Insider Threat Plan Template
Insider Threat Plan Template - Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. With axonius, see all assets in context, uncover gaps, and automate action. The dcsa headquarters is located at: Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web overview organizations of all sizes are vulnerable to an insider threat. Web 19 establish an insider threat program on october 7, 2011, the president signed executive order 13587, “structural reforms to improve security of classified. This is a corporate security and risk management. Roadmap for business achievement analysis. Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements any specific updates will most likely occur with new. Ad make sure your company is prepared to detect common risk indicators. Ad make sure your company is prepared to detect common risk indicators. Roadmap for business achievement analysis. This fact sheet provides organizations a fundamental overview of insider threats and the key components to building an insider. Web an insider threat program plan for malicious insiders should revolve around spotting and reviewing warning signs. Web nispom v3 ( aka 32 cfr. Web it is not a template. Roadmap for business achievement analysis. Empower your team with huntress mdr. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. This is a corporate security and risk management. Insider threat indicators in uam june 2023, 7. On cisa.gov, visitors will find. This fact sheet provides organizations a fundamental overview of insider threats and the key components to building an insider. Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements any specific updates will most likely occur with new.. Web overview organizations of all sizes are vulnerable to an insider threat. Ad learn how caasm solution axonius helps you achieve asset visibility. Web how we work national insider threat task force (nittf) nittf resource library nittf produced guides & templates this section of the resource library provides guidance. Defining the threat, detecting and identifying the threat, assessing the threat,. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Learn how businesses defend against threats with mdr for microsoft 365. Web overview organizations of all sizes are vulnerable to an insider threat. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and. Web overview organizations of all sizes are vulnerable to an insider threat. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Ad learn how caasm solution axonius helps you achieve asset visibility. Empower your team with huntress mdr. Web insider threat programs are designed to deter, detect, and. Web dcsa continues to assess compliance with minimum insider threat requirements, which provide the basic elements necessary to establish a fully functional insider threat. Web insider threat 101 fact sheet. Ad make sure your company is prepared to detect common risk indicators. When planning, communicate and coordinate with your. Web it is not a template. On cisa.gov, visitors will find. More industry insider threat information and resources. Major indicators of cybersecurity insider threat. Empower your team with huntress mdr. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements any specific updates will most likely occur with new. Web how we work national insider threat task force (nittf) nittf resource library nittf produced guides & templates this section of the resource library provides guidance. Ad make sure your company is. The dcsa headquarters is located at: Ad learn how caasm solution axonius helps you achieve asset visibility. Discover examples of data movements that should be flagged by your it or security team. Workers and managers should be connected to a. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. When planning, communicate and coordinate with your. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Roadmap for business achievement analysis. Web an insider threat program plan for malicious insiders should revolve around spotting and reviewing warning signs. Web nispom v3 ( aka 32 cfr part 117) there are no significant changes to insider threat program requirements any specific updates will most likely occur with new. Web how we work national insider threat task force (nittf) nittf resource library nittf produced guides & templates this section of the resource library provides guidance. Discover examples of data movements that should be flagged by your it or security team. Web this slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Web communication plan for insider threat awareness. This is a corporate security and risk management. This fact sheet provides organizations a fundamental overview of insider threats and the key components to building an insider. More industry insider threat information and resources. Discover examples of data movements that should be flagged by your it or security team. At the end of this course, students will recognize national minimum standards outlined in executive order 13587 and will be able to apply those standards to. Learn how businesses defend against threats with mdr for microsoft 365. An insider threat is the potential for an insider to use their authorized access or special understanding of. Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Major indicators of cybersecurity insider threat. An organization’s plan must be tailored to the specific insider threat program (itp) procedures and processes in place at the organization. On cisa.gov, visitors will find.Building an Insider Threat Management Program Divurgent
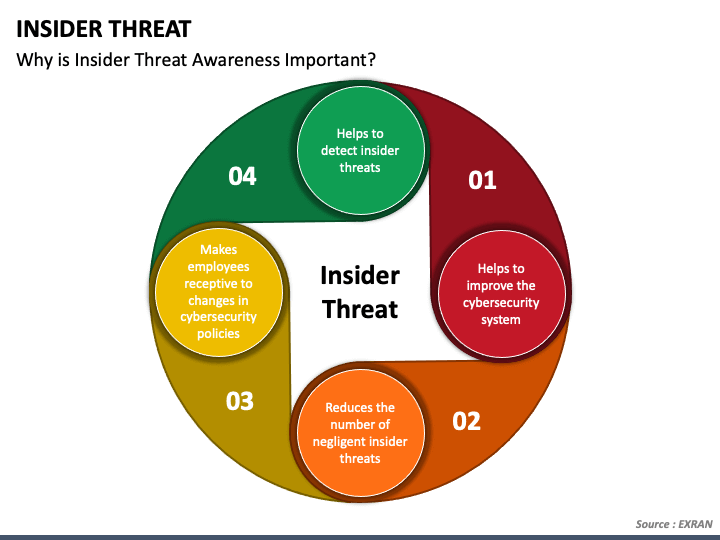
Insider Threat PowerPoint Template PPT Slides
How to Build an Insider Threat Program [12step Checklist] Ekran System
Insider Threat Report SC Report Template Tenable®
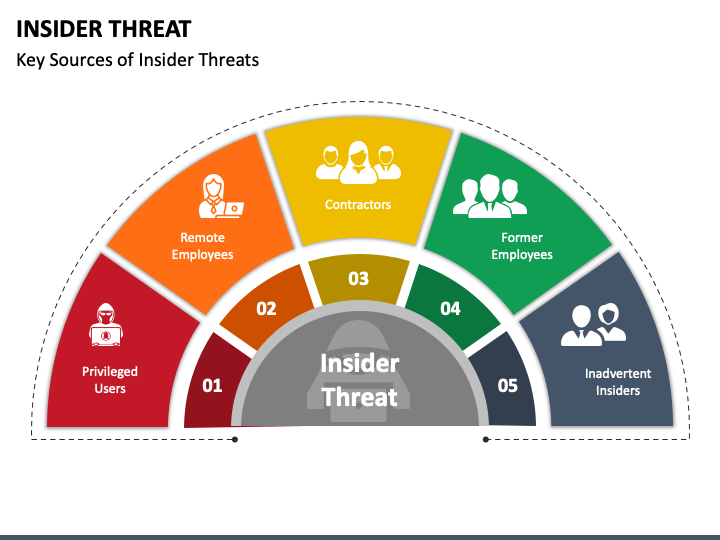
Insider Threat PowerPoint Template PPT Slides
Insider Threat PowerPoint Template PPT Slides
2017 Insider Threat Guide
Insider Threat Mitigation
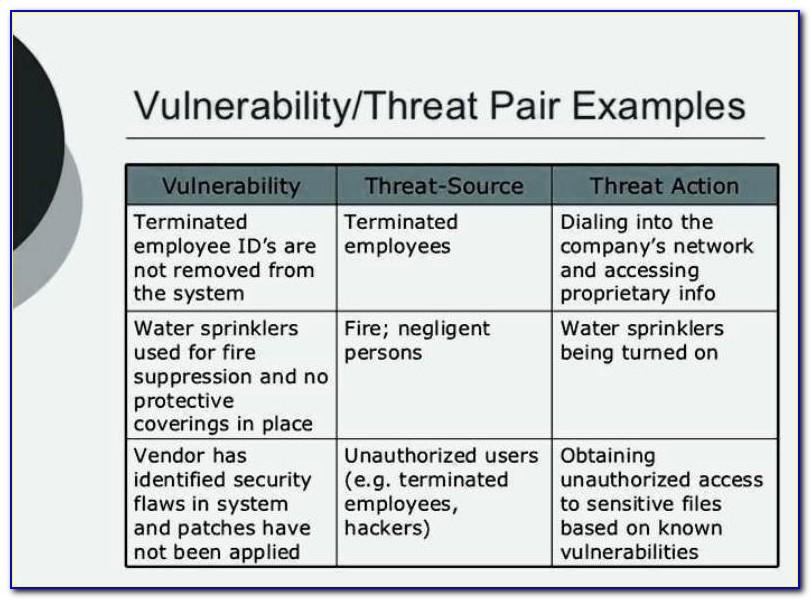
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
Related Post:
![How to Build an Insider Threat Program [12step Checklist] Ekran System](https://www.ekransystem.com/sites/default/files/figure1.jpg)