Threat Intelligence Template
Threat Intelligence Template - Web cyber threat intelligence report volume 1 view full report in an era of unprecedented uncertainty, with so many devices scattered throughout enterprise. Select the rule templates menu tab. Empower your team with huntress mdr. Web a cyber threat intelligence analyst is the specific position designed to be able to synthesize the tactical, operational intelligence and create strategic intelligence. In the search window type threat intelligence. Ad access 24/7 experts for managed detection & response. Web import threat indicators, view logs, and create rules to generate security alerts and incidents, and visualize threat intelligence data with microsoft sentinel. Web cyber threat intelligence has become a critical tool for organizations trying to defend their networks. Web organizations and security teams use threat intelligence to identify potential behaviors or characteristics associated with a certain threat, implement more granular security. Web this template leverages several models in the cyber threat intelligence domain (such as the intrusion kill chain, campaign correlation, the courses of action matrix and the. Web a cyber threat intelligence analyst is the specific position designed to be able to synthesize the tactical, operational intelligence and create strategic intelligence. Web organizations and security teams use threat intelligence to identify potential behaviors or characteristics associated with a certain threat, implement more granular security. Industry leading cybersecurity protection for your data and devices. Web microsoft defender for. Select the rule templates menu tab. Get the cyberthreat intelligence you need to block an entire. Web click the analytics menu from the configuration section. Enrich your threat analysis w/ibm security services. Web cyber threat intelligence report volume 1 view full report in an era of unprecedented uncertainty, with so many devices scattered throughout enterprise. Web cyber threat intelligence has become a critical tool for organizations trying to defend their networks. Web reference iso 27001 threat intelligence i am going to show you what iso 27001 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, an iso 27001. Web view the threat intelligence you’ve imported in your logs; See how to. Web reference iso 27001 threat intelligence i am going to show you what iso 27001 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, an iso 27001. Web click the analytics menu from the configuration section. In bicep, you can specify the parent resource for a child resource. Select the rule templates menu tab. Web this. In the search window type threat intelligence. Web click the analytics menu from the configuration section. To unlock the full content, please fill out our simple form and receive instant access. Empower your team with huntress mdr. Web cyber threat intelligence has become a critical tool for organizations trying to defend their networks. Web a cyber threat intelligence analyst is the specific position designed to be able to synthesize the tactical, operational intelligence and create strategic intelligence. Web below is an example of how to enable and configure a rule to generate security alerts using the threat indicators you've imported into microsoft sentinel. Web threat intelligence reports (tirs) are an important tool for. Web view the threat intelligence you’ve imported in your logs; Web cyber threat intelligence report volume 1 view full report in an era of unprecedented uncertainty, with so many devices scattered throughout enterprise. Web reference iso 27001 threat intelligence i am going to show you what iso 27001 annex a 5.7 threat intelligence is, what’s new, give you iso 27001. Web click the analytics menu from the configuration section. Web threat intelligence policy template. Get the cloud threat report today. Web reference iso 27001 threat intelligence i am going to show you what iso 27001 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, an iso 27001. Select the rule templates menu tab. Web click the analytics menu from the configuration section. Web defender threat intelligence maps the entire internet to expose cyberthreat actors and their infrastructures. In the search window type threat intelligence. Web view the threat intelligence you’ve imported in your logs; Web import threat indicators, view logs, and create rules to generate security alerts and incidents, and visualize threat intelligence. Web view the threat intelligence you’ve imported in your logs; Web microsoft defender for iot has released the october 2023 threat intelligence package. Get the cyberthreat intelligence you need to block an entire. See how to set names and types for child resources in bicep. Web defender threat intelligence maps the entire internet to expose cyberthreat actors and their infrastructures. Web threat intelligence policy template. Get the cloud threat report today. Web microsoft defender for iot has released the october 2023 threat intelligence package. Web defender threat intelligence maps the entire internet to expose cyberthreat actors and their infrastructures. Web this template leverages several models in the cyber threat intelligence domain (such as the intrusion kill chain, campaign correlation, the courses of action matrix and the. Web organizations and security teams use threat intelligence to identify potential behaviors or characteristics associated with a certain threat, implement more granular security. Web view the threat intelligence you’ve imported in your logs; Empower your team with huntress mdr. Get the cyberthreat intelligence you need to block an entire. Web threat intelligence reports (tirs) are an important tool for businesses looking to stay informed about the latest cyber threats and take appropriate actions to. In bicep, you can specify the parent resource for a child resource. Web import threat indicators, view logs, and create rules to generate security alerts and incidents, and visualize threat intelligence data with microsoft sentinel. Ad access 24/7 experts for managed detection & response. See how to set names and types for child resources in bicep. The package is available for download from the microsoft. Enrich your threat analysis w/ibm security services. Web cyber threat intelligence has become a critical tool for organizations trying to defend their networks. In the search window type threat intelligence. Industry leading cybersecurity protection for your data and devices. Web click the analytics menu from the configuration section.What is Cyber Threat Intelligence? [Beginner's Guide]
Free Cyber Security Intelligence And Threat Report
Threat Intelligence PowerPoint Template PPT Slides
Cyber Threat Intelligence Requirements Ppt Powerpoint Presentation
Threat Assessment Report Template Professional Template
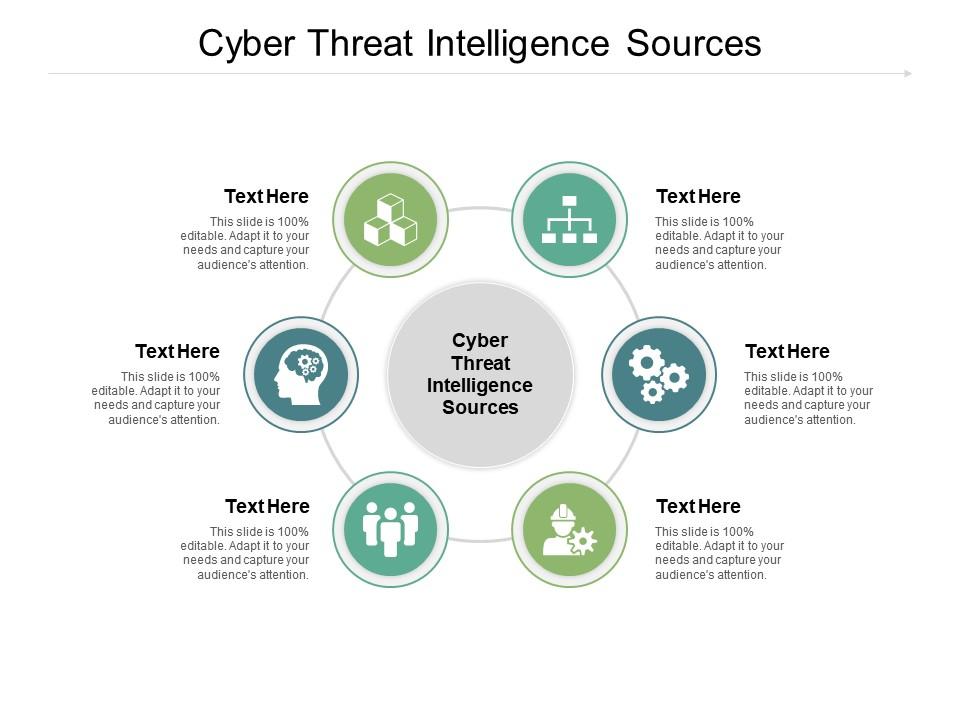
Cyber Threat Intelligence Sources Ppt Powerpoint Presentation
Cyber Threat Intelligence PowerPoint Template PPT Slides
Threat Intelligence Program Template Ppt Powerpoint Presentation
4 Steps to a Business Threat Assessment [+ Template]
What is Cyber Threat Intelligence? [Beginner's Guide]
Related Post:
![What is Cyber Threat Intelligence? [Beginner's Guide]](https://www.crowdstrike.com/wp-content/uploads/2019/07/crowdstrike-threat-intelligence-areas.png)




![4 Steps to a Business Threat Assessment [+ Template]](https://www.alertmedia.com/wp-content/uploads/2021/07/shutterstock_1614345841-scaled-e1627494359810.jpg)
![What is Cyber Threat Intelligence? [Beginner's Guide]](https://www.crowdstrike.com/wp-content/uploads/2019/07/operationalizing-threat-intelligence-2048x1149.png)