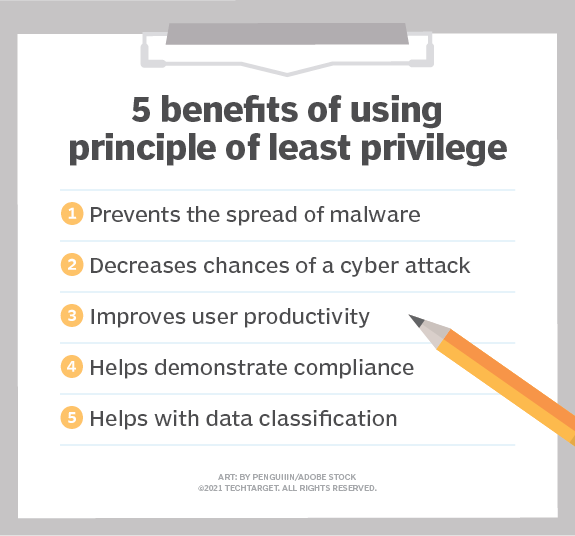
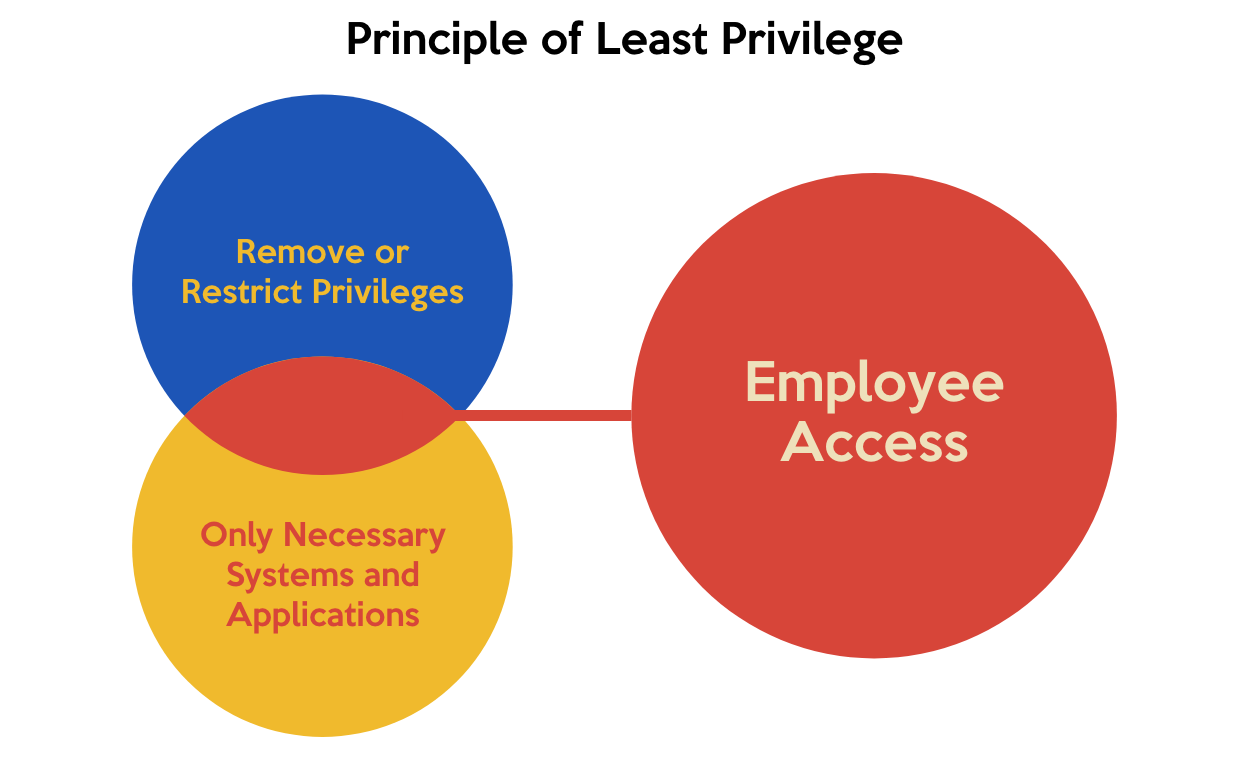
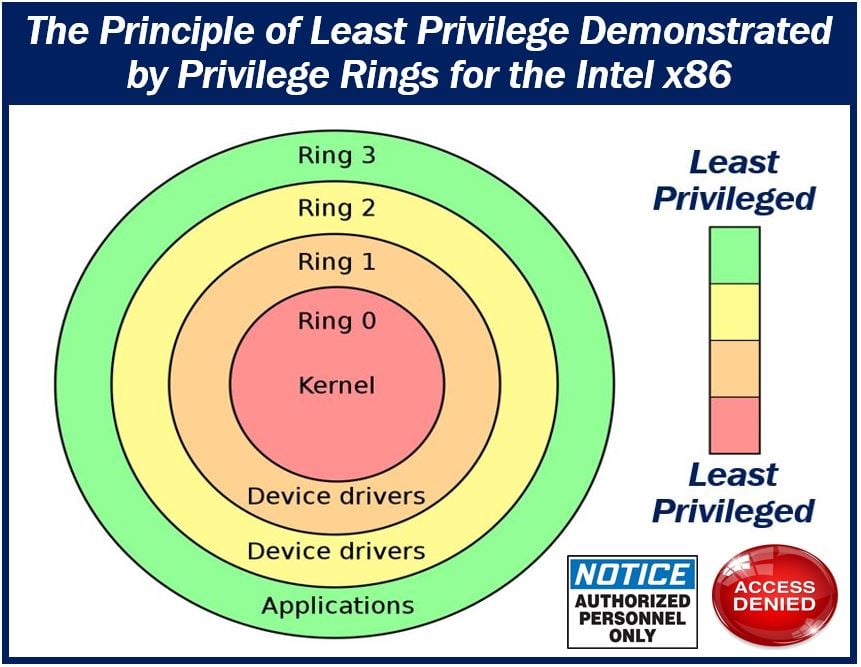
Least Privilege Policy Template
Least Privilege Policy Template - Web the principle of least privilege, or “least privilege access,” is a cyber security best practice that requires limiting users to the privileges necessary to perform a specific task. Web follow the principle of least privilege. This principle sounds very technical, but we see examples of least privileged access everywhere in our daily lives. You have to communicate them transparently and straightforwardly to ensure the employees understand the company's policy and its consequences. Web small business policy template. Web in this post, i show you how to conform to the principle of least privilege while still allowing users to use cloudformation to create the resources they need. Build applications with least privilege in mind during all stages of development. Use the identity platform's consent framework to require that a human consent to the request from the application to access protected data. Web you may also see the security policy examples. It demands that the required permissions for a task shall only grant access to the needed information or resources that a task requires. Web in this post, i show you how to conform to the principle of least privilege while still allowing users to use cloudformation to create the resources they need. Build applications with least privilege in mind during all stages of development. The “principle of least privilege” (short: A maternity leave is given to a female employee who is expecting a. This principle sounds very technical, but we see examples of least privileged access everywhere in our daily lives. Instead, provide only the needed level of privilege to perform specific tasks and only for the period necessary. The principle of least privilege access is a software security best practice that provides a user only the minimum set of rights required to. The company policies and procedures document is also called the policy manual or the. To implement a zero trust security strategy never grant broad or standing privileges. Systems that are designed using zero trust principals should be better positioned to address existing. One of the biggest advantages to a least privilege strategy is the ability to lower the risk of. This leave is given to ensure the safe delivery of the employee’s baby and so that the mother can have enough time to take care of the newborn. Web expenses policy templates often include: Web a minimum access policy ensures that users have the lowest level of privileges to complete necessary functions. Web the principle of least privilege, or “least. Each company has its intern regulations that an employee must know and follow. This principle sounds very technical, but we see examples of least privileged access everywhere in our daily lives. The principle of least privilege access is a software security best practice that provides a user only the minimum set of rights required to perform an assigned job or. Web the principle of least privilege (polp) the first security principle that i am going to discuss is one that most system administrators are familiar with: Systems that are designed using zero trust principals should be better positioned to address existing. Web the principle of least privilege, or “least privilege access,” is a cyber security best practice that requires limiting. Web the principle of least privilege (polp) the first security principle that i am going to discuss is one that most system administrators are familiar with: You may also see the training policy. Web prevent overprivileged applications by revoking unused and reducible permissions. Any privilege elevation must be approved and limited in time and scope. Each company has its intern. Use the identity platform's consent framework to require that a human consent to the request from the application to access protected data. A maternity leave is given to a female employee who is expecting a child. Web follow the principle of least privilege. Each company has its intern regulations that an employee must know and follow. To begin your expenses. You have to communicate them transparently and straightforwardly to ensure the employees understand the company's policy and its consequences. Instead, provide only the needed level of privilege to perform specific tasks and only for the period necessary. Web beyondtrust’s privileged accessible management platform protects your organization from unnecessary remote access, stole credentials, and improperly privileges To implement a zero trust. It demands that the required permissions for a task shall only grant access to the needed information or resources that a task requires. Instead, provide only the needed level of privilege to perform specific tasks and only for the period necessary. Web follow the principle of least privilege. Web you may also see the security policy examples. One of the. Instead, provide only the needed level of privilege to perform specific tasks and only for the period necessary. This principle sounds very technical, but we see examples of least privileged access everywhere in our daily lives. Use the identity platform's consent framework to require that a human consent to the request from the application to access protected data. One of the biggest advantages to a least privilege strategy is the ability to lower the risk of exposure to cyberattacks and minimize any potential damage an infiltration can cause. Web follow the principle of least privilege. To implement a zero trust security strategy never grant broad or standing privileges. A maternity leave is given to a female employee who is expecting a child. Web a minimum access policy ensures that users have the lowest level of privileges to complete necessary functions. The principle of least privilege access is a software security best practice that provides a user only the minimum set of rights required to perform an assigned job or function. You may also see the training policy. The company policies and procedures document is also called the policy manual or the. Any privilege elevation must be approved and limited in time and scope. To begin your expenses policy, summarize employee duties that involve the policies included in the document. Web beyondtrust’s privileged accessible management platform protects your organization from unnecessary remote access, stole credentials, and improperly privileges Web prevent overprivileged applications by revoking unused and reducible permissions. Web you may also see the security policy examples. This leave is given to ensure the safe delivery of the employee’s baby and so that the mother can have enough time to take care of the newborn. Web expenses policy templates often include: The “principle of least privilege” (short: You can summarize the purpose of each policy and how employees can use and comply with it.Enforcing principle of least privilege
Principle of least privilege examples & best practices
The Principle of Enforcing Least Privilege (Part 2) PolicyPak
Identity and Entitlements Management (IAM) Least Privilege Policy for
Principle of Least Privilege Everything You Need to Know
What is the Principle of Least Privilege (POLP)? ManageEngine
The 5 Most Important Strategies of the Security Principle of Least
PPT Secure Software Development PowerPoint Presentation, free
AppLocker vs. PolicyPak Least Privilege Manager PolicyPak
Best Practice Guide to Implementing the Least Privilege Principle
Related Post: