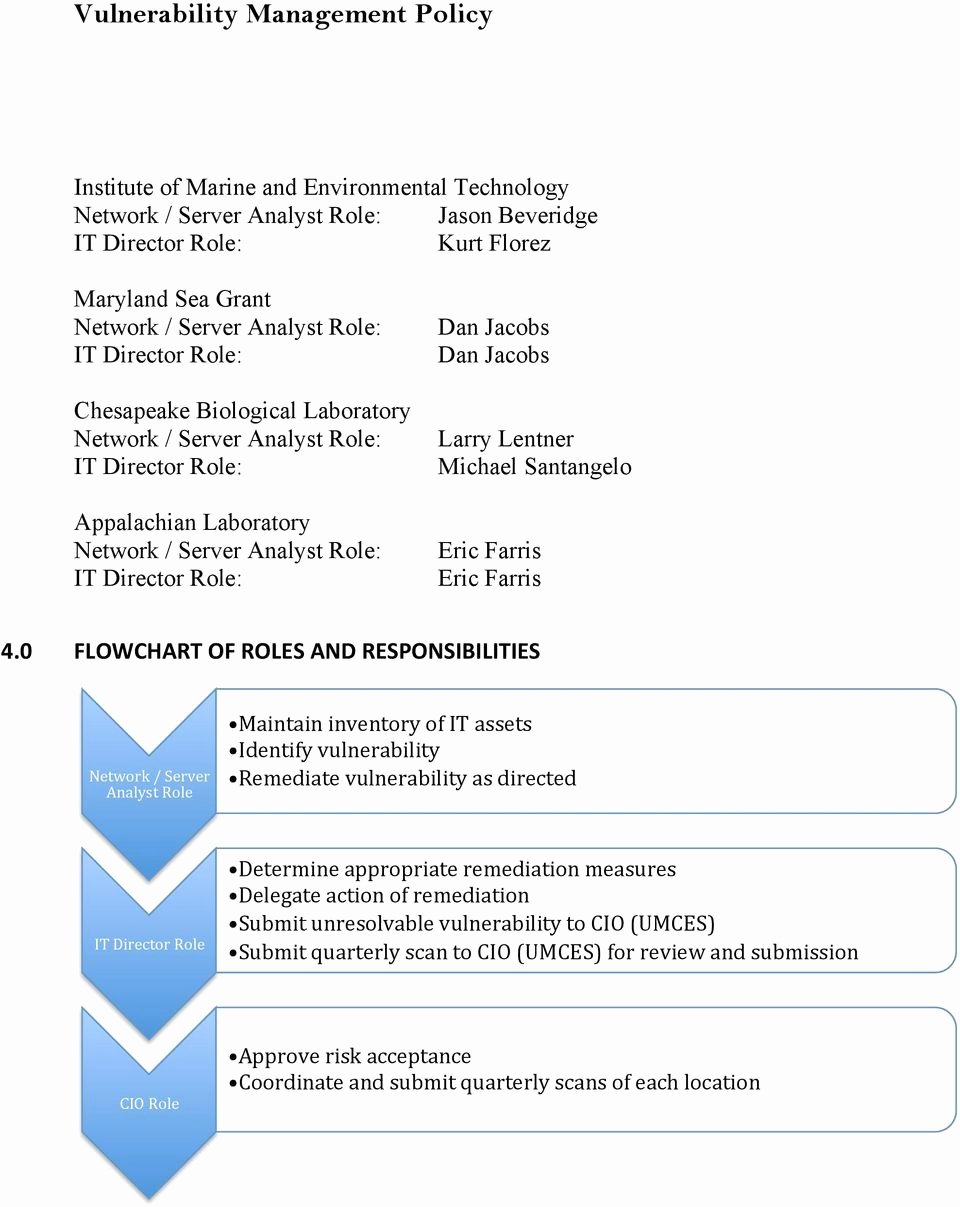
Vulnerability Management Plan Template
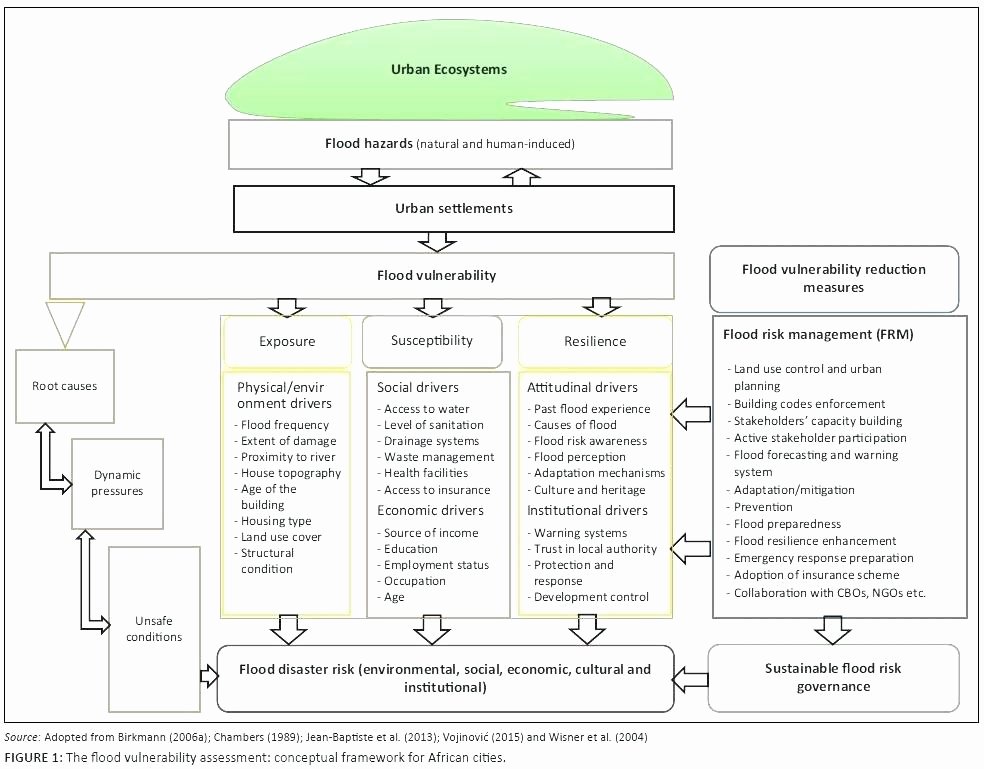
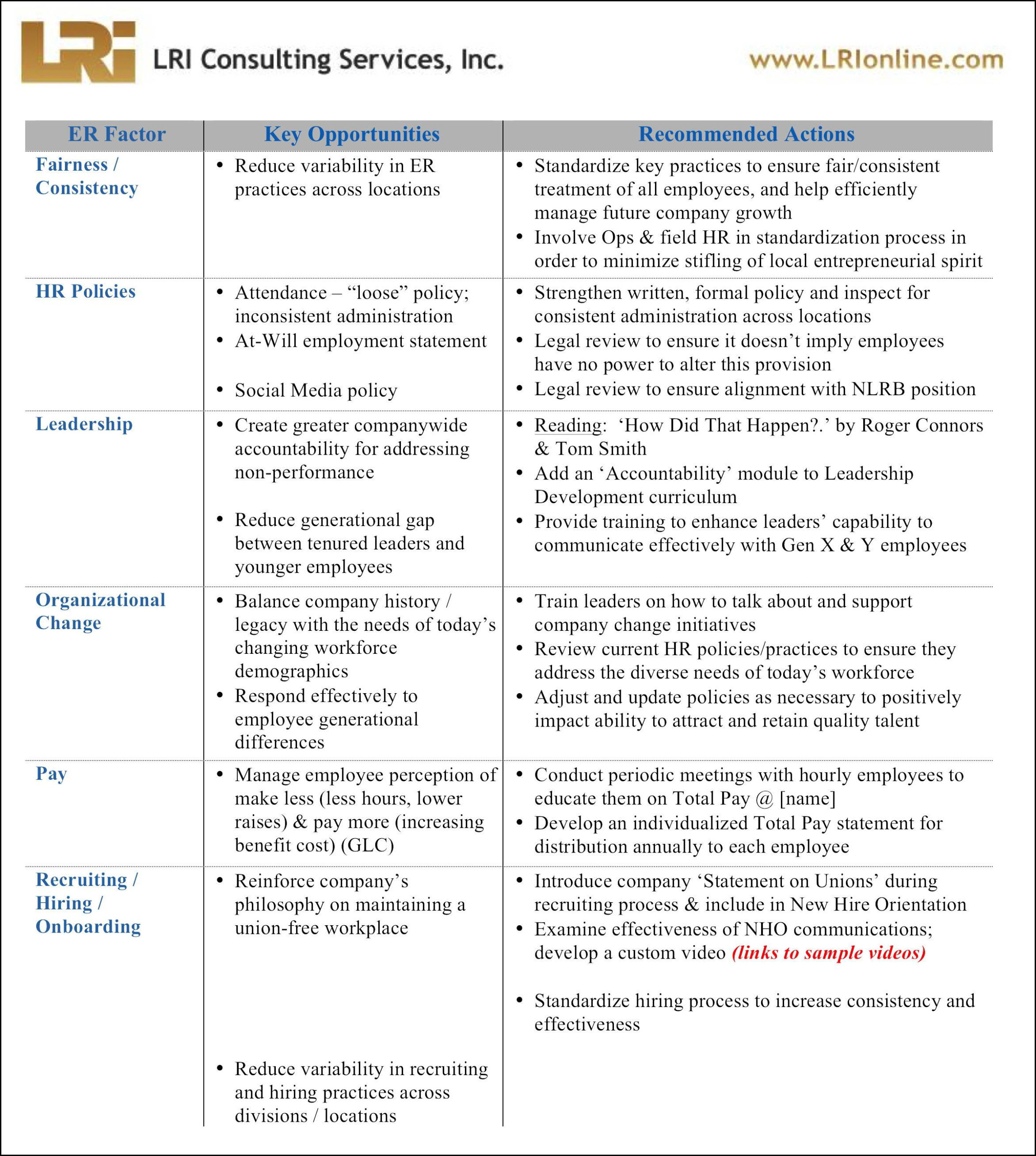
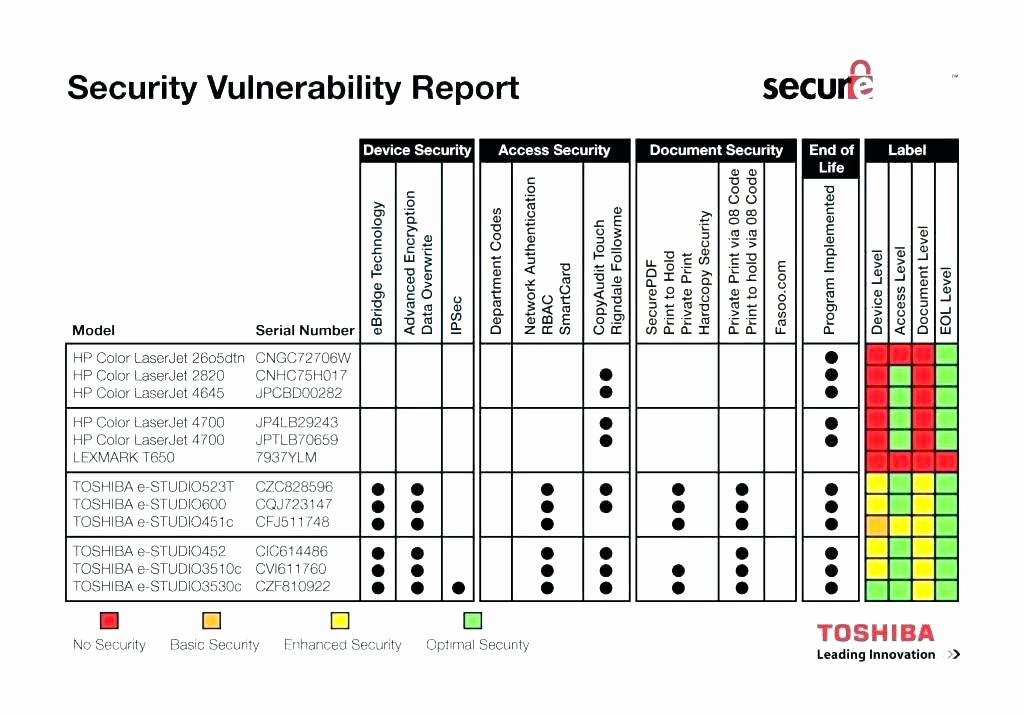
Vulnerability Management Plan Template - This guide gives the correlation between 49 of. Vulnerabilities occur through product defects,. Web download our free vulnerability management policy template now. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Free scan today.cloud pentestingdark web monitoringpentesting While we strive to keep the information up to date and correct, we. Helping you identify, classify, remediate, and mitigate vulnerabilities—before attackers do. Security vulnerabilities enable attackers to compromise a resource or data. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Web download our free vulnerability management policy template now. This standard supports and supplements fsu technology policies and provides additional security and privacy best practices. It establishes a framework for identifying,. Web vulnerability management policy template. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security. It establishes a framework for identifying,. The process areas described include • developing a. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Web develop a. Security vulnerabilities enable attackers to compromise a resource or data. 10k+ visitors in the past month While we strive to keep the information up to date and correct, we. Go to reports > compliance templates. On the left navigation pane, click nist csf. 10k+ visitors in the past month It establishes a framework for identifying,. The process areas described include • developing a. Vulnerabilities occur through product defects,. This policy template is meant to supplement the cis. This guide gives the correlation between 49 of. Use the dod vulnerability management process to manage and respond to vulnerabilities identified in all software, firmware, and hardware within the dodin. This policy template is meant to supplement the cis. A vulnerability management policy defines an approach for vulnerability management to reduce system risks and. Web this document provides guidance on. While we strive to keep the information up to date and correct, we. Vulnerabilities occur through product defects,. It establishes a framework for identifying,. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Helping you identify, classify, remediate, and mitigate vulnerabilities—before attackers do. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. The purpose of the (company) vulnerability management. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). This paper outlines how organizational. Web download our free vulnerability management policy template now. This policy template is meant to supplement the cis. Vulnerabilities occur through product defects,. Web any articles, templates, or information provided by smartsheet on the website are for reference only. Web vulnerability management policy template. Vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. 10k+ visitors in the past month It establishes a framework for identifying,. Security vulnerabilities enable attackers to compromise a resource or data. Web download our free vulnerability management policy template now. Vulnerabilities occur through product defects,. It establishes a framework for identifying,. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. Web download our free vulnerability management policy template now. Web understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. Web this paper examines the critical role of. While we strive to keep the information up to date and correct, we. Web any articles, templates, or information provided by smartsheet on the website are for reference only. This policy template is meant to supplement the cis. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Security vulnerabilities enable attackers to compromise a resource or data. The process areas described include • developing a. Go to reports > compliance templates. Web this paper examines the critical role of project management in building a successful vulnerability management program. This paper outlines how organizational. Helping you identify, classify, remediate, and mitigate vulnerabilities—before attackers do. Vulnerabilities occur through product defects,. Vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. Web download our free vulnerability management policy template now. Web vulnerability management policy template. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security. Free scan today.cloud pentestingdark web monitoringpentesting 10k+ visitors in the past month Use the dod vulnerability management process to manage and respond to vulnerabilities identified in all software, firmware, and hardware within the dodin. Web understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. This guide gives the correlation between 49 of.Vulnerability Assessment Flow Chart (Adapted from the US DOE 2002
Vulnerability Management Program Template Stcharleschill Template
Free Vulnerability Assessment Templates Smartsheet
Vulnerability Management Program Template Stcharleschill Template
Fresh Vulnerability Management Program Template Sparklingstemware
Vulnerability Management Program Template Stcharleschill Template
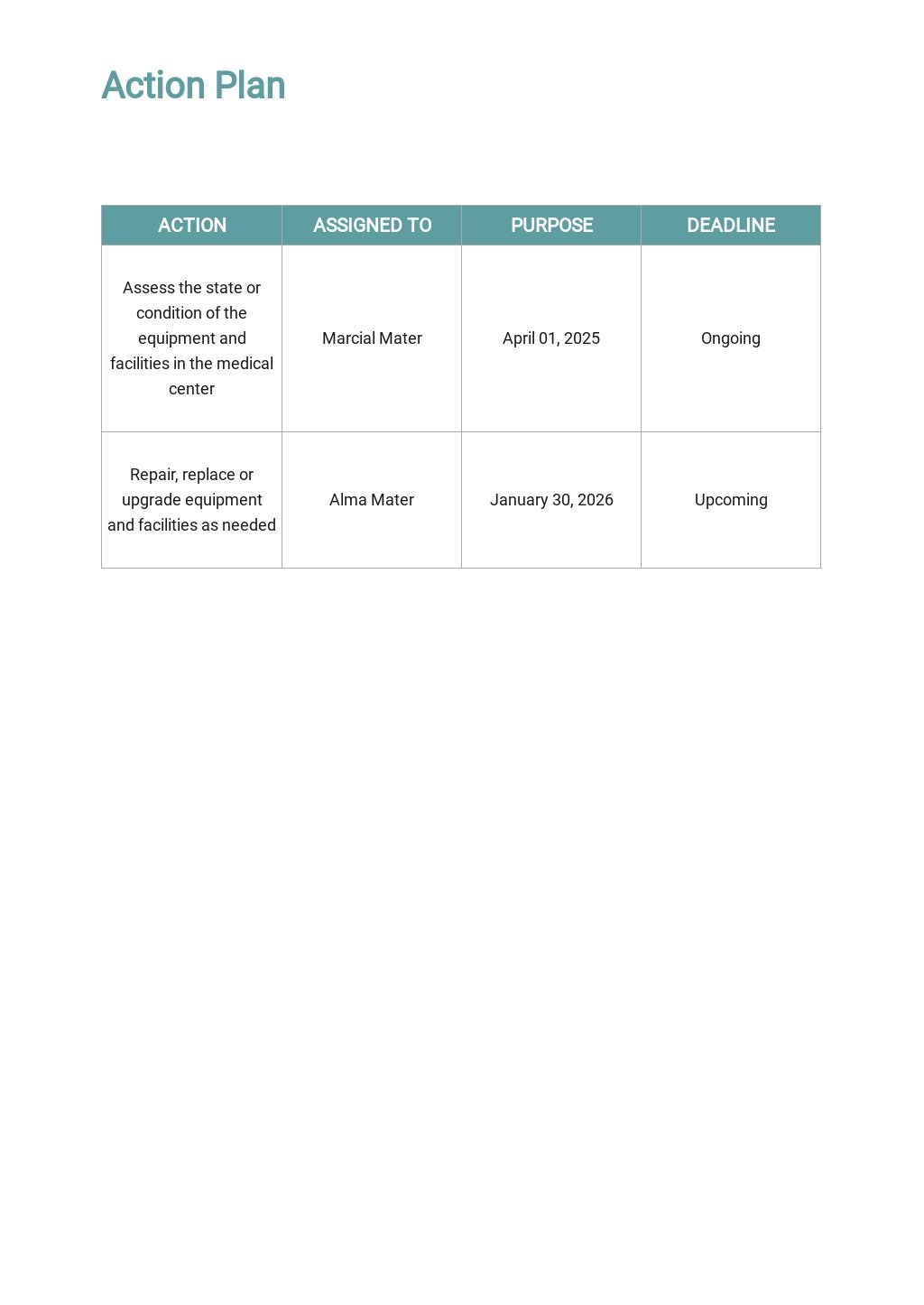
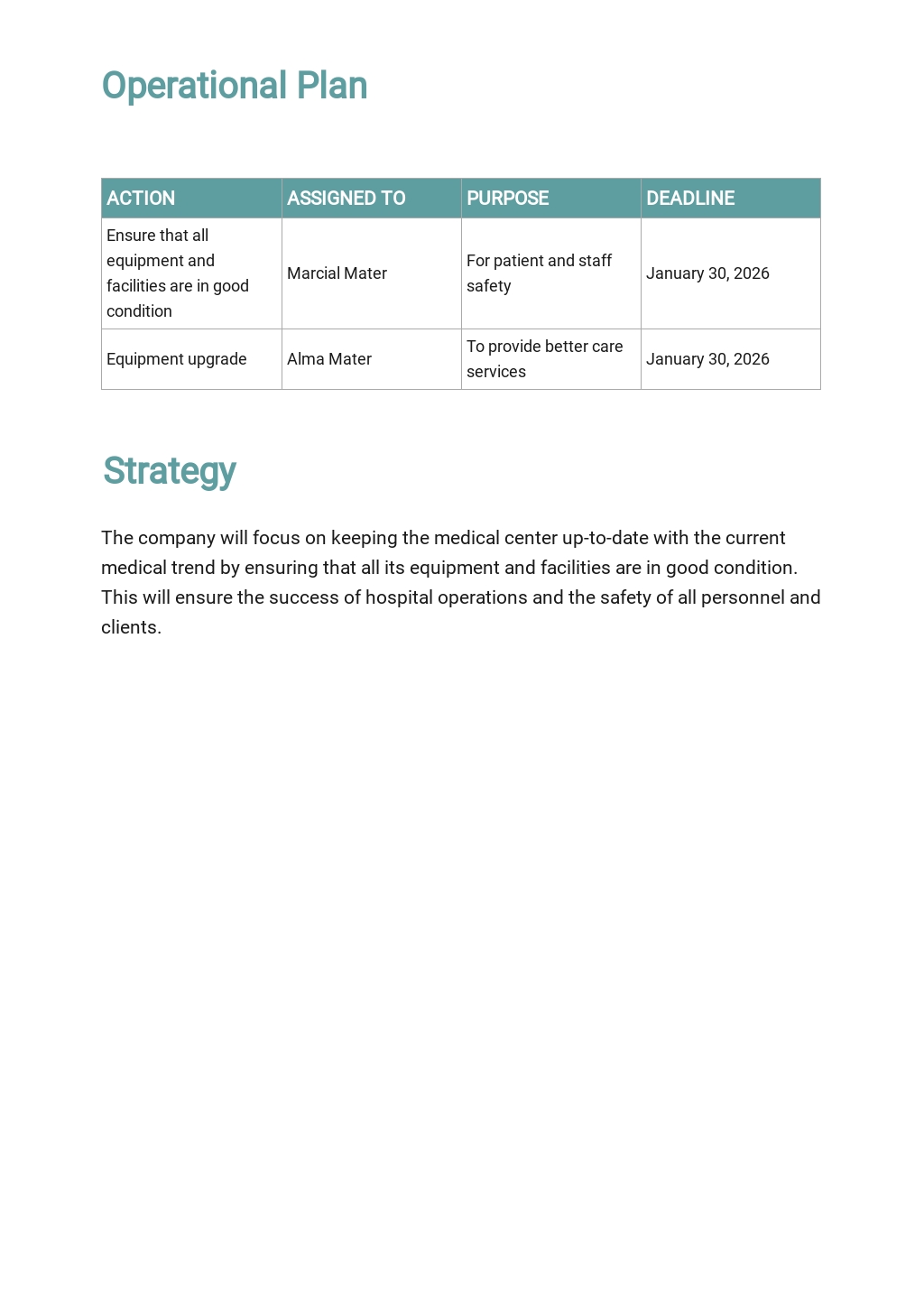
Free Vulnerability Assessment Plan Template Google Docs, Word, Apple
Creating a Vulnerability Management Strategy Dr. Erdal Ozkaya
Free Vulnerability Assessment Plan Template Google Docs, Word, Apple
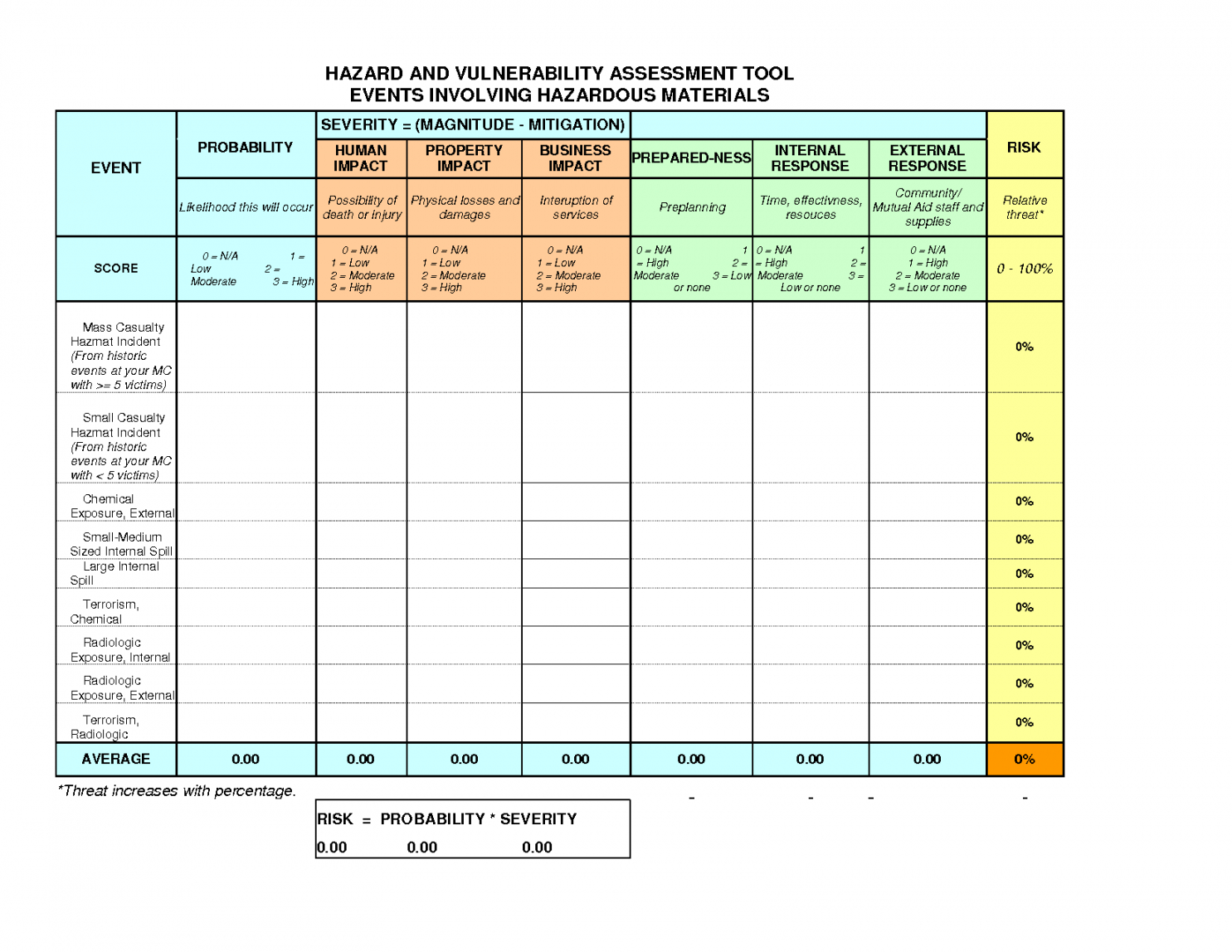
Editable Updated Guidelines For Fast Systems In Hazard Assessment
Related Post: