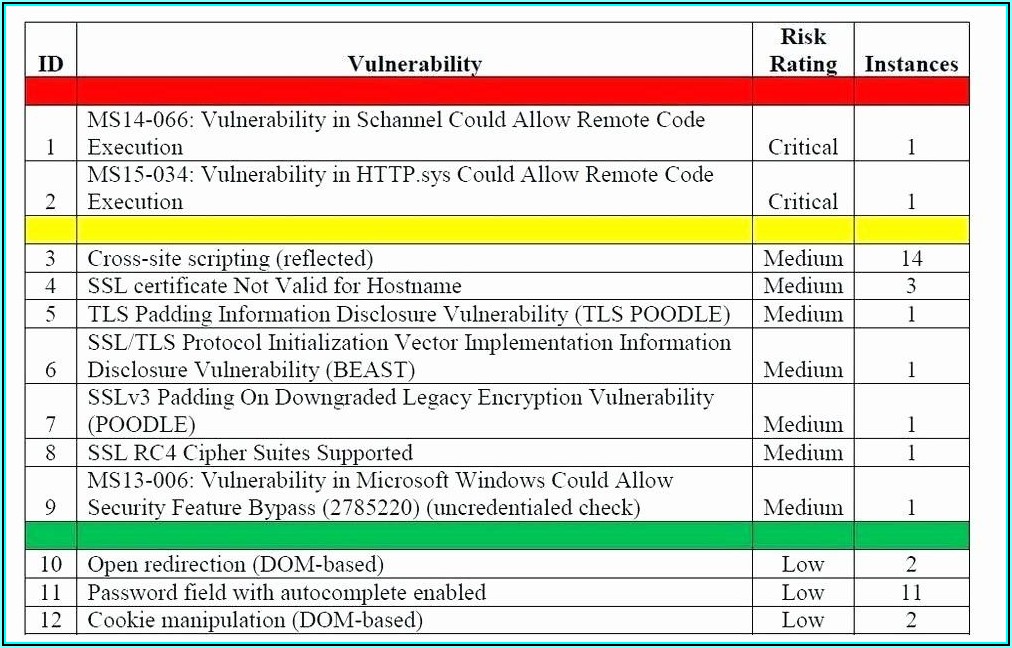
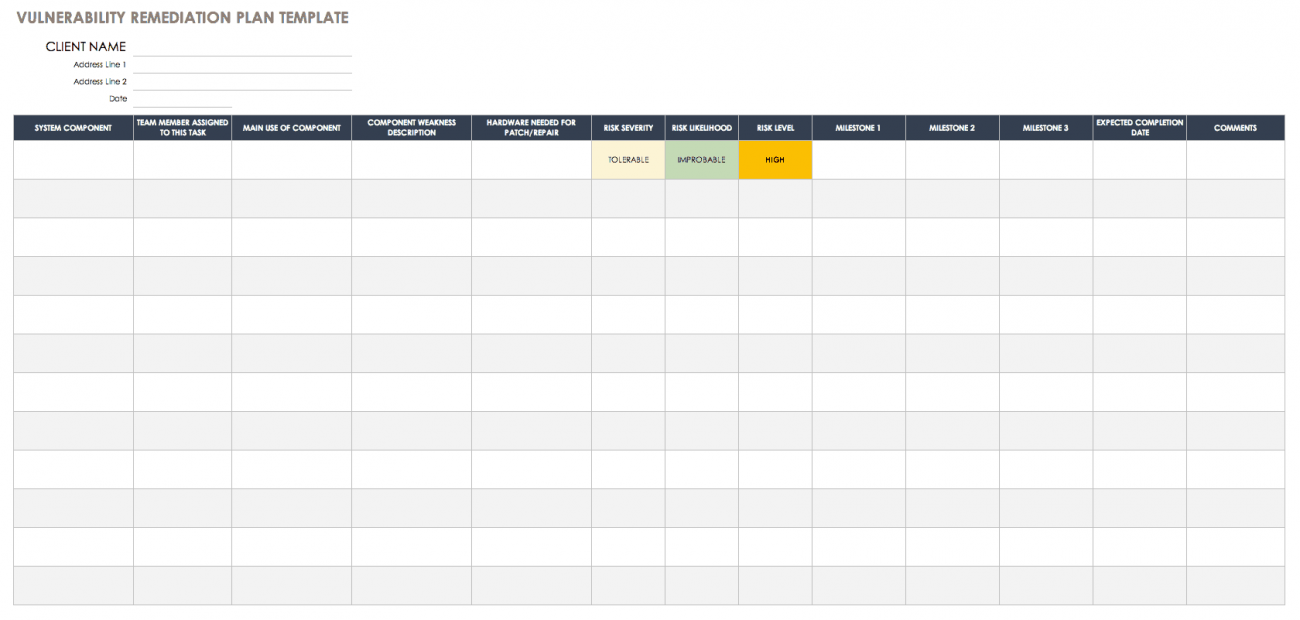
Vulnerability Remediation Plan Template
Vulnerability Remediation Plan Template - Cloud pentestingfree scan today.dark web monitoringpentesting A plan of action to address identified vulnerabilities. Measure the effectiveness of the patch and. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Web it professionals and cybersecurity heads can use these powerpoint slides to represent best practices that should be considered before setting the vulnerability remediation. Web august 31, 2018 | team netspi. 10k+ visitors in the past month Web vulnerability scanning system, on at least a monthly basis. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability • assessing the. This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. Interim mitigation actions to overcome constraints. It establishes a framework for identifying,. Web the remediation plan should include: Cloud pentestingfree scan today.dark web monitoringpentesting A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. It establishes a framework for identifying,. Utilize centralized and continuous scanning technology to identify risk. Steps to vulnerability management are prerequisites for proactive protection. Web august 31, 2018 | team netspi. Interim mitigation actions to overcome constraints. A plan of action to address identified vulnerabilities. Final actions required to remediate. Steps taken to reduce or eliminate a vulnerability. A plan of action to address identified vulnerabilities. Utilize centralized and continuous scanning technology to identify risk. Web the remediation plan should include: A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Web five tips for crafting a cybersecurity risk remediation plan: Units are responsible for ensuring all of their systems are scanned monthly, reviewing the results of the scan, and. Measure the effectiveness of the patch and. Utilize centralized and continuous scanning technology to identify risk. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. 10k+ visitors in the past month Utilize centralized and continuous scanning technology to identify risk. 10k+ visitors in the past month This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Cloud pentestingfree scan today.dark web monitoringpentesting Final actions required to remediate. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Web creating and implementing an vulnerability management policies and procedures is a vital component of any company’s cyber security strategy, and is required by several. Web understanding and managing vulnerabilities is a continuous activity, requiring. This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. Be sure you don’t put [attacks] or [controls] in. Units are responsible for ensuring all of their systems are scanned monthly, reviewing the results of the scan, and. Web vulnerability scanning system, on at least a monthly basis. Steps taken to reduce or eliminate. Steps to vulnerability management are prerequisites for proactive protection of business system security. Web it professionals and cybersecurity heads can use these powerpoint slides to represent best practices that should be considered before setting the vulnerability remediation. Web vulnerability remediation plan template client name date address line 1 address line 2 component weakness description hardware needed. Web understanding and managing. This policy template is meant to supplement the cis. Web vulnerability remediation plan template client name date address line 1 address line 2 component weakness description hardware needed. Web five tips for crafting a cybersecurity risk remediation plan: It establishes a framework for identifying,. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. A plan of action to address identified vulnerabilities. Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability • assessing the. Be sure you don’t put [attacks] or [controls] in. This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. Steps taken to reduce or eliminate a vulnerability. Units are responsible for ensuring all of their systems are scanned monthly, reviewing the results of the scan, and. 10k+ visitors in the past month Web august 31, 2018 | team netspi. Web understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. Steps to vulnerability management are prerequisites for proactive protection of business system security. Web vulnerability patch management template custom tailored plan risk assessment project management weekly & monthly reporting. Interim mitigation actions to overcome constraints. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web guide to effective remediation of network vulnerabilities. Web it professionals and cybersecurity heads can use these powerpoint slides to represent best practices that should be considered before setting the vulnerability remediation. Cloud pentestingfree scan today.dark web monitoringpentesting Web creating and implementing an vulnerability management policies and procedures is a vital component of any company’s cyber security strategy, and is required by several. This policy template is meant to supplement the cis. Web five tips for crafting a cybersecurity risk remediation plan:ICVulnerabilityRemediationPlanTemplate_Google.xltx Google Sheets
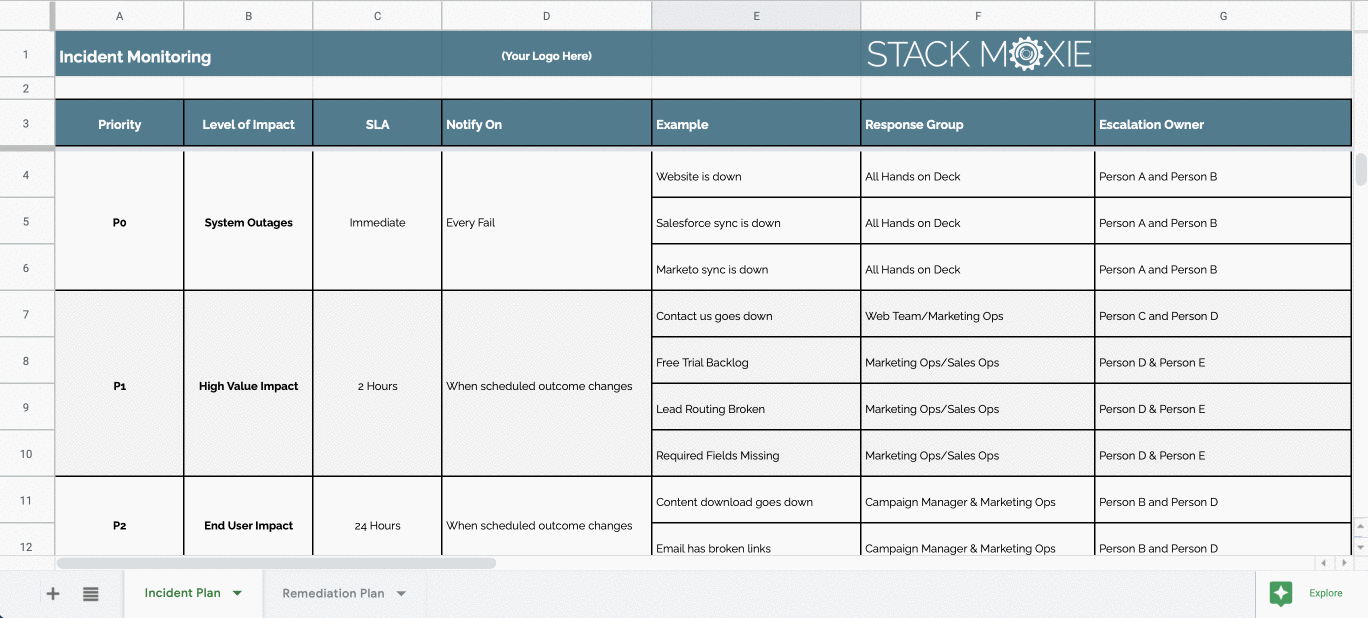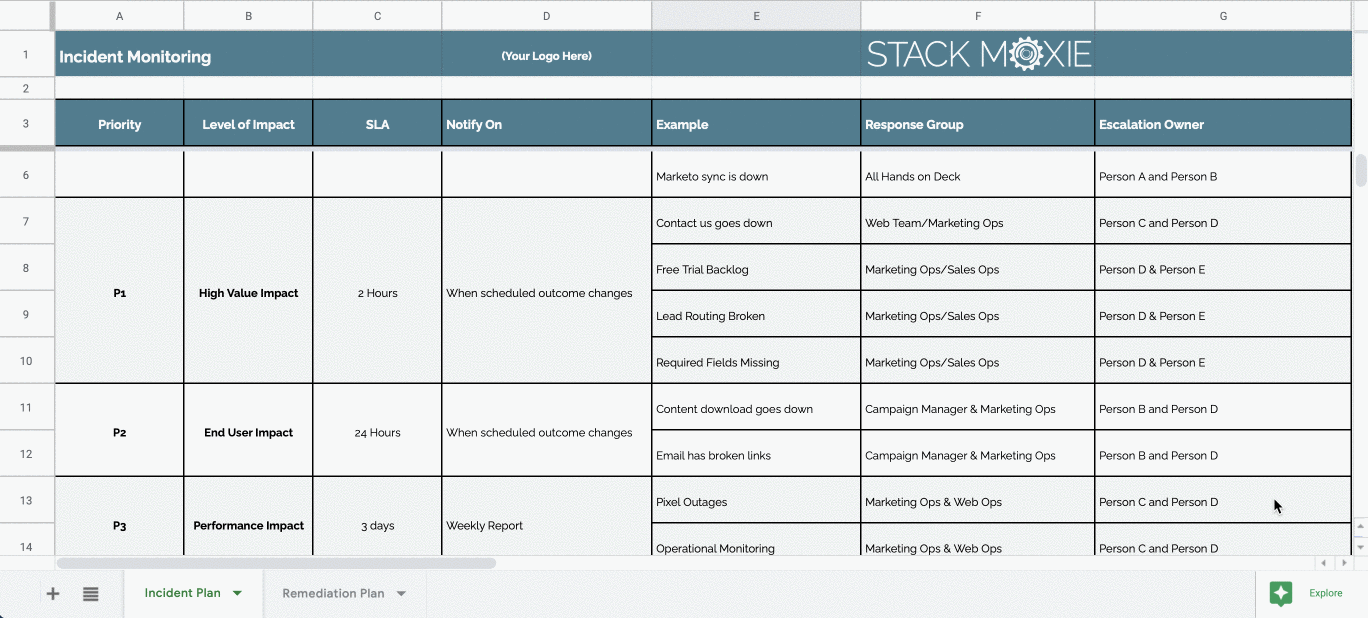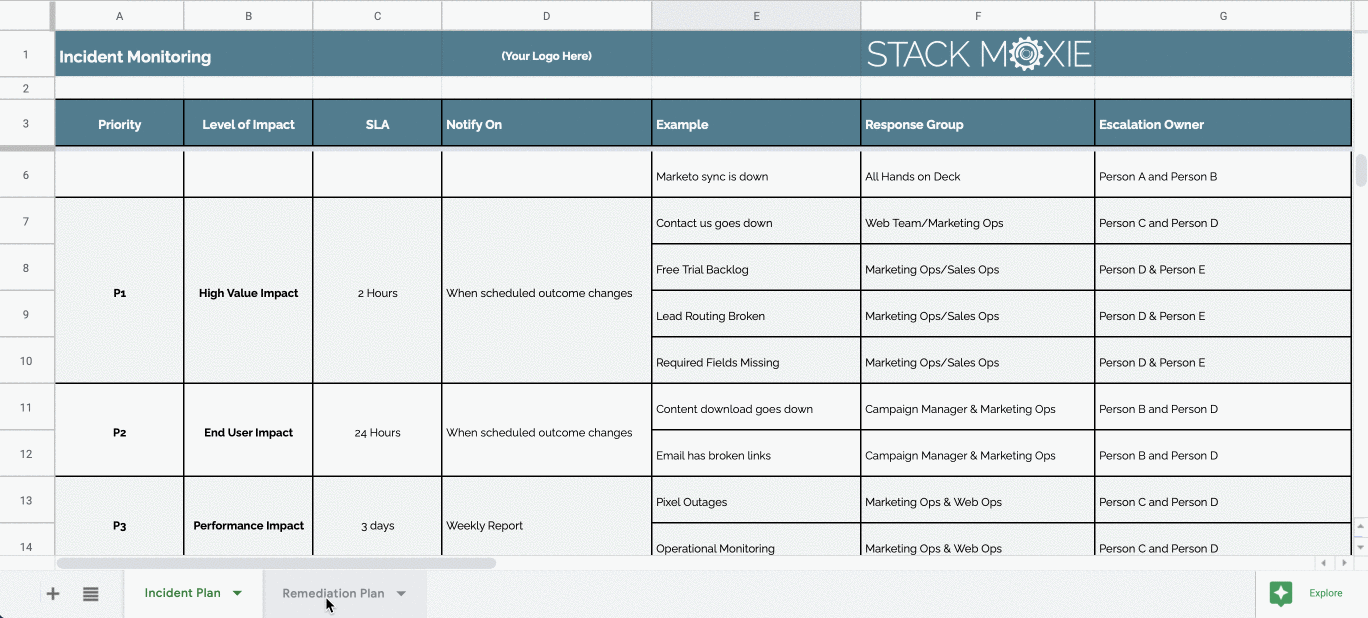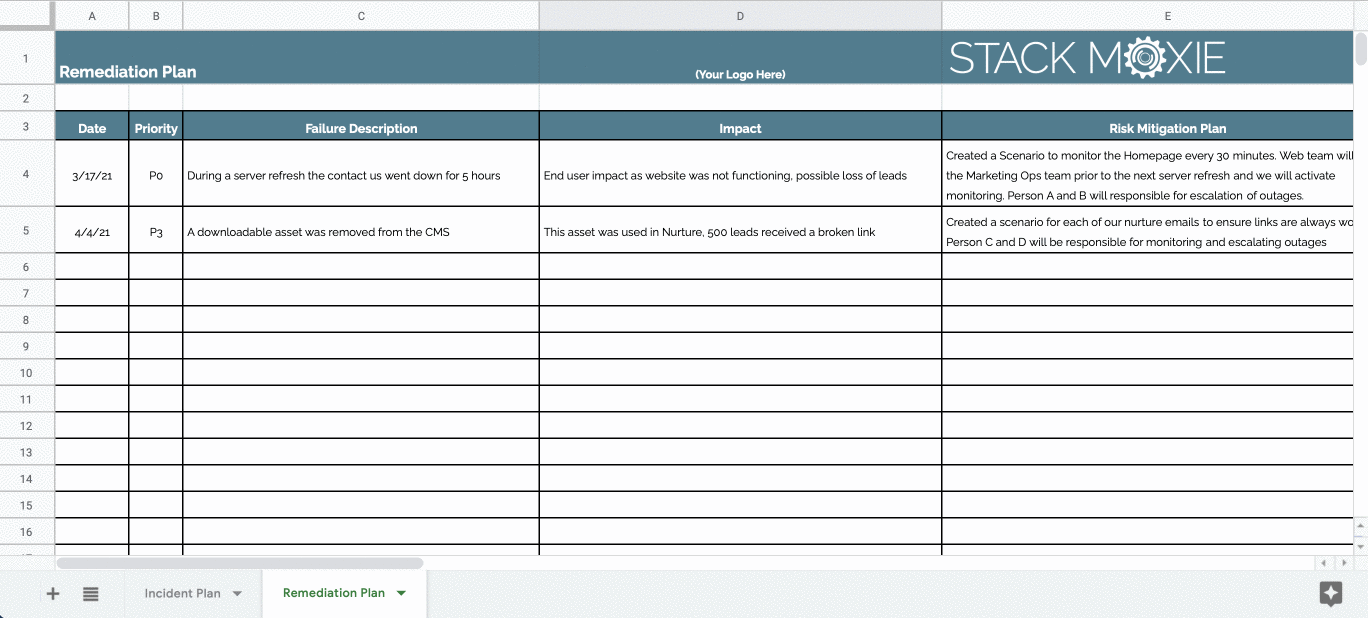
Incident & Remediation Plan Template for managing critical errors and
Vulnerability Remediation PowerPoint Template PPT Slides
Free Vulnerability Assessment Plan Template Google Docs, Word, Apple
Simplify Vulnerability Management with Nexpose 5.6
Vulnerability Assessment Flow Chart (Adapted from the US DOE 2002
Vulnerability Remediation Plan Template Flyer Template
What is a Vulnerability Assessment? Panda Security
Vulnerability Assessment And Testing Plan Templates
Free Vulnerability Assessment Templates Smartsheet
Related Post: