Vulnerability Management Template
Vulnerability Management Template - It systematically identifies, assesses and mitigates potential. This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. Web sans cybersecurity leadership. The nist framework is meant as an overarching cyber strategy, but its process of identify, protect, detect, respond,. Ad learn how businesses defend against threats with mdr for microsoft 365. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. The process areas described include • developing a. Web free vulnerability management policy template. Vulnerability scans (common) — tenable recommends using vulnerability scan. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web tenable vulnerability management and tenable security center enable security teams to focus on the vulnerabilities and assets, which matter most to the. Helping you identify, classify, remediate, and mitigate vulnerabilities—before attackers do. Focus areas are the topics or areas of security that. Cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Vulnerability scans (common) — tenable recommends using vulnerability scan. Vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. Web sans cybersecurity leadership. Define clear examples of your focus areas. Empower your team with huntress mdr. Web framework for vulnerability management. Ad learn how businesses defend against threats with mdr for microsoft 365. The purpose of the (company) vulnerability management policy is to establish the rules for the review, evaluation,. Stay current with free resources focused on vulnerability management. It establishes a framework for identifying,. The process areas described include • developing a. The nist framework is meant as an overarching cyber strategy, but its process of identify, protect, detect, respond,. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Web this document provides guidance on creating a security patch and vulnerability management. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Web vulnerability management is a proactive strategy to protect network assets against cyber threats. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. This standard supports and supplements fsu technology. Cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. It establishes a framework for identifying,. Web sans cybersecurity leadership. The purpose of the (company) vulnerability management policy is to establish the rules for the review, evaluation,. Ad learn how businesses defend against threats with mdr for microsoft 365. Read this ebook to help you build trust and loyalty with customers and employees. Vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. Helping you identify, classify, remediate, and mitigate vulnerabilities—before attackers do. It establishes a framework for identifying,. As both an example and a starting point, esecurity planet has developed a. Define clear examples of your focus areas. Vulnerability scans (common) — tenable recommends using vulnerability scan. Web tenable vulnerability management and tenable security center enable security teams to focus on the vulnerabilities and assets, which matter most to the. Empower your team with huntress mdr. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. The nist framework is meant as an overarching cyber strategy, but its process of identify, protect, detect, respond,. The purpose of the (company) vulnerability management policy is to establish the rules for the review, evaluation,. Web framework for vulnerability management. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web vulnerability management. Access 24/7 experts for managed detection & response. Vulnerabilities occur through product defects, misconfigurations, or. Web sans cybersecurity leadership. Empower your team with huntress mdr. Web vulnerability management policy template. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. Web sans cybersecurity leadership. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Stay current with free resources focused on vulnerability management. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Security vulnerabilities enable attackers to compromise a resource or data. Define clear examples of your focus areas. Web framework for vulnerability management. Access 24/7 experts for managed detection & response. Web tenable vulnerability management and tenable security center enable security teams to focus on the vulnerabilities and assets, which matter most to the. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. It systematically identifies, assesses and mitigates potential. This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web free vulnerability management policy template. Read this ebook to help you build trust and loyalty with customers and employees. Empower your team with huntress mdr. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. The purpose of the (company) vulnerability management policy is to establish the rules for the review, evaluation,.Vulnerability Management Template pack from ControlCase
Vulnerability Management PowerPoint Template SketchBubble
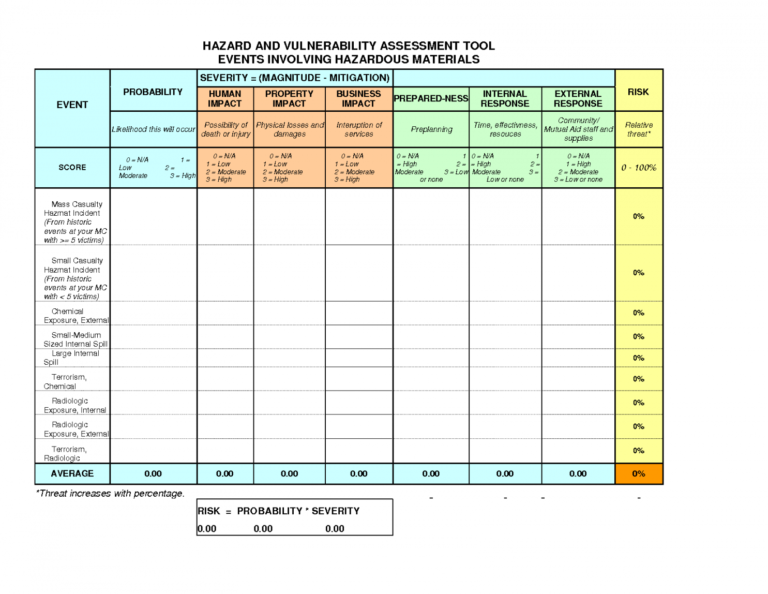
Sample Hazard Vulnerability Analysis Analysis, Vulnerability
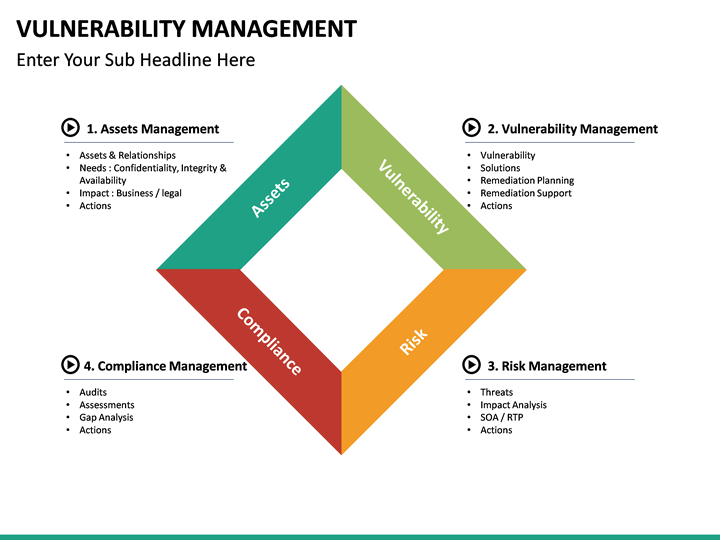
Creating a Vulnerability Management Strategy Dr. Erdal Ozkaya
Editable Updated Guidelines For Fast Systems In Hazard Assessment
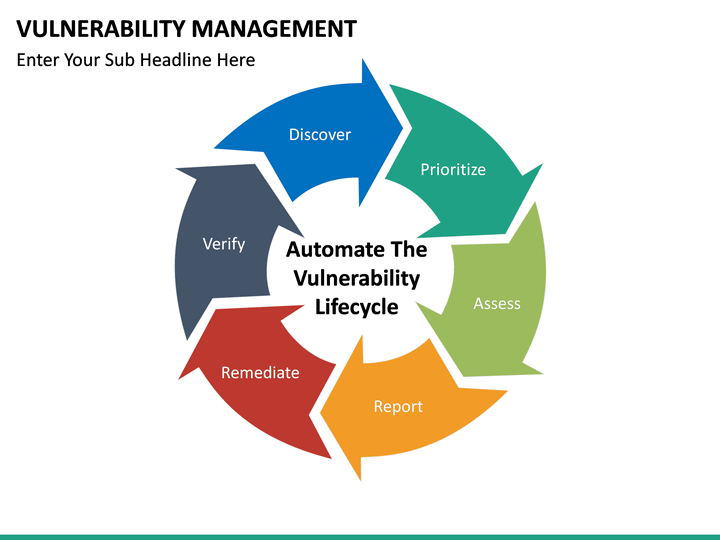
The Five Stages of Vulnerability Management
Fresh Vulnerability Management Program Template Sparklingstemware
Vulnerability Assessment Flow Chart (Adapted from the US DOE 2002
Free Vulnerability Assessment Templates Smartsheet
Vulnerability Management PowerPoint Template SketchBubble
Related Post: