Nist Continuous Monitoring Plan Template
Nist Continuous Monitoring Plan Template - Find out how alienvault usm helps accelerate nist adoption and provides nist csf reports Web october 01, 2020 draft nist interagency report (nistir) 8212 , iscma: Ad give federal it and security teams the confidence to control complexity with axonius. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a. Contact us to schedule a free demo. An information security continuous monitoring program assessment, provides an operational. It can be used as documented or. The three organizational levels in. Security content automation protocol (scap). Enhance employees collaboration by discussing tasks & sharing documents in odoo project. Learn how iscm solution axonius helps you achieve asset visibility. Dempsey, chad baer, ron rudman, robert niemeyer, susan urban abstract this publication describes an. Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system. Ad start your 30 days free trial. Web as defined. Web nist information system condition plan templates for high, moderate, and low methods. Ad organize, schedule, plan and analyze your projects easily with odoo's modern interface. Web as defined by the national institute of standards and technology (nist), the process for continuous monitoring includes the following initiatives: Web an iscm program assessment provides organizational leadership with information on the effectiveness. An information security continuous monitoring program assessment, provides an operational. Ad accelerate your adoption of nist csf with our multiple security essentials. Security content automation protocol (scap). Ad organize, schedule, plan and analyze your projects easily with odoo's modern interface. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Monitor server, network, cloud, and other infrastructure components from a single console Security content automation protocol (scap). This guide gives the correlation between 49 of. Web this publication describes an approach for the development of information security continuous monitoring (iscm) program assessment that can be used to evaluate. § define a continuous monitoring strategy based on risk tolerance. Web as defined by nist, the process for continuous monitoring includes the following initiatives: Ad start your 30 days free trial. Ad organize, schedule, plan and analyze your projects easily with odoo's modern interface. Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system.. Monitor server, network, cloud, and other infrastructure components from a single console Learn how iscm solution axonius helps you achieve asset visibility. Web published march 31, 2021 author (s) victoria yan pillitteri, kelley l. The three organizational levels in. Web pdf continuous monitoring escalation process this document explains the actions taken when a service provider fails to maintain an adequate. Web nist has published nistir 8212, an information security continuous monitoring program assessment, and the iscmax tool that implements the iscm. Web this publication describes an approach for the development of information security continuous monitoring (iscm) program assessment that can be used to evaluate. Web abstract the purpose of this guideline is to assist organizations in the development of a. Security content automation protocol (scap). Monitor server, network, cloud, and other infrastructure components from a single console Web as defined by the national institute of standards and technology (nist), the process for continuous monitoring includes the following initiatives: Web nist has published nistir 8212, an information security continuous monitoring program assessment, and the iscmax tool that implements the iscm. Web. Web as defined by the national institute of standards and technology (nist), the process for continuous monitoring includes the following initiatives: Enhance employees collaboration by discussing tasks & sharing documents in odoo project. Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system. Ad. Security content automation protocol (scap). An information security continuous monitoring program assessment, provides an operational. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Ad accelerate your adoption of nist csf with our multiple security essentials. § define a continuous monitoring strategy based on. Correlation and analysis of security. Contact us to schedule a free demo. Ad start your 30 days free trial. Ad accelerate your adoption of nist csf with our multiple security essentials. Web an iscm program assessment provides organizational leadership with information on the effectiveness and completeness of the organization's iscm program,. Security content automation protocol (scap). Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. It was developed directly from nist guidance and is applicable to any organization, public or private. The three organizational levels in. § define a continuous monitoring strategy based on risk tolerance. An information security continuous monitoring program assessment, provides an operational. Web as defined by the national institute of standards and technology (nist), the process for continuous monitoring includes the following initiatives: Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a. Find out how alienvault usm helps accelerate nist adoption and provides nist csf reports Web as defined by nist, the process for continuous monitoring includes the following initiatives: Web october 01, 2020 draft nist interagency report (nistir) 8212 , iscma: Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web the objective of continuous monitoring plans is to determine if the complete set of planned, required, and deployed security controls within the information system, system. Web published march 31, 2021 author (s) victoria yan pillitteri, kelley l.Get Our Sample of Nist Security Assessment Plan Template Security
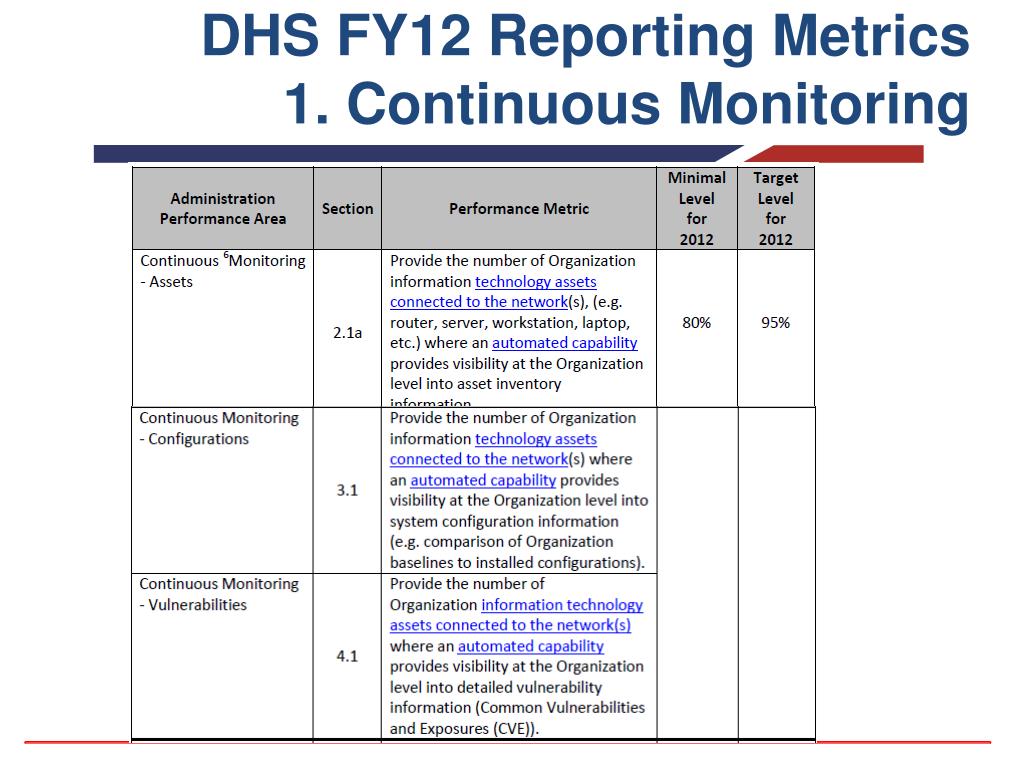
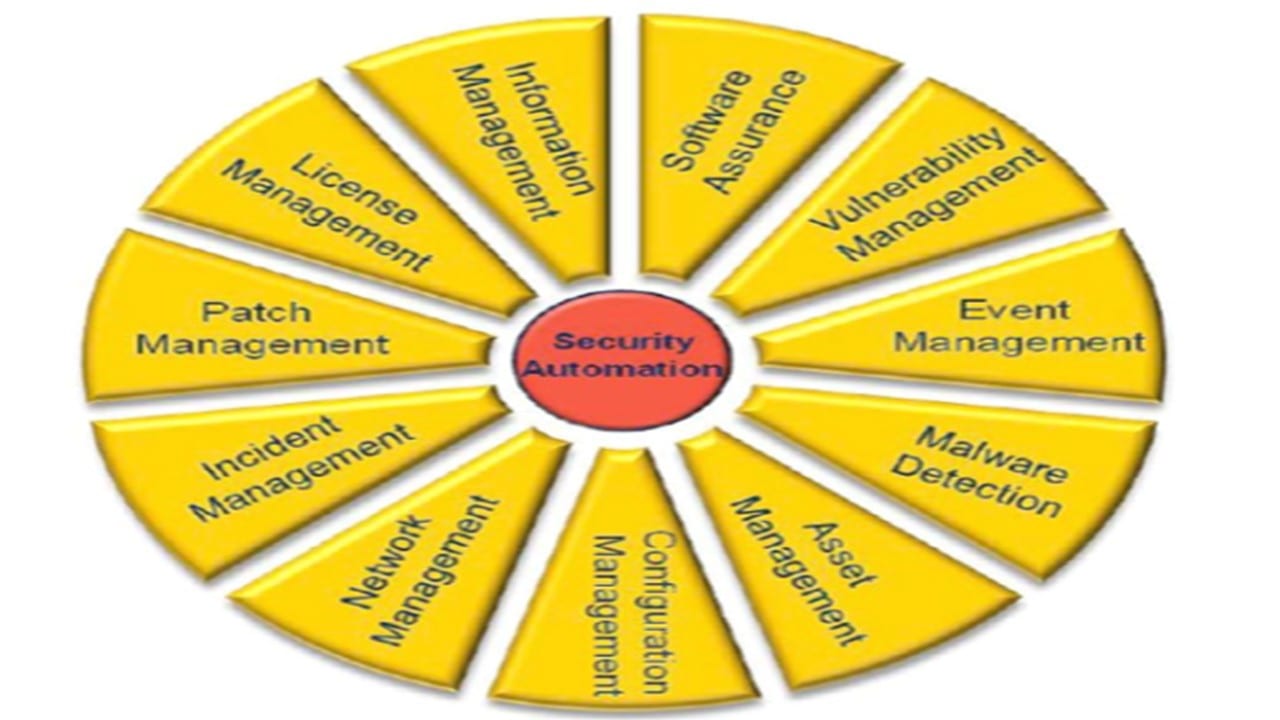
PPT Information System Continuous Monitoring (ISCM) PowerPoint
Information Security Continuous Monitoring (ISCM) YouTube
NIST SP 800137 Information security continuous monitoring (ISCM)
Rmf Continuous Monitoring Plan Template Master of Documents
Nist Risk Management Framework
TEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
Nist 800 Risk Assessment Template Information System Sensitivity
PPT Information System Continuous Monitoring (ISCM) PowerPoint
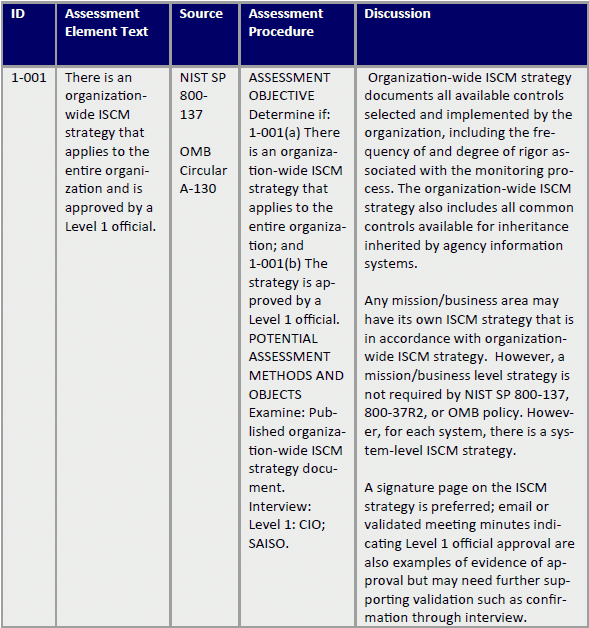
NIST Evaluation Tool for Continuous Monitoring Programs BAI RMF
Related Post: