Insider Threat Program Template
Insider Threat Program Template - Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web it is not a template. Insider threat for senior leaders. Here are 3 types of insider threats: Web insider threat program page 1 abstract the u.s. Web this guide supersedes the previous insider threat program guides issued by the nittf and ncsc including the nittf’s 2014 “guide to accompany the national insider threat. The dcsa headquarters is located at: An insider threat is a threat to an organization that comes from negligent or malicious insiders, such as employees, former employees, contractors, third. This is a corporate security and risk management. On cisa.gov, visitors will find. Insider threat and extremism within the dod. Web reduced costs of an insider attack: Web dcsa continues to assess compliance with minimum insider threat requirements, which provide the basic elements necessary to establish a fully functional insider threat. Web employment application risks and mitigation for insiders with national security eligibility. On cisa.gov, visitors will find. Insider threat for senior leaders. An insider threat is a threat to an organization that comes from negligent or malicious insiders, such as employees, former employees, contractors, third. It will define an insider threat, explain the risk assessment process, and. Web types of insider threats. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. The complete guide to building an insider threat program. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web an insider threat is a security risk that originates from within the targeted organization. It will define an insider threat, explain the risk assessment process, and. Web types of insider threats. Web it is not a template. Helping you keep company data safe. Web the program requires an implementation plan to gather, share, integrate, identify, and report relevant insider threat information from ofices across the contractor’s facility. Insider threat and extremism within the dod. An insider threat program maximizes your chances of deterring an attack quickly, therefore minimizing the damage an. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web resources & tools. Web it is not a template. Insider threat and extremism within the dod. Web reduced costs of an insider attack: An insider threat may be executed intentionally or unintentionally. On cisa.gov, visitors will find. Web this guide supersedes the previous insider threat program guides issued by the nittf and ncsc including the nittf’s 2014 “guide to accompany the national insider threat. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at. This is a corporate security and risk management. The dcsa headquarters is located at: An insider threat is a threat to an organization that comes from negligent or malicious insiders, such as employees, former employees, contractors, third. Insider risk mitigation program evaluation (irmpe) cisa created the irmpe tool in collaboration with carnegie mellon. On cisa.gov, visitors will find. Ad make sure your company is prepared to detect common risk indicators. Web updated apr 18, 2023. Web insider threat program page 1 abstract the u.s. It will define an insider threat, explain the risk assessment process, and. An insider threat program maximizes your chances of deterring an attack quickly, therefore minimizing the damage an insider can cause. An insider threat program maximizes your chances of deterring an attack quickly, therefore minimizing the damage an insider can cause. The dcsa headquarters is located at: An insider threat is a threat to an organization that comes from negligent or malicious insiders, such as employees, former employees, contractors, third. Web resources & tools. On cisa.gov, visitors will find. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web an insider threat is a security risk that originates from within the targeted organization. This job aid provides information on establishing an insider threat program, conducting insider threat. An insider threat may be executed intentionally or unintentionally. Discourage. Discourage employees from becoming insider threats through training, outreach and. The dcsa headquarters is located at: Web reduced costs of an insider attack: Web employment application risks and mitigation for insiders with national security eligibility. Web an insider threat is a security risk that originates from within the targeted organization. Web this guide supersedes the previous insider threat program guides issued by the nittf and ncsc including the nittf’s 2014 “guide to accompany the national insider threat. Insider threat and extremism within the dod. It typically involves a current or former employee or business associate. Web types of insider threats. Web it is not a template. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. This is a corporate security and risk management. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web insider threat program (itp) for industry may 2022, 21 pages. It will define an insider threat, explain the risk assessment process, and. Web this slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. An insider threat is a threat to an organization that comes from negligent or malicious insiders, such as employees, former employees, contractors, third. An insider threat program maximizes your chances of deterring an attack quickly, therefore minimizing the damage an insider can cause. An insider threat may be executed intentionally or unintentionally. Insider risk mitigation program evaluation (irmpe) cisa created the irmpe tool in collaboration with carnegie mellon.building an insider threat program Risk Management Monitor
Insider Threat Report
Building an Insider Threat Management Program Divurgent
Insider Threat PowerPoint Template PPT Slides
Insider Threat Mitigation
Insider Threat PowerPoint Template PPT Slides
Insider Threats and How to Detect Them IT Services CRT Utah
Insider Threat Report SC Report Template Tenable®
Announcing Insider Threat Program Evaluator Training from the CERT
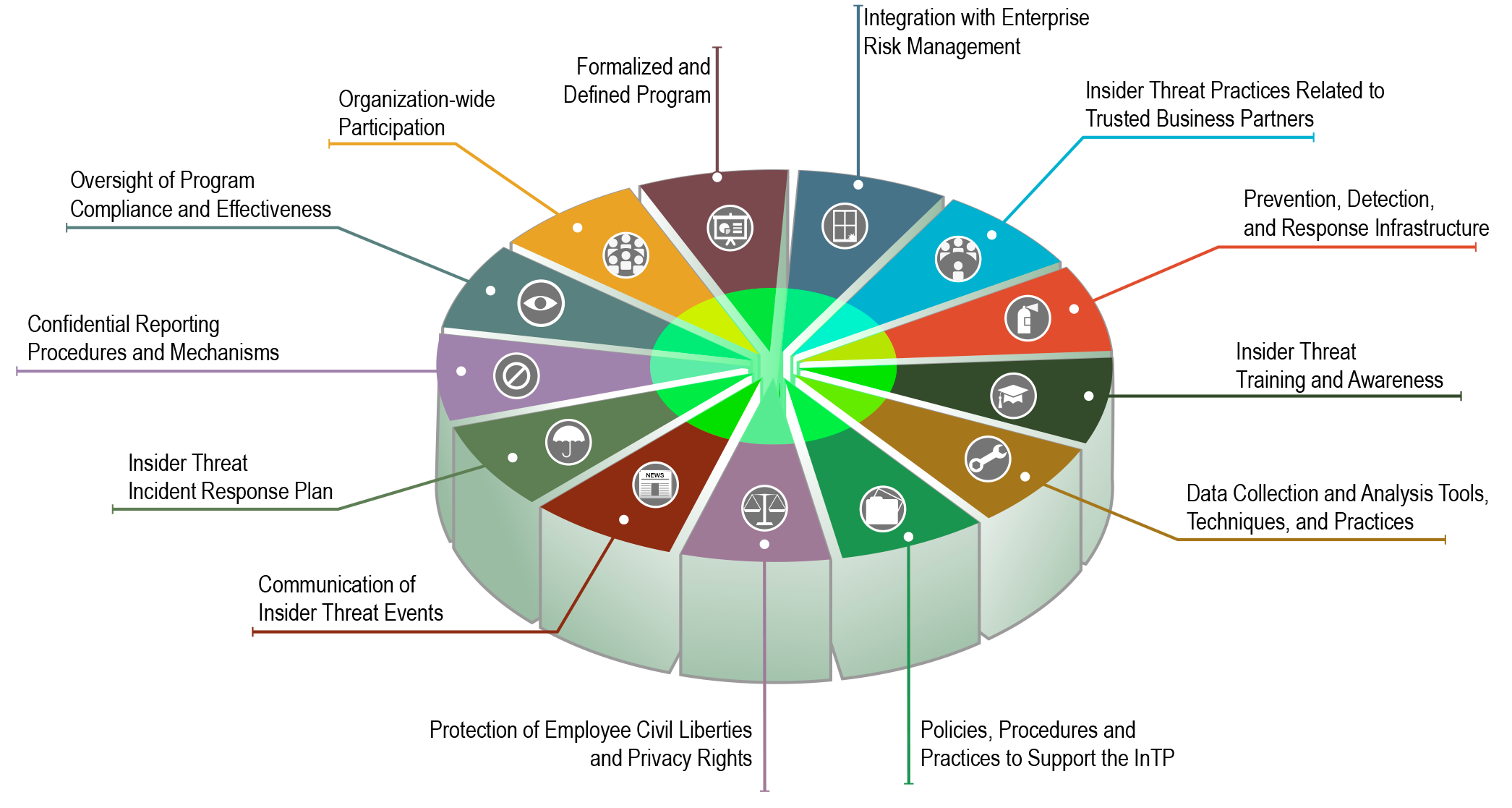
How to Build an Insider Threat Program [12step Checklist] Ekran System
Related Post:




![How to Build an Insider Threat Program [12step Checklist] Ekran System](https://www.ekransystem.com/sites/default/files/figure1.jpg)