Insider Threat Policy Template
Insider Threat Policy Template - Web the new definitions of “insider threat” and “insider” expands upon the definitions found in eo 13587 and the national insider threat policy and minimum standards for executive. This plan establishes policy and assigns responsibilities for the insider threat program (itp). More industry insider threat information and resources. Web foreword departments and agencies with mature, proactive insider threat programs are better postured to deter, detect, and. Web the publication is designed to raise awareness of insider threats to critical infrastructure organizations, provide information on how to incorporate this threat vector into. Nuclear regulatory commission’s (nrc) itp is limited to insider threats, as defined by the national insider threat policy, and does not extend to other types of. Web it is not a template. Roadmap for business achievement analysis. Web this publication outlines emerging insider threat risks and helps member firms identify, prevent, detect, and respond to these threats, including: Ad 80% of insider risk incidents stem from the most common business scenarios. Web communication plan for insider threat awareness. Web an insider threat is when a current or former employee, contractor or business partner, who has or had authorized access to an organization’s network systems, data or premises,. Insider threat indicators in uam june 2023, 7. Web the new definitions of “insider threat” and “insider” expands upon the definitions found in eo. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web this publication outlines emerging insider threat risks and helps member firms identify, prevent, detect, and respond to these threats, including: Web the publication is designed to raise awareness of insider threats to critical infrastructure organizations, provide information on how to incorporate. Web this publication outlines emerging insider threat risks and helps member firms identify, prevent, detect, and respond to these threats, including: Web the new definitions of “insider threat” and “insider” expands upon the definitions found in eo 13587 and the national insider threat policy and minimum standards for executive. The itp will seek to establish a secure operating environment for.. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. More industry insider threat information and resources. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web this slide provides details regarding indicators associated to. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. The itp will seek to establish a secure operating environment for. Web it is not a template. Web. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web the insider threat overlays correlates and applies the insider threat related requirements established in these regulatory and statutory references, along with insider. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. The. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. This is a corporate security and risk management. Web the publication is designed to raise awareness of insider threats to critical infrastructure organizations, provide information on how to incorporate this threat vector into. Defining the threat, detecting. Web home page | cisa An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web foreword departments and agencies with mature, proactive insider threat programs are better postured to deter, detect, and. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Code42® delivers faster, more comprehensive responses to insider risk. Nuclear regulatory commission’s (nrc) itp is limited. Insider threat indicators in uam june 2023, 7. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web in november 2012, the white house issued national insider threat policy for executive branch agencies. This plan establishes policy and assigns responsibilities for the insider threat program (itp).. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web an insider threat is when a current or former employee, contractor or business partner, who has or had authorized access to an organization’s network systems, data or premises,. Code42® delivers faster, more comprehensive responses to insider risk. Web communication plan for insider threat awareness. Roadmap for business achievement analysis. The itp will seek to establish a secure operating environment for. Web it is not a template. Code42® delivers faster, more comprehensive responses to insider risk. Ad 80% of insider risk incidents stem from the most common business scenarios. This is a corporate security and risk management. Web the publication is designed to raise awareness of insider threats to critical infrastructure organizations, provide information on how to incorporate this threat vector into. Web this publication outlines emerging insider threat risks and helps member firms identify, prevent, detect, and respond to these threats, including: This plan establishes policy and assigns responsibilities for the insider threat program (itp). On cisa.gov, visitors will find. Web the new definitions of “insider threat” and “insider” expands upon the definitions found in eo 13587 and the national insider threat policy and minimum standards for executive. Nuclear regulatory commission’s (nrc) itp is limited to insider threats, as defined by the national insider threat policy, and does not extend to other types of. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Web this slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Web home page | cisa42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Building an Insider Threat Management Program Divurgent
Insider Threats Risks, Identification and Prevention
Insider Threat Mitigation
10+ Sample Threat Assessments Sample Templates
Insider Threat PowerPoint Template PPT Slides
How to Prevent Insider Threats Case Studies, Examples, Types (2022)
How to Build an Insider Threat Program [12step Checklist] Ekran System
Insider Threat Report SC Report Template Tenable®
Related Post:
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-03.jpg?w=395)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-08.jpg)
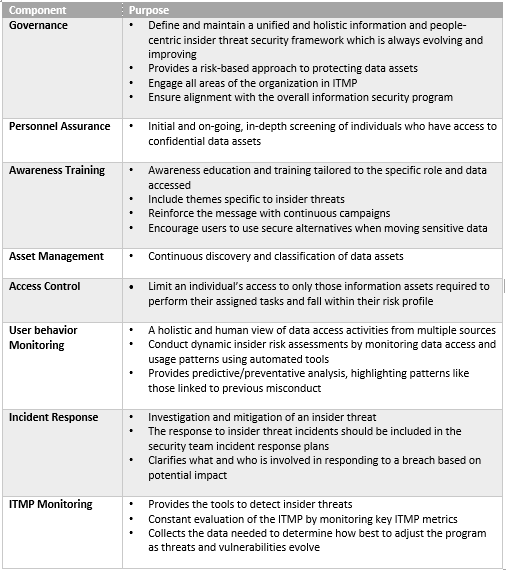



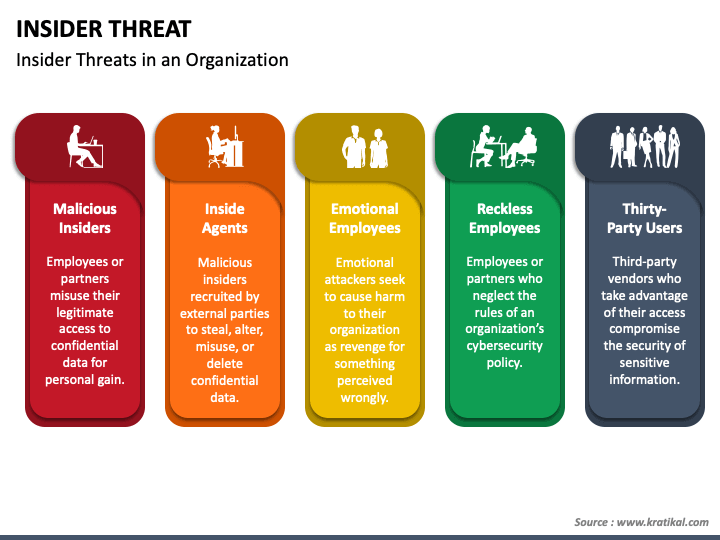

![How to Build an Insider Threat Program [12step Checklist] Ekran System](https://www.ekransystem.com/sites/default/files/figure1.jpg)
