Threat Hunting Template
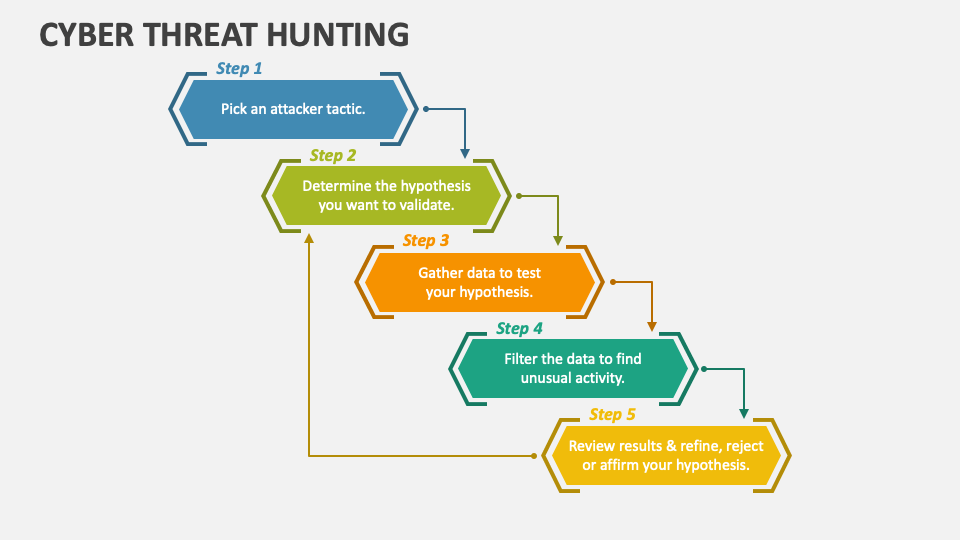
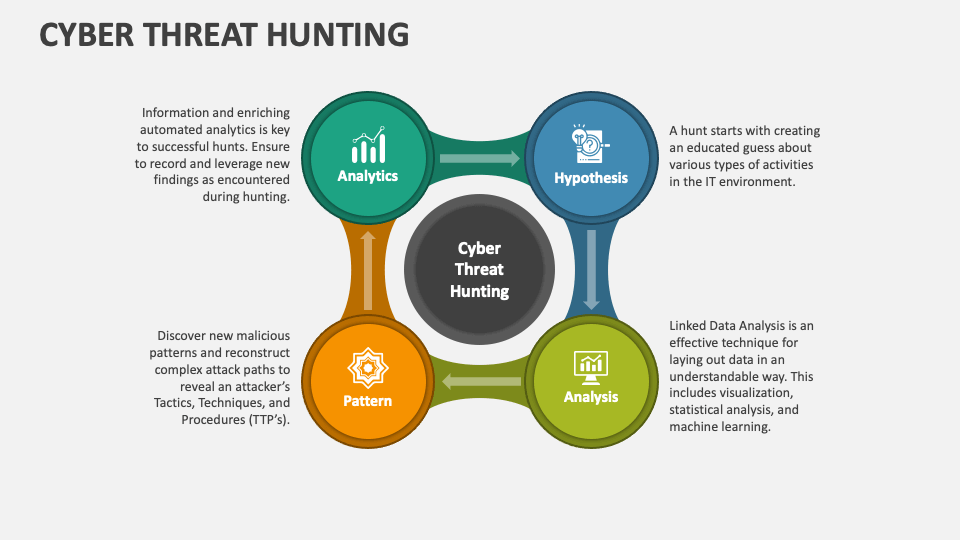
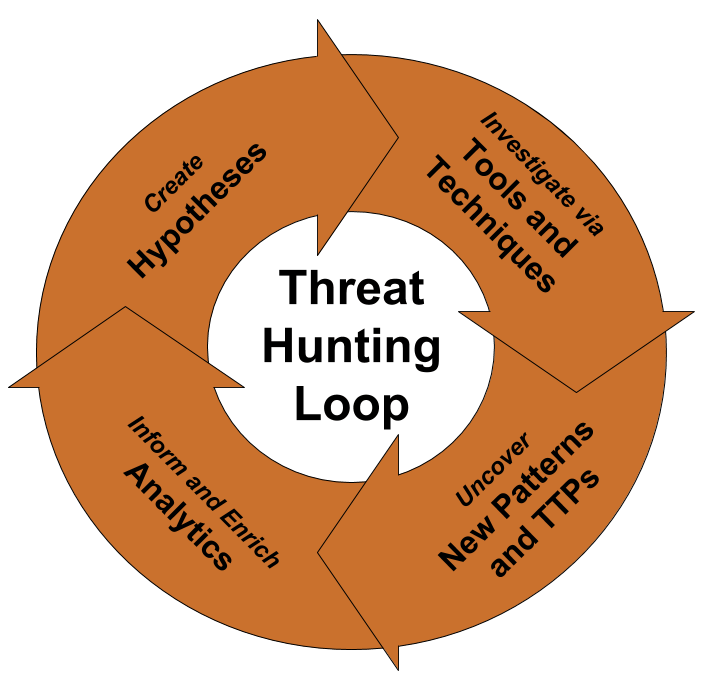
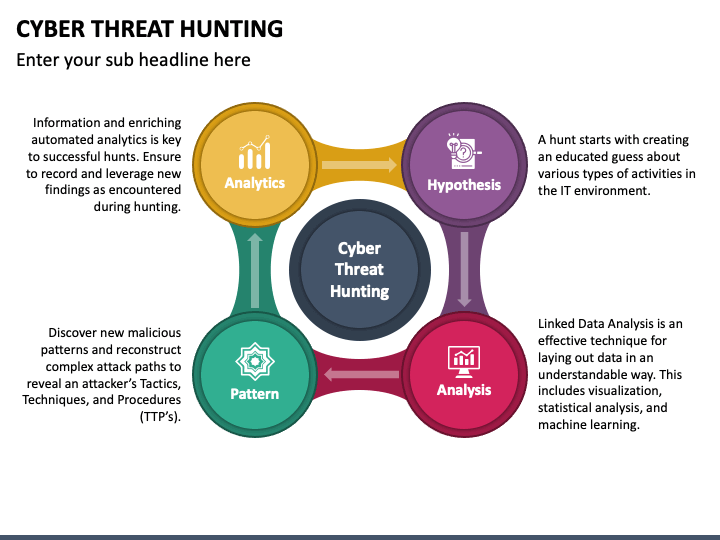
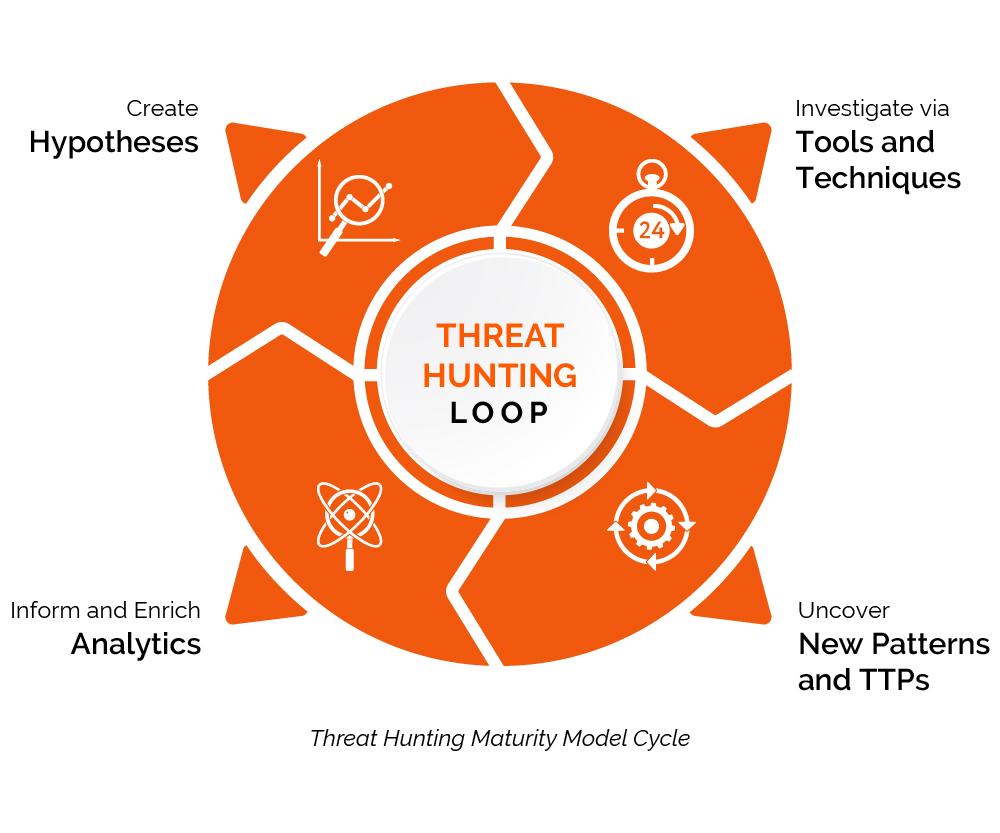
Threat Hunting Template - Determining your security operation’s maturity. Web threat hunting can be broken down into three steps: Ad learn how businesses defend against threats with mdr for microsoft 365. Easily train teams large & small remotely. The word “hunting” is an emerging term within cybersecurity for which the exact definition is still evolving. In the 2017 threat hunting survey, the. Threat hunt like a professional. Web vast — vast (visual, agile and simple threat modeling) is a malleable and scalable modeling process for security planning throughout the software. Resources enhance your skills with. Threat hunting is a popular topic these days, and there are a lot of people who want to get started but. Threat hunt like a professional. Access 24/7 experts for managed detection & response. Get a free course trial! Easily train teams large & small remotely. Web vast — vast (visual, agile and simple threat modeling) is a malleable and scalable modeling process for security planning throughout the software. The word “hunting” is an emerging term within cybersecurity for which the exact definition is still evolving. Threat hunting is typically a focused process. The example report included offers a simplified format suitable for executives and technicians. Ad industry leading cybersecurity protection for your data and devices. Threat hunting is a proactive and critical aspect of cybersecurity that involves searching. An intro to threat hunting and why it’s important. The example report included offers a simplified format suitable for executives and technicians. Web vast — vast (visual, agile and simple threat modeling) is a malleable and scalable modeling process for security planning throughout the software. Web click here to download our free threat hunting framework to learn how to build. Creating an actionable hypothesis, executing the hypothesis, and testing the hypothesis to completion. Web for this, use a template to match your intended audience. Describes the focus of the hunt and proposes a theory about the potential threat. Empower your team with huntress mdr. Provide technical capabilities and expertise to understand and remediate adversary activity via detections, partnerships, and forensics. Hunting for adversaries in your it environment. Threat hunting is a popular topic these days, and there are a lot of people who want to get started but. The example report included offers a simplified format suitable for executives and technicians. A concise overview of the threat hunting operation and its results. The word “hunting” is an emerging term within. Provide technical capabilities and expertise to understand and remediate adversary activity via detections, partnerships, and forensics and by. Due to its clear benefits in detection, threat hunting has garnered the attention of many organizations. Ad industry leading cybersecurity protection for your data and devices. Easily train teams large & small remotely. Threat hunting is a proactive and critical aspect of. A robust report template typically includes several key sections: The example report included offers a simplified format suitable for executives and technicians. Resources enhance your skills with. Top requirements for cyber analysts and management. Threat hunt like a professional. An intro to threat hunting and why it’s important. Visual paradigm online (vp online) is an online drawing software that supports threat model diagram and a wide range of diagrams that covers uml, erd,. Resources enhance your skills with. Ad learn how businesses defend against threats with mdr for microsoft 365. Web 1.1 definition of hunting. Resources enhance your skills with. Threat hunting is typically a focused process. Access 24/7 experts for managed detection & response. Web 1.1 definition of hunting. Take your workplace threats training from boring to brilliant. Visual paradigm online (vp online) is an online drawing software that supports threat model diagram and a wide range of diagrams that covers uml, erd,. Top requirements for cyber analysts and management. Ad comprehensive library of interactive content. A concise overview of the threat hunting operation and its results. Threat hunting is a popular topic these days, and there are. The hunter collects information about the environment and raises hypotheses about potential threats. A concise overview of the threat hunting operation and its results. Web threat hunting can be broken down into three steps: Get a free course trial! A robust report template typically includes several key sections: Threat hunt like a professional. Threat hunting is typically a focused process. Take your workplace threats training from boring to brilliant. Creating an actionable hypothesis, executing the hypothesis, and testing the hypothesis to completion. Ad comprehensive library of interactive content. Threat hunting is a proactive and critical aspect of cybersecurity that involves searching for signs of malicious activity on your organization’s networks and. Describes the focus of the hunt and proposes a theory about the potential threat. In the 2017 threat hunting survey, the. Provide technical capabilities and expertise to understand and remediate adversary activity via detections, partnerships, and forensics and by. Due to its clear benefits in detection, threat hunting has garnered the attention of many organizations. Web for this, use a template to match your intended audience. Framework for cyber threat hunting. The example report included offers a simplified format suitable for executives and technicians. Maldocs (malware documents) are malicious documents. Top requirements for cyber analysts and management.Threat Hunting Assessments
How To Start Threat Hunting in CyberSecurity [A guide]
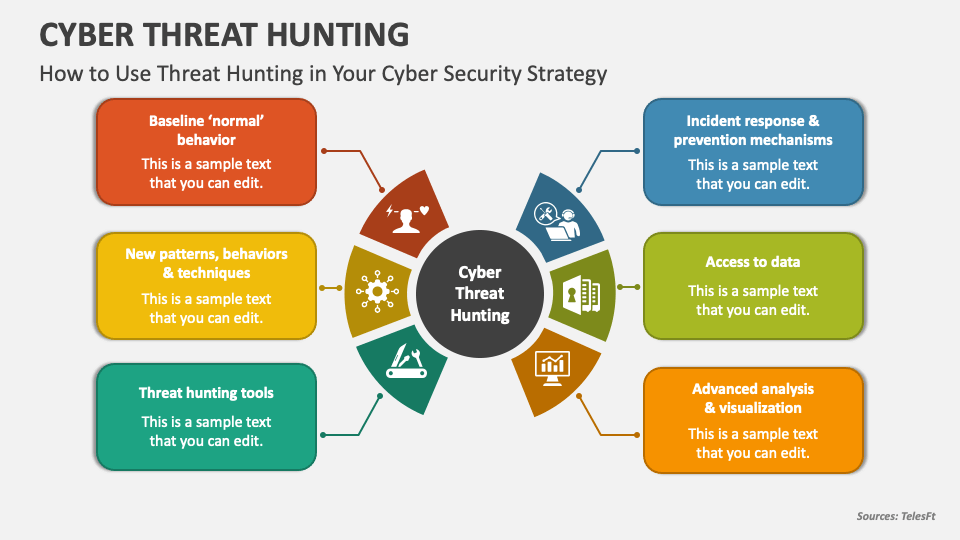
Cyber Threat Hunting PowerPoint Presentation Slides PPT Template
Threat Hunting Report Cybersecurity Insiders
Cyber Threat Hunting PowerPoint Presentation Slides PPT Template
Cyber Threat Hunting Proactive Intrusion Detection Security
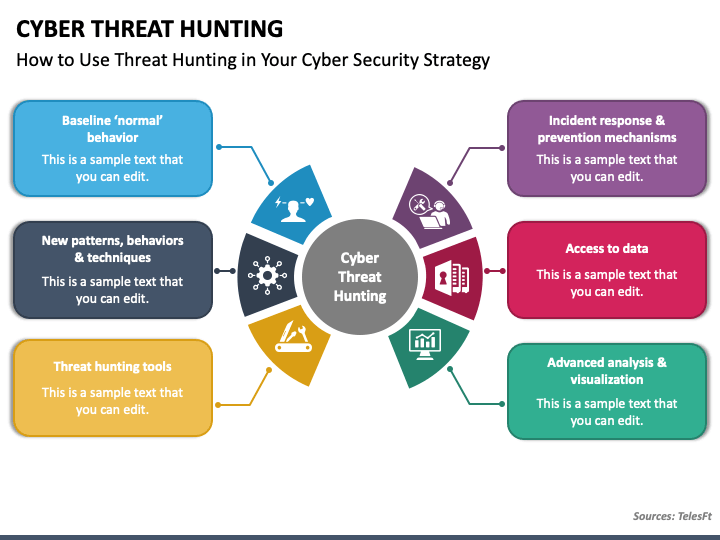
Cyber Threat Hunting PowerPoint Template PPT Slides
A Threat Hunt tale
Cyber Threat Hunting PowerPoint Presentation Slides PPT Template
Cyber Threat Hunting PowerPoint Template PPT Slides
Related Post:

![How To Start Threat Hunting in CyberSecurity [A guide]](https://pbs.twimg.com/media/D5thFeqWAAUHRK0.png)