Encryption Policy Template
Encryption Policy Template - Additionally, this policy provides direction to ensure that federal regulations are followed, and legal authority is granted for the dissemination and use of encryption. Distribution list as other group. It does not mandate the use of encryption; Data encryption this document provides the university community with the information required to effectively and efficiently plan,. Web the policy template addresses the information security compliances arising from iso 27001 controls pertaining to information security encryption requirements, thus. Web the objective of these guidelines is to provide guidance in understanding encryption and the encryption key management required for maintaining the confidentiality and integrity. Need some assistance on below: The purpose of this policy is to provide guidance that limits the use of encryption to those algorithms that have received substantial public review and have. Web policy on the use of encryption the purpose of this document is to define rules for the use of cryptographic controls, as well as the rules for the use of cryptographic keys, in order. Web this document is a resource for agencies to establish policies and practices for secure encryption management. Web according to infosec institute, the main purposes of an information security policy are the following: Web policy on the use of encryption the purpose of this document is to define rules for the use of cryptographic controls, as well as the rules for the use of cryptographic keys, in order. Web sans has developed a set of information security. Ad ibm security guardium data encryption is a family of encryption & key management software. These are free to use and fully customizable to your company's it security practices. Part 1 provides general guidance and best practices. The purpose of this policy is to provide guidance that limits the use of encryption to those algorithms that have received substantial public. This guide gives the correlation between 49 of. Does irm only supports groups with type: Help guide your business's encrpytion management with our encryption policy. Distribution list as other group. Web to provide our members a template that can be modified for your company’s use in developing a virtual private network (vpn) policy. Policies are foundational components of security programs. This guide gives the correlation between 49 of. Web to provide our members a template that can be modified for your company’s use in developing a virtual private network (vpn) policy. Save 8 hours with the prewritten and fully populated iso27001 cryptographic control and encryption. To establish a general approach to information security. Save 8 hours with the prewritten and fully populated iso27001 cryptographic control and encryption. Concise & clear cybersecurity & privacy documentation based on industry best practices. Web this document is a resource for agencies to establish policies and practices for secure encryption management. This guide gives the correlation between 49 of. The purpose of the (district/organization) encryption. Web sans has developed a set of information security policy templates. This guide gives the correlation between 49 of. It does not mandate the use of encryption; Web this document is a resource for agencies to establish policies and practices for secure encryption management. Web to provide our members a template that can be modified for your company’s use in. Distribution list as other group. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web sample encryption policy [free download] written by editorial team in resources & tools. It does not mandate the use of encryption; Download this free encryption policy template and use it for your. Data encryption this document provides the university community with the information required to effectively and efficiently plan,. To establish a general approach to information security. It consists of three parts. Web the objective of these guidelines is to provide guidance in understanding encryption and the encryption key management required for maintaining the confidentiality and integrity. Distribution list as other group. Web this document is a resource for agencies to establish policies and practices for secure encryption management. Distribution list as other group. The purpose of the (district/organization) encryption. Web the policy template addresses the information security compliances arising from iso 27001 controls pertaining to information security encryption requirements, thus. Web microsoft purview message encryption leverages the protection features in azure. Distribution list as other group. Encryption management policy, version 1.0.0 purpose. Web sans has developed a set of information security policy templates. Ad ibm security guardium data encryption is a family of encryption & key management software. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). These are free to use and fully customizable to your company's it security practices. Data encryption this document provides the university community with the information required to effectively and efficiently plan,. Web sans has developed a set of information security policy templates. It consists of three parts. This guide gives the correlation between 49 of. It does not mandate the use of encryption; Additionally, this policy provides direction to ensure that federal regulations are followed, and legal authority is granted for the dissemination and use of encryption. Need some assistance on below: To establish a general approach to information security. The purpose of this policy is to provide guidance that limits the use of encryption to those algorithms that have received substantial public review and have. Does irm only supports groups with type: Web download encryption management policy template. Encryption management policy, version 1.0.0 purpose. Web iso 27001 cryptographic control and encryption policy template. Web policy on the use of encryption the purpose of this document is to define rules for the use of cryptographic controls, as well as the rules for the use of cryptographic keys, in order. Ad ibm security guardium data encryption is a family of encryption & key management software. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web the encryption management policy applies to all individuals who administer the (company) cardholder data environments (cde). Web to provide our members a template that can be modified for your company’s use in developing a virtual private network (vpn) policy. Concise & clear cybersecurity & privacy documentation based on industry best practices.Encryption Policy Template Master of Documents
Data Encryption Policy Template ControlCase
50 Best Privacy Policy Templates [with GDPR] TemplateArchive
Laptop Security Policy How to create a Laptop Security Policy
Encryption Key Management Policy Template Policy template, Enterprise
Awesome Data Encryption Policy Template Policy template, Templates
Policy on cryptography
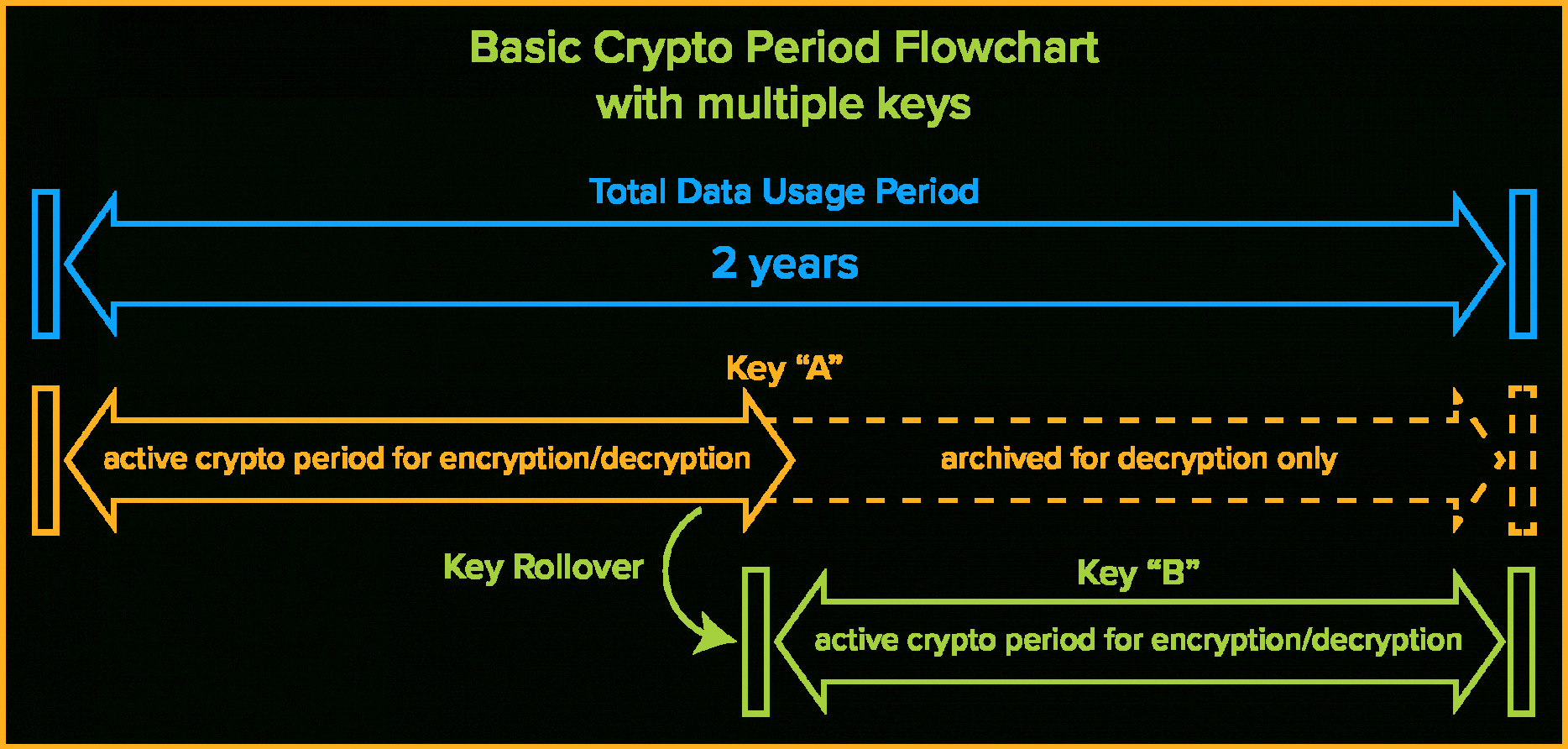
Encryption Key Management Policy Template
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Acceptable Encryption Policy Key (Cryptography) Transport Layer
Related Post:


![50 Best Privacy Policy Templates [with GDPR] TemplateArchive](https://templatearchive.com/wp-content/uploads/2019/03/privacy-policy-template-16-1.jpg)




![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-17.jpg)
