Threat Report Template
Threat Report Template - Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. (ii) result in major damage to organizational assets; Instead, the assessment is intended as an Web template section the threat modeling tool team is constantly working to improve tool functionality and experience. Its purpose is to guide you during the investigations and to report. (i) cause a severe degradation in or loss of mission capability to an extent and duration that the organization is not able to perform one or more of its primary functions; Or (iv) result in severe. It delineates the essential components that must be. Powered by huntress' 24/7 expert security operations center. Ad learn how businesses defend against threats with mdr for microsoft 365. Powered by huntress' 24/7 expert security operations center. Countermeasures (fouo) 2023 edition appendix c: Ad industry leading cybersecurity protection for your data and devices. More industry insider threat information and resources. Web do not copy information from the security report example you downloaded. Web do not copy information from the security report example you downloaded. Web a threat hunting report template serves as a roadmap for crafting structured, insightful reports. Web threat modeling cheat sheet¶ introduction¶ threat modeling is a structured approach of identifying and prioritizing potential threats to a system, and determining the value that potential mitigations would have in reducing or. Web cyberthreat reports can help bridge that gap. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Its purpose is to guide you during the investigations and to report. Please click on the nittf technical page to review these. (ii) result in major damage to organizational. Web do not copy information from the security report example you downloaded. More industry insider threat information and resources. Note that a cyber risk assessment is not a meant to be conducted just once. Web defender for cloud has three types of threat reports, which can vary according to the attack. Its purpose is to guide you during the investigations. Web a threat hunting report template serves as a roadmap for crafting structured, insightful reports. (iii) result in major financial loss; Ad industry leading cybersecurity protection for your data and devices. Powered by huntress' 24/7 expert security operations center. Web template section the threat modeling tool team is constantly working to improve tool functionality and experience. Web a threat hunting report template serves as a roadmap for crafting structured, insightful reports. Powered by huntress' 24/7 expert security operations center. Ad learn how businesses defend against threats with mdr for microsoft 365. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Or (iv). (i) cause a severe degradation in or loss of mission capability to an extent and duration that the organization is not able to perform one or more of its primary functions; (iii) result in major financial loss; Web a threat hunting report template serves as a roadmap for crafting structured, insightful reports. Use threats, vulnerabilities, likelihoods, and impacts to determine. A few minor changes might take place over. Web template section the threat modeling tool team is constantly working to improve tool functionality and experience. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web this template leverages several models in the cyber threat intelligence domain. Or (iv) result in severe. Instead, the assessment is intended as an More industry insider threat information and resources. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web this template leverages several models in the cyber threat intelligence domain (such as the intrusion kill chain,. Countermeasures (fouo) 2023 edition appendix c: Note that a cyber risk assessment is not a meant to be conducted just once. Web the goal of a vulnerability assessment report is to highlight threats to an organization’s security posed by vulnerabilities in its it environment. More industry insider threat information and resources. Web a severe or catastrophic adverse effect means that,. Web do not copy information from the security report example you downloaded. Countermeasures (fouo) 2023 edition appendix c: It delineates the essential components that must be. Use threats, vulnerabilities, likelihoods, and impacts to determine risk 8 risk is a guide when formulating an incident response plan, however, it is not the final state of an organization’s cyber posture. (ii) result in major damage to organizational assets; Ad industry leading cybersecurity protection for your data and devices. (iii) result in major financial loss; Note that a cyber risk assessment is not a meant to be conducted just once. Web download a cybersecurity risk assessment report template for microsoft word | google docs. Web key components of a threat hunting report template: Web template section the threat modeling tool team is constantly working to improve tool functionality and experience. This cybersecurity risk assessment report template includes everything you need to assess cybersecurity threats and. In this blog post, we'll discuss how to create an. Web cyberthreat reports can help bridge that gap. Web a threat hunting report template serves as a roadmap for crafting structured, insightful reports. Instead, the assessment is intended as an Please click on the nittf technical page to review these. Powered by huntress' 24/7 expert security operations center. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. More industry insider threat information and resources.FREE 10+ Sample Threat Assessments in PDF M Word
Threat Assessment Report Template
Threat Assessment Report Template PROFESSIONAL TEMPLATES
Security Threat Assessment Templates At With Regard To Threat
Bomb Threat Report form (Free and editable template)
10+ Security Risk Assessment Templates Free Samples, Examples
Free Cyber Security Intelligence And Threat Report
Insider Threat Report SC Report Template Tenable®
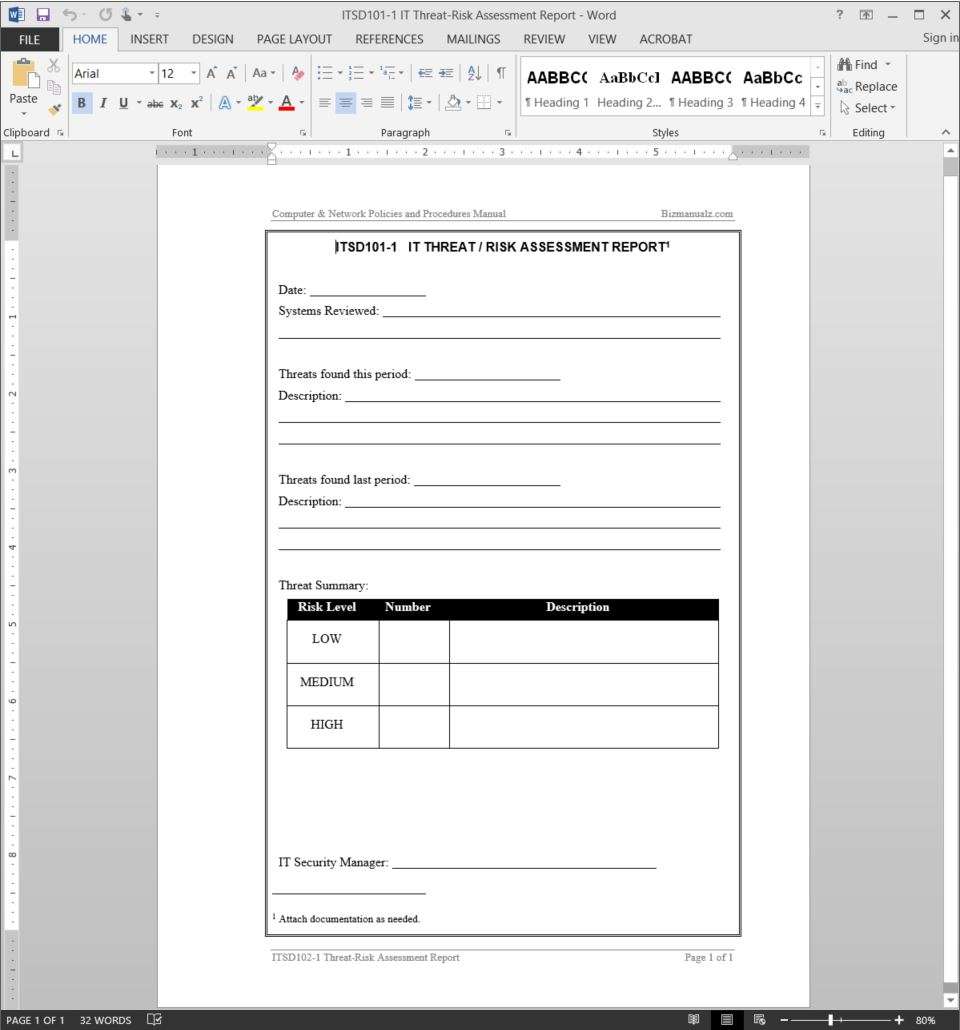
IT Threat Risk Assessment Report Template
Free 4+ Restaurant Risk Assessment Forms In Pdf Doc In Threat
Related Post: