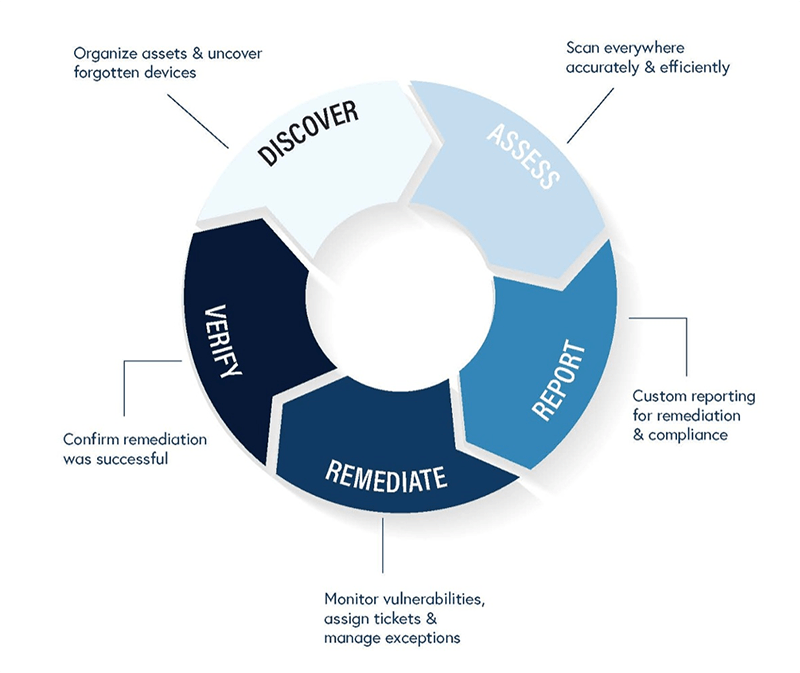
Vulnerability Management Process Template
Vulnerability Management Process Template - Review and update documentation annually, or. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Advanced protection for windows operating system. Learn how taegis™ vdr delivers impact throughout each part of the vm process. Smooth and simple sign up. The process starts with asset. Web vulnerability management vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. Be sure you don’t put [attacks] or [controls] in. Web the vulnerability management team coordinates patches fixing vulnerabilities in maintained stable branches (corresponding to previous major releases). A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Web 4 steps of a vulnerability management program. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Ad our security scanner will help you keep up with the. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Web vulnerability management policy template. Ad purchase your vulnerability and patch management solution today. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. A tool used to evaluate the severity,. The process areas described include • developing a. An automated tool used to detect security weaknesses in a system or network. The scan consists of four stages: Create and maintain a documented vulnerability management process for enterprise assets. Learn how taegis™ vdr delivers impact throughout each part of the vm process. Smooth and simple sign up. A tool used to evaluate the severity,. Create and maintain a documented vulnerability management process for enterprise assets. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Perform vulnerability scan at the heart of a typical vulnerability management tool is a vulnerability scanner. Learn how taegis™ vdr delivers impact throughout each part of the vm process. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. All modern software contains vulnerabilities; A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Learn how taegis™ vdr. Be sure you don’t put [attacks] or [controls] in. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. The process starts with asset. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Web vulnerability management is a continuous, proactive, and often automated. Web vulnerability management vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. Web 4 steps of a vulnerability management program. The process areas described include • developing a. Web 7.1 establish and maintain a vulnerability management process: Perform vulnerability scan at the heart of a typical vulnerability management tool is a vulnerability. Web the vulnerability management team coordinates patches fixing vulnerabilities in maintained stable branches (corresponding to previous major releases). The process starts with asset. Ad taegis™ vdr provides a complete vm solution eliminating the need for multiple vm products. Create and maintain a documented vulnerability management process for enterprise assets. Ad taegis™ vdr provides a complete vm solution eliminating the need. Perform vulnerability scan at the heart of a typical vulnerability management tool is a vulnerability scanner. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. An automated tool used to detect security weaknesses in a system or network. Web 4 steps of a vulnerability management program. A vulnerability. The process starts with asset. Review and update documentation annually, or. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Be sure you don’t put [attacks] or [controls] in. Perform vulnerability scan at the heart of a typical vulnerability management tool is a vulnerability scanner. Ad taegis™ vdr provides a complete vm solution eliminating the need for multiple vm products. The process starts with asset. Web vulnerability management vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. An automated tool used to detect security weaknesses in a system or network. Industry leading pricing for application scanner platform. Web 4 steps of a vulnerability management program. A tool used to evaluate the severity,. Learn how taegis™ vdr delivers impact throughout each part of the vm process. A vulnerability scanner automates the vulnerability management process, typically breaking it down into the following four. Web vulnerability management policy template. Ad taegis™ vdr provides a complete vm solution eliminating the need for multiple vm products. Web vulnerability management guidance to help organisations assess and prioritise vulnerabilities. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. The scan consists of four stages: The process areas described include • developing a. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Ad purchase your vulnerability and patch management solution today.Figure 10 Vulnerability Assessment Flow Chart (Adapted from the US DOE
Vulnerability Assessment and Testing Services Cloud4C
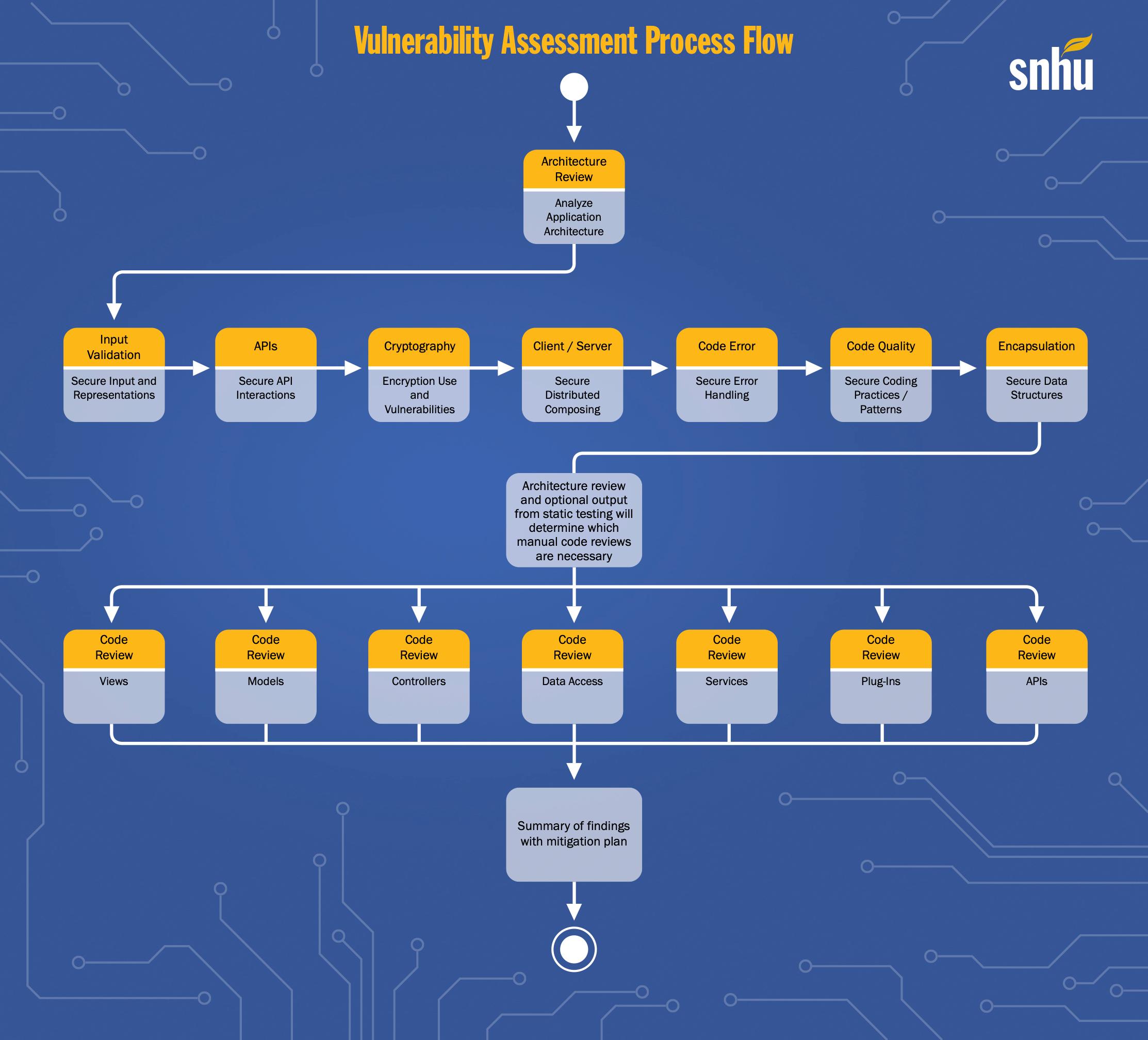
Vulnerability Assessment Process Flow snhu Architecture Review Analyze
Creating a Vulnerability Management Strategy zSecurity
Vulnerability Assessment Lanworks
What Is Vulnerability Management? Get the Answers You Need
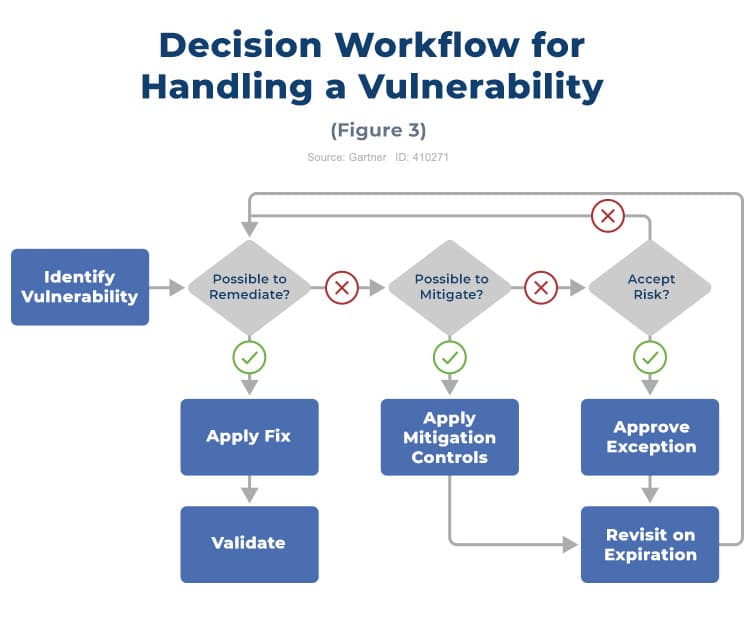
Vulnerability Management Process Flow Chart Rootshell
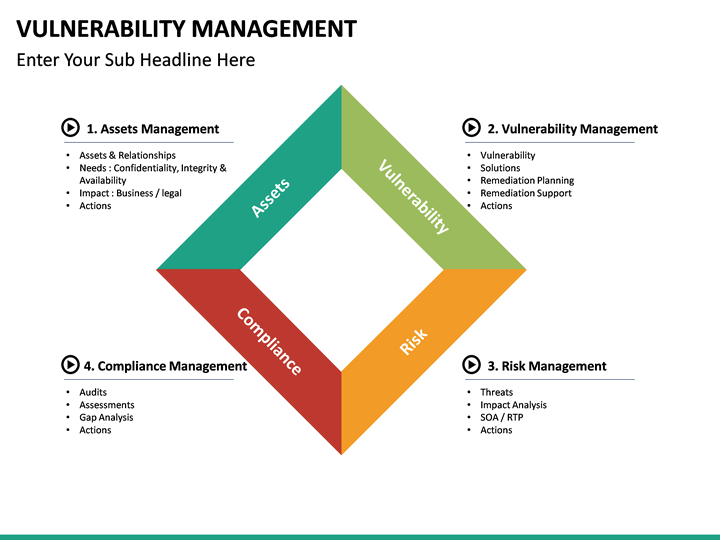
Vulnerability Management PowerPoint Template SketchBubble
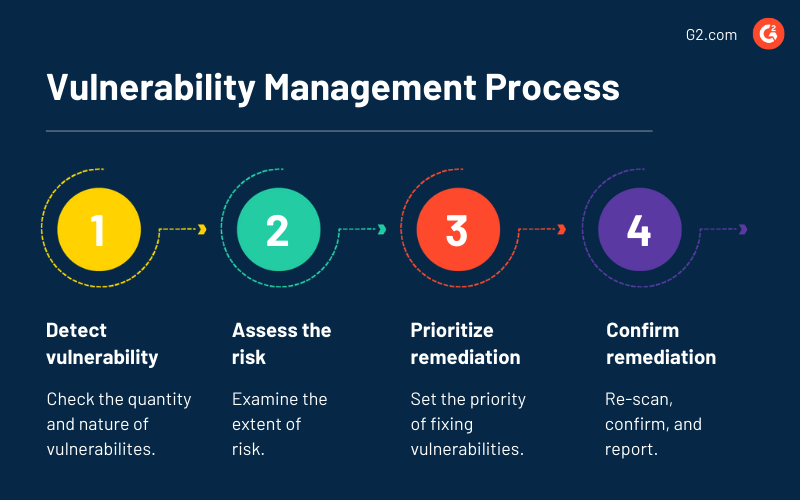
The Five Stages of Vulnerability Management
The Basics of Vulnerability Management
Related Post: