Threat Model Template
Threat Model Template - Web ms threat modeling tool stencils. As a result, it greatly reduces the total cost of development. Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an application, a host, a system, or an environment. Want to create a swot analysis or wish to highlight threats to your business or venture? Use our technology powerpoint templates to give them an. It can be used for categorising threats using stride, linddun and cia. Threat modeling is a core element of the microsoft security development lifecycle (sdl). Threatware parses threat models using a scheme file that describes the format of the threat model. Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Web find 45 different ways to say make threat, along with antonyms, related words, and example sentences at thesaurus.com. One is to identify a threat and the centre of origin, second being the seriousness of the threat identified and third, devising an intervention plan in order to nip the threat in the bud. The key areas of focus for the tool is: Propose risk mitigation plan step 6: Identify and assign potential threats from stride applicability matrix step 4:. Download them for free in ai or eps format. As a result, it greatly reduces the total cost of development. Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an application, a host, a system, or an environment. One is. Web choose from 71 printable design templates, like threat posters, flyers, mockups, invitation cards, business cards, brochure,etc. Identify and assign potential threats from stride applicability matrix step 4: With these expertly crafted slide designs you can create amazing 3d swot analysis diagrams, as well as highlight the strengths, weaknesses. Generic threat modeling threats can that of stride or another methodology.. Web 05.08.2021 / mikhail rusakovich. Identify and assign potential threats from stride applicability matrix step 4: A threat model is a structured representation of all the information that affects the security of an application. You must select which template to use before creating a model. As a result, it greatly reduces the total cost of development. Want to create a swot analysis or wish to highlight threats to your business or venture? In the top right corner of the template editor, you will find an orange button labeled 'update threat model.' click on this button to. Web to enable threatware to help threat models should be created from a threat model template which has a format. Generic threat modeling elements are: This cheat sheet aims to provide guidance on how to create threat models for both existing systems or applications as well as new systems. Generic threat modeling threats can that of stride or another methodology. Web find 45 different ways to say make threat, along with antonyms, related words, and example sentences at thesaurus.com. Locate. Web draw ahead of others with our secure your data from threats powerpoint templates ppt backgrounds for slides. Create an architecture diagram and label the artifacts step 2: These threat analysis powerpoint templates are just what you need. Identify appropriate security controls from nist csf Web 05.08.2021 / mikhail rusakovich. Today i would like to share how to personalize the template and produced the toolbar skilled for. Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an application, a host, a system, or an environment. Threat modeling works to identify,. The key areas of focus for the tool is: Web to enable threatware to help threat models should be created from a threat model template which has a format that threatware can parse. Let your inner brilliance come to the surface. As a result, it greatly reduces the total cost of development. Identify appropriate security controls from nist csf Threat modeling looks at a system from a potential attacker’s perspective, as opposed to a defender’s viewpoint. Draw out the talents of your team. Create an architecture diagram and label the artifacts step 2: The key areas of focus for the tool is: One is to identify a threat and the centre of origin, second being the seriousness of the. With the default installation microsoft tmt contains many useful templates like ones since aqua, medical device, etc. Lifetime premium up to 80% off! Web here’s a diagram that highlights this process: Web this document describes a structured approach to application threat modeling that enables you to identify, quantify, and address the security risks associated with an application. Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). As a result, it greatly reduces the total cost of development. Threat modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value. Is there a template containing stencils for azure and for desktop applications, or can 2 stencils be loaded or combined? Web choose from 71 printable design templates, like threat posters, flyers, mockups, invitation cards, business cards, brochure,etc. Web threat modeling is a form of risk assessment that models aspects of the attack and defense sides of a particular logical entity, such as a piece of data, an application, a host, a system, or an environment. Web this will take you to the list of available templates. The key areas of focus for the tool is: A threat model is a structured representation of all the information that affects the security of an application. Web the threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Web 05.08.2021 / mikhail rusakovich. Describe threat description step 5: Threatware provides an scheme for a threat model template that is tried and tested and been used in different or. Create an architecture diagram and label the artifacts step 2: Web a threat assessment checklist must include three major steps. Web threat modeling is a structured approach of identifying and prioritizing potential threats to a system, and determining the value that potential mitigations would have in reducing or neutralizing those threats.Aws Threat Modeling Tool Template
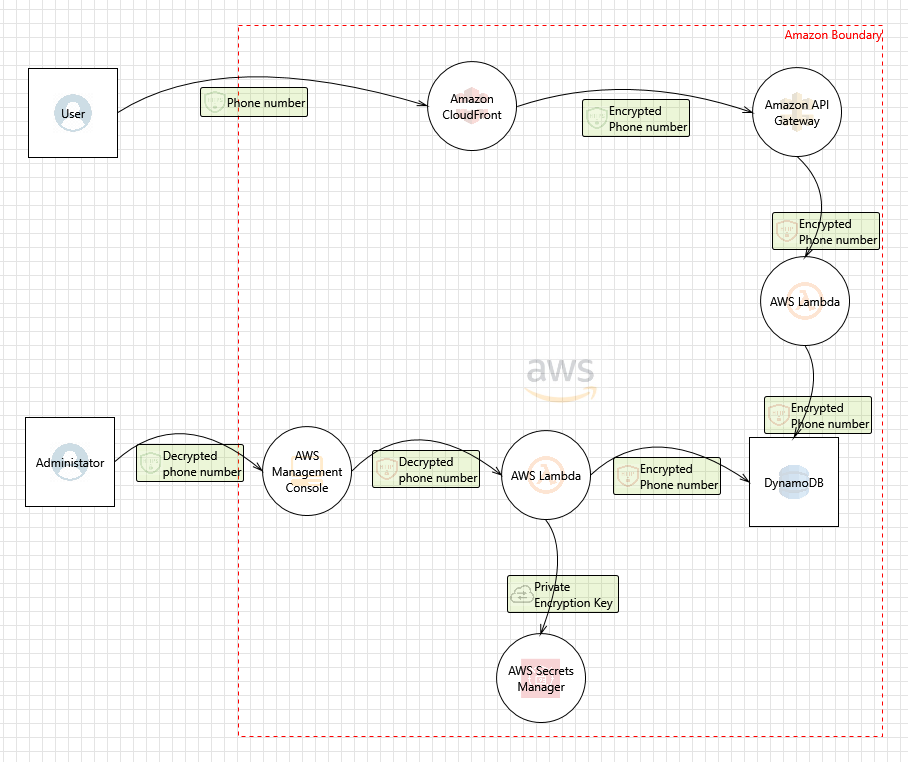
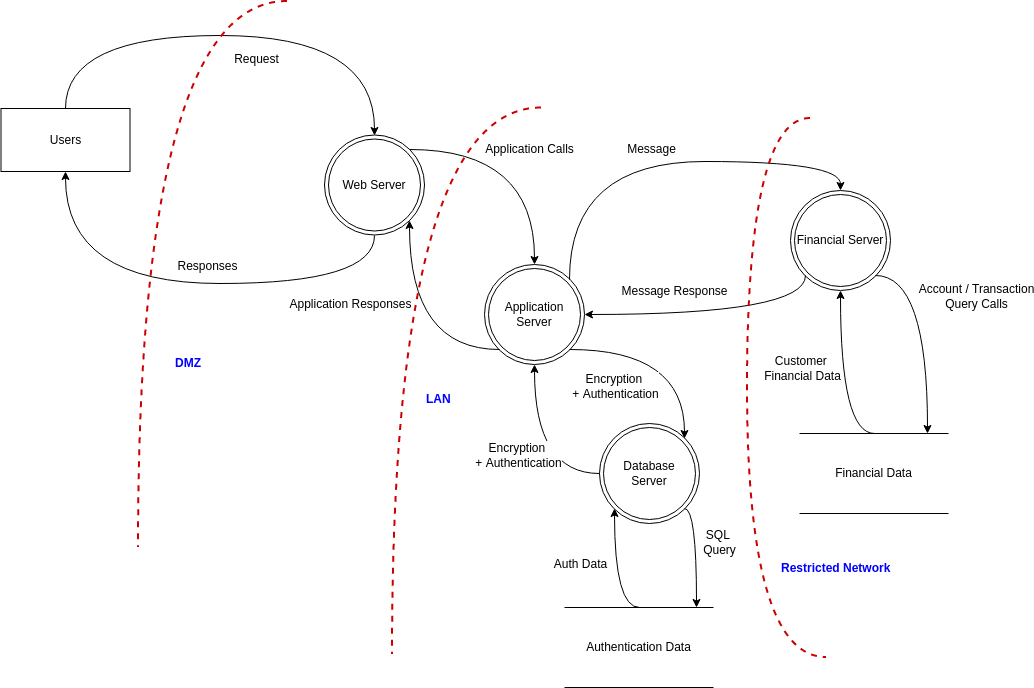
Website Threat Modeling Threat Model Diagram Template
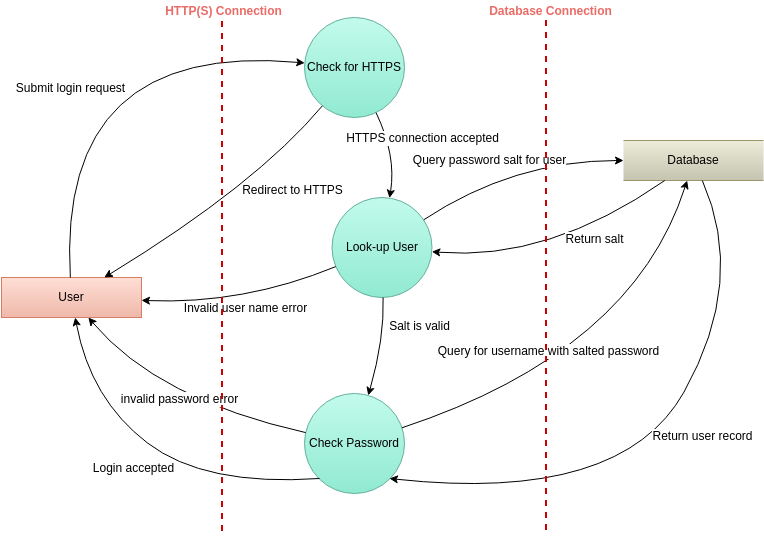
Threat Modeling Threat Model Diagram Template
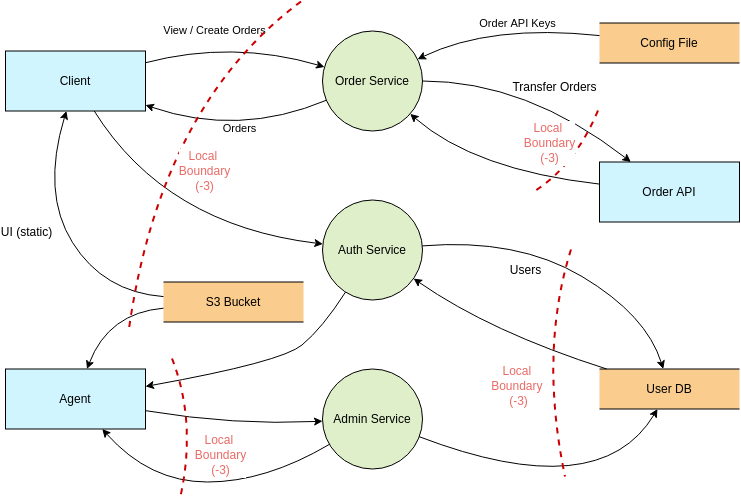
Threat modeling in the context of microservice architectures IBM
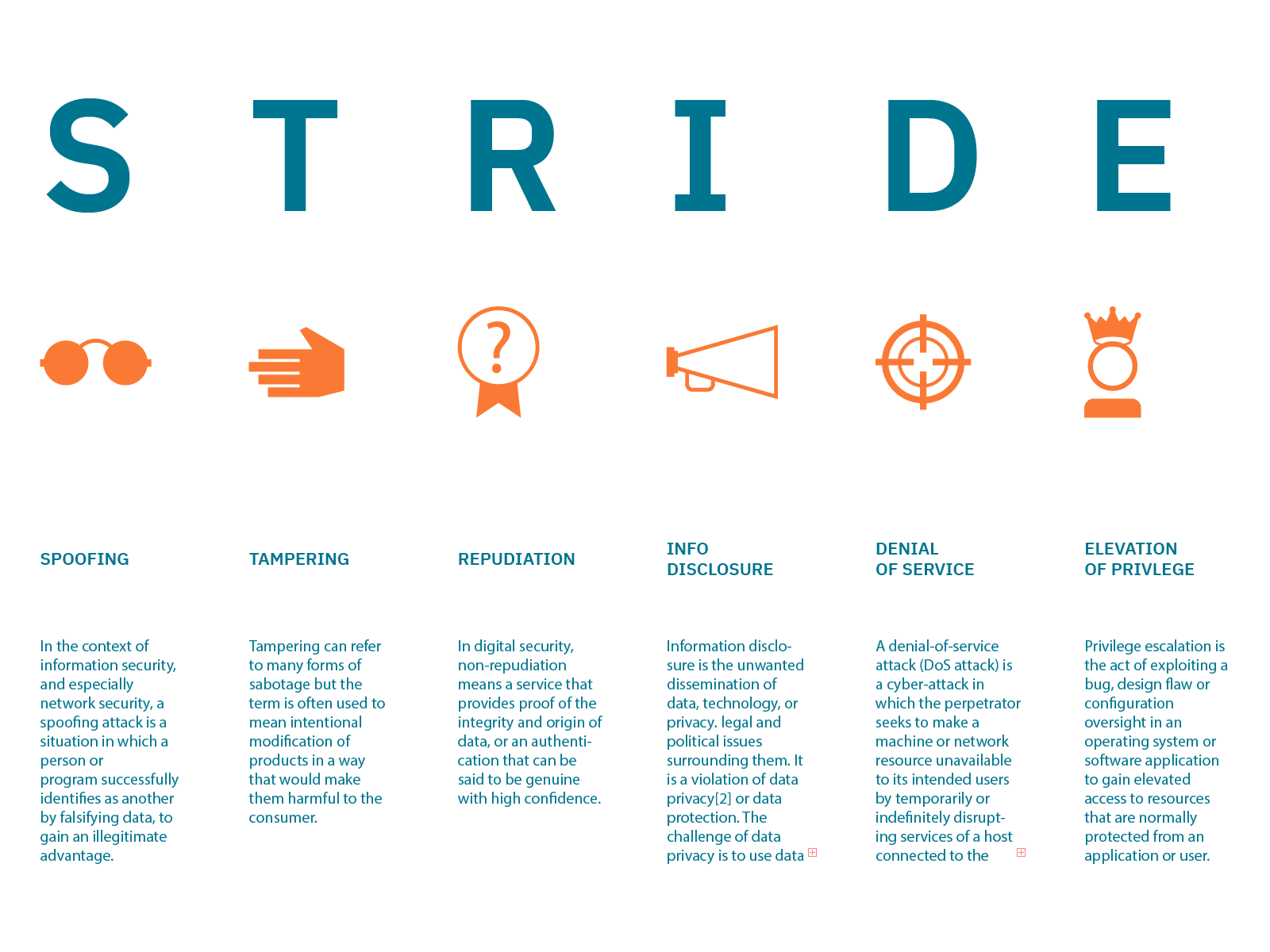
What Is Threat Modeling? (+Top Threat Model Examples)
GitHub AzureArchitecture/threatmodeltemplates Templates for the
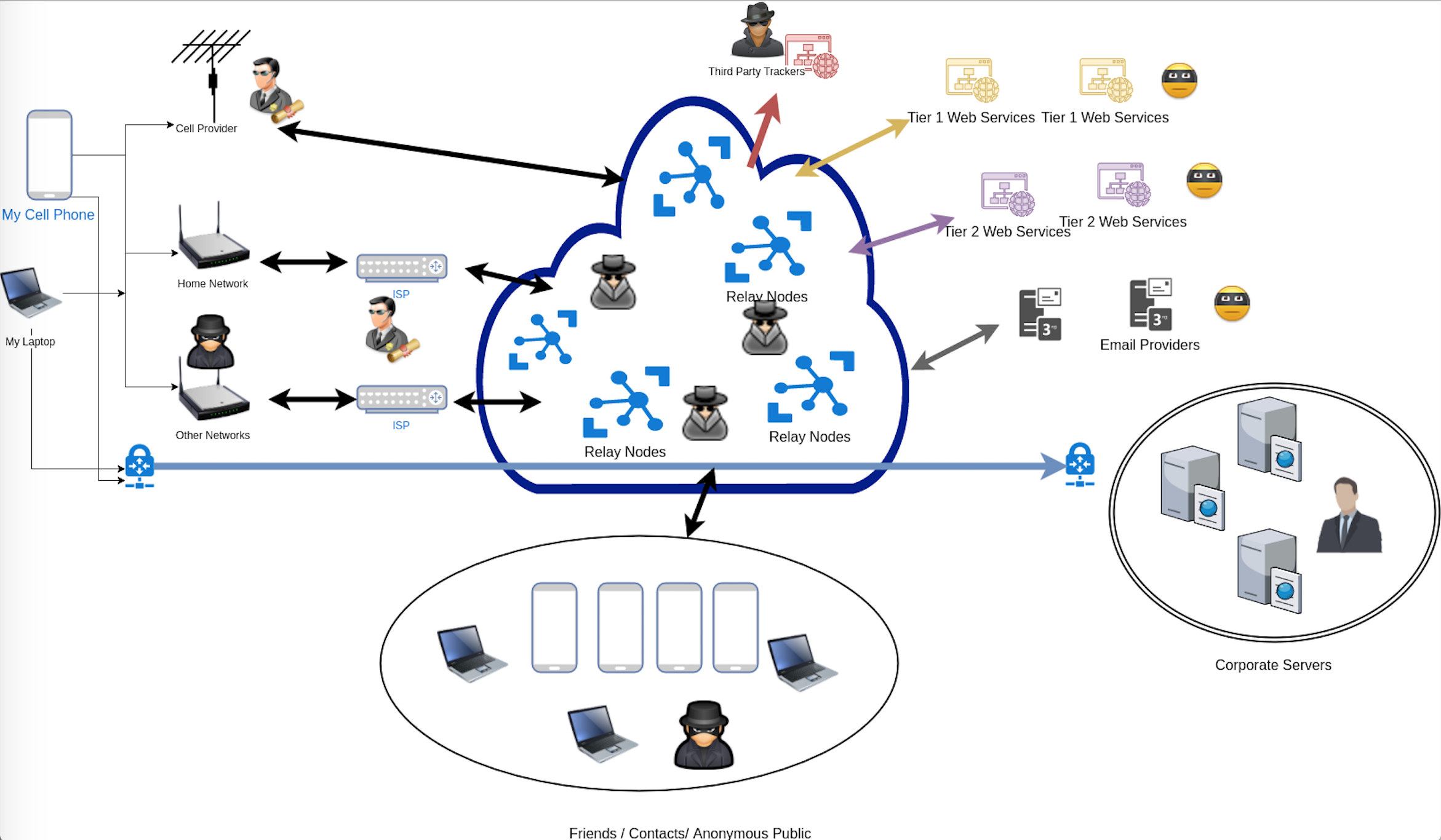
Creating Your Own Personal Threat Model
Threat Modeling Threat Model Diagram Template
Threat Modeling Threat Model Diagram Template
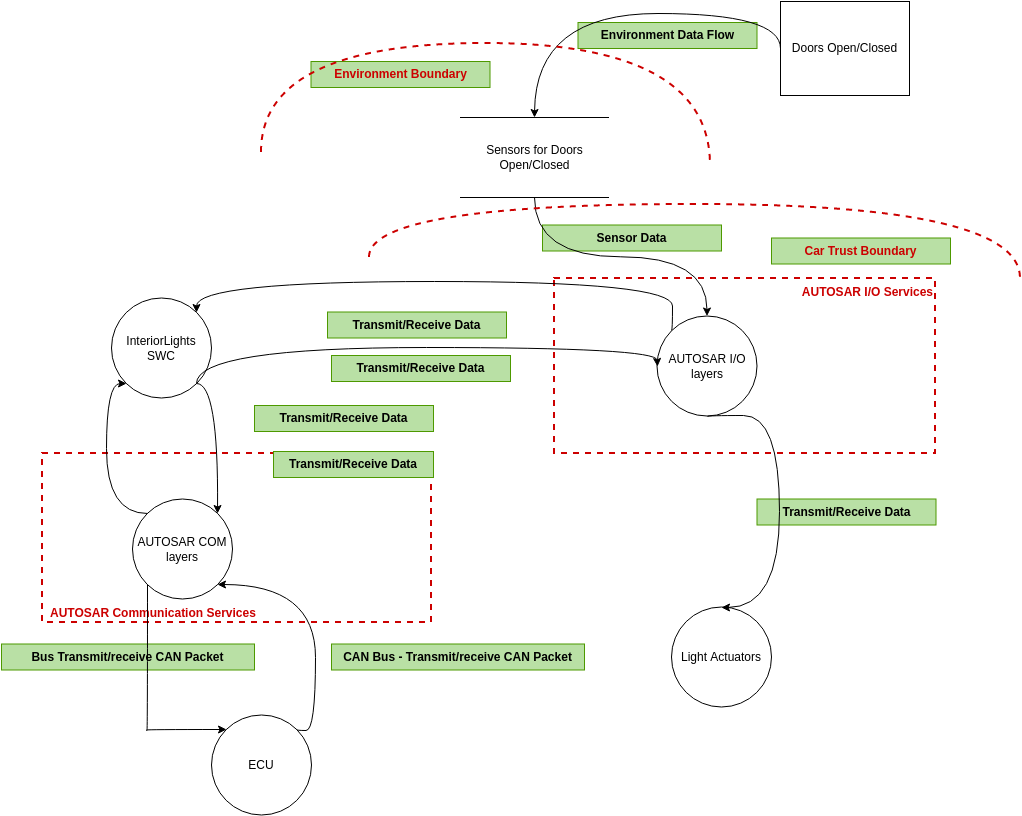
The Automotive Threat Modeling Template NCC Group Research
Related Post: