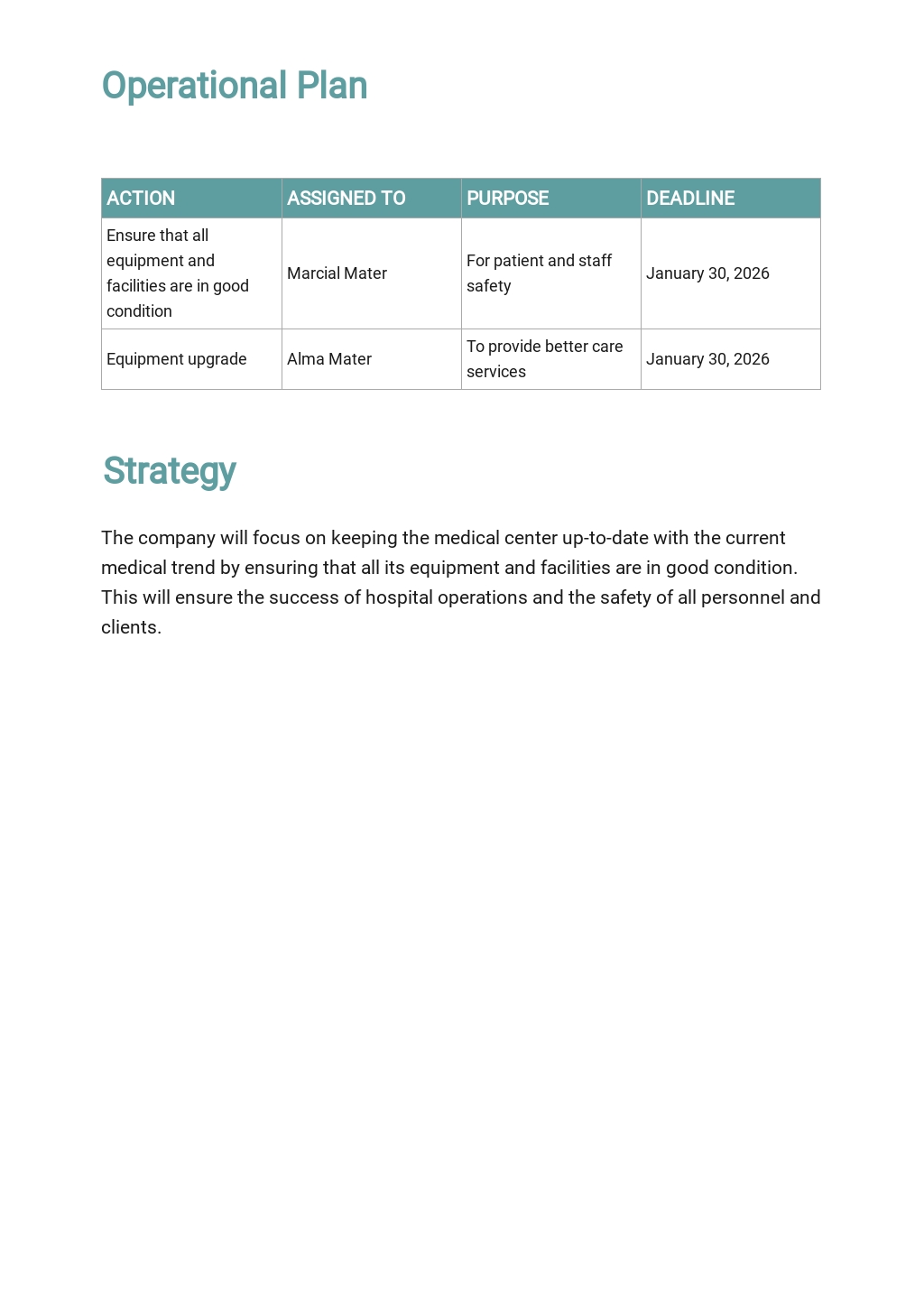
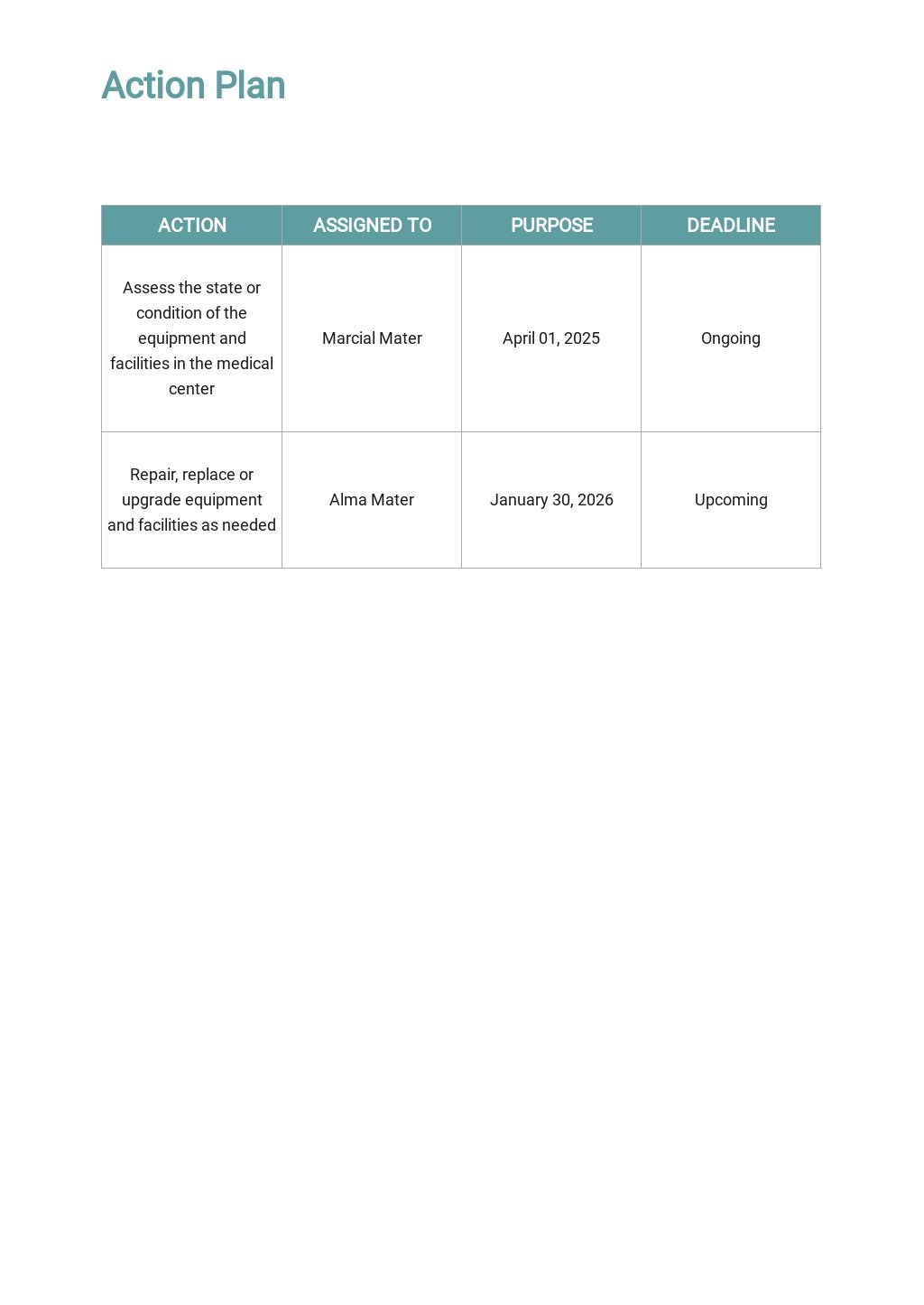
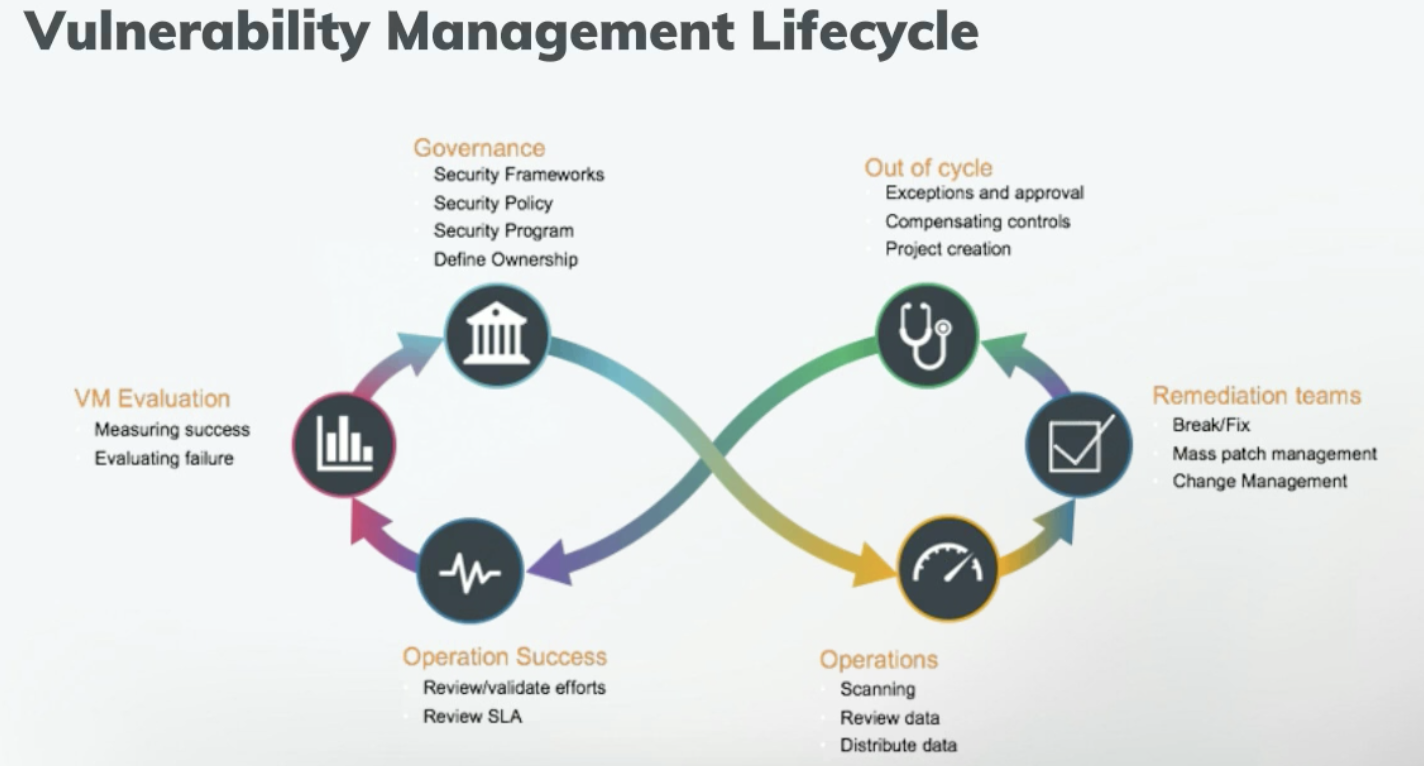
Patch And Vulnerability Management Plan Template
Patch And Vulnerability Management Plan Template - Switch to the rmm #1 in ease of setup, administration & use. Web develop a plan for vulnerability management—outlines a plan creation process and identifies issues and considerations to help ensure that the plan addresses the. Enterprise patch management is the process of identifying, prioritizing, acquiring, installing, and verifying the installation of patches, updates, and. Cspm, cnapp, vulnerability management, and more. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Web patch and vulnerability management is a security practice designed to proactively prevent the exploitation of it vulnerabilities that exist within an organization. Smooth and simple sign up. Web we've created one vulnerability management policy template to find organizations assess and paving security vulnerabilities. Simple, reliable patching with no scripting or cumbersome setup required. Web the owasp vulnerability management guide project seeks to establish guidance on the best practices that organizations can use establish a vulnerability management. Web the owasp vulnerability management guide project seeks to establish guidance on the best practices that organizations can use establish a vulnerability management. While we strive to keep the information up to date and correct, we make. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. Simple, reliable. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Web patch management is the process for identifying, acquiring, installing, and verifying patches for products and systems. Industry leading pricing for application scanner platform. Switch to the rmm #1 in ease of setup, administration & use. Web patch and. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Ad our security scanner will help you keep up with the latest patches for all your servers. Getapp has the tools you need to stay ahead of the competition. Web develop a plan for vulnerability management—outlines a plan creation. Industry leading pricing for application scanner platform. Cspm, cnapp, vulnerability management, and more. If one 570 or more of. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. This report recommends patch management practices for consideration and deployment by. Web enterprise patch management is the process of identifying, prioritizing, acquiring, installing, and verifying installation of patches, updates, and upgrades. This publication is designed to assist. Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Simple, reliable patching with no scripting or cumbersome setup required. Web vulnerability scanning. Enterprise patch management is the process of identifying, prioritizing, acquiring, installing, and verifying the installation of patches, updates, and. Web patch management is the process for identifying, acquiring, installing, and verifying patches for products and systems. Simple, reliable patching with no scripting or cumbersome setup required. Web patch and vulnerability management is a security practice designed to proactively prevent the. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. Web the owasp vulnerability management guide project seeks to establish guidance on the best practices that organizations can use establish a vulnerability management. Web patch and vulnerability management is a security practice designed to proactively prevent the exploitation of. Web enterprise patch management is the process of identifying, prioritizing, acquiring, installing, and verifying installation of patches, updates, and upgrades. Simple, reliable patching with no scripting or cumbersome setup required. Industry leading pricing for application scanner platform. If one or more of the. Web develop a plan for vulnerability management—outlines a plan creation process and identifies issues and considerations to. Cspm, cnapp, vulnerability management, and more. This report recommends patch management practices for consideration and deployment by. While we strive to keep the information up to date and correct, we make. Web enterprise patch management is the process of identifying, prioritizing, acquiring, installing, and verifying installation of patches, updates, and upgrades. Web the objective of this document is to bridge. Web patch and vulnerability management is a security practice designed to proactively prevent the exploitation of it vulnerabilities that exist within an organization. Web vulnerability scanning standard detect: Ad our security scanner will help you keep up with the latest patches for all your servers. Getapp has the tools you need to stay ahead of the competition. If one or. Web patch and vulnerability management is a security practice designed to proactively prevent the exploitation of it vulnerabilities that exist within an organization. Ad learn how businesses defend against threats with mdr for microsoft 365. Web the owasp vulnerability management guide project seeks to establish guidance on the best practices that organizations can use establish a vulnerability management. Enterprise patch management is the process of identifying, prioritizing, acquiring, installing, and verifying the installation of patches, updates, and. Web patch management is the process for identifying, acquiring, installing, and verifying patches for products and systems. Powered by huntress' 24/7 expert security operations center. Industry leading pricing for application scanner platform. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable repeatable functions: Web vulnerability management policy template for cis control 7 cybersecurity professionals are constantly challenged by attackers actively searching for vulnerabilities within. Web develop a plan for vulnerability management—outlines a plan creation process and identifies issues and considerations to help ensure that the plan addresses the. Web we've created one vulnerability management policy template to find organizations assess and paving security vulnerabilities. Web enterprise patch management is the process of identifying, prioritizing, acquiring, installing, and verifying installation of patches, updates, and upgrades. Cspm, cnapp, vulnerability management, and more. Switch to the rmm #1 in ease of setup, administration & use. Switch to the rmm #1 in ease of setup, administration & use. If one 570 or more of. This report recommends patch management practices for consideration and deployment by. While we strive to keep the information up to date and correct, we make. Web this is the procedure to address patching emergencies in a crisis 569 situation, such as a severe vulnerability or a vulnerability being actively exploited. Web a patch management policy is an it strategy document that outlines the processes and methodology used to ensure hardware and software on a corporate.Free Vulnerability Assessment Plan Template Google Docs, Word, Apple
Professional Patch Management Plan Template Riteforyouwellness
Creating a Vulnerability Management Strategy zSecurity
Free Vulnerability Assessment Plan Template Google Docs, Word, Apple
Simple Patch Management Plan Template Patch management, Emergency
An effective vulnerability management lifecycle Entrepreneur Business
Vulnerability Management Policy Template in 2021 Patch management
Vulnerability & Patch Management Program (VPMP) Security Waypoint
Free Vulnerability Assessment Templates Smartsheet
Vulnerability Management Program Template Stcharleschill Template
Related Post: