Cybersecurity Program Template
Cybersecurity Program Template - Check out our library of free information technology and cyber security policy templates. Use our sample cyber security business plan created using upmetrics business plan software to start writing your business plan in no time. Cyber security program components the purpose of a cyber security strategy is to define the goals and objectives of the cyber security program to assure the confidentiality, integrity, and availability of the information vital to achieving the utility’s mission. Web get ahead of your 2023 security goals. Our small firm cybersecurity checklist supports small firms in establishing a cybersecurity program to: Web the department of energy (doe) has created three templates to assist you in drafting your plan: This cybersecurity program charter template is a prepopulated template that it leaders can customize to create their cybersecurity program charter. Master information security policy and procedures template (updated mar 2021) incident response policy template (updated mar 2021) cybersecurity program strategic plan template (new mar 2021) social media policy template (dec 2019) password policy template (oct 2018) policy development protocol template (aug. Even though half of all people are adhering to the five core security behaviors, there’s still lots of room for improvement, according to this year’s. The templates can be customized and used as an outline of an organizational policy, with additional details to be added by the end user. 15 credits $1,017 per credit. Ad code42® delivers faster, more comprehensive responses to insider risk. Master information security policy and procedures template (updated mar 2021) incident response policy template (updated mar 2021) cybersecurity program strategic plan template (new mar 2021) social media policy template (dec 2019) password policy template (oct 2018) policy development protocol template (aug. Protect assets from cyber. Final date by which all management, operational, and technical cyber security controls will be implemented for cdas is provided within the [licensee] proposed implementation schedule. Collection, management, and analysis of audit logs can help detect, understand, or recover from an attack. Easily build and maintain your security program, and automate all of your compliance docs Web cybersecurity program templates |. Axio cybersecurity program assessment tool. Use our sample cyber security business plan created using upmetrics business plan software to start writing your business plan in no time. Web general information this guide is intended to help applicants complete the fiscal year (fy) 2023 tcgp cybersecurity plan template and includes key tips and instructions for specific sections of the template in. Immigrants are coming to north dakota for jobs. 15 credits $1,017 per credit. This platform provides a range of resources chosen based on the needs of the small business community. This cybersecurity program charter template is a prepopulated template that it leaders can customize to create their cybersecurity program charter. Web the cybersecurity program charter establishes the purpose for the. Master information security policy and procedures template (updated mar 2021) incident response policy template (updated mar 2021) cybersecurity program strategic plan template (new mar 2021) social media policy template (dec 2019) password policy template (oct 2018) policy development protocol template (aug. Web general information this guide is intended to help applicants complete the fiscal year (fy) 2023 tcgp cybersecurity plan. Apply by july 1 to start august 26. This platform provides a range of resources chosen based on the needs of the small business community. Axio cybersecurity program assessment tool. Web cybersecurity program templates | tiffin cyber tiffin cyber provides cybersecurity services for the smb and m&a markets ranging from current state and gap analysis to full remediation, solutions and. Apply by july 1 to start august 26. Download our information and cyber security policy templates for smbs, startups, and enterprises. Plan for the response when a compromise. Collection, management, and analysis of audit logs can help detect, understand, or recover from an attack. Want to protect yourself from emerging cyber threats? Web related nist cybersecurity framework (csf) categories: This ppt template showcases the cybersecurity management action plan. This platform provides a range of resources chosen based on the needs of the small business community. Download our information and cyber security policy templates for smbs, startups, and enterprises. Final date by which all management, operational, and technical cyber security controls will be. Ad finish your fedramp ato package faster and with more accuracy. It presents the action plan in two parts, namely risk identification and risk treatment. Identify and assess cybersecurity threats; The risk treatment table covers the sections, plan, risk owner, and resolution date. This ppt template showcases the cybersecurity management action plan. Want to protect yourself from emerging cyber threats? Apply by july 1 to start august 26. Download our information and cyber security policy templates for smbs, startups, and enterprises. Download cyber security word templates designs today. It presents the action plan in two parts, namely risk identification and risk treatment. Ad finish your fedramp ato package faster and with more accuracy. Not everyone is glad to see them. It presents the action plan in two parts, namely risk identification and risk treatment. Ad microsoft defender online security solutions to help secure your business & family. Discover how to easily & efficiently spot unusual data behavior to protect your business. The templates can be customized and used as an outline of an organizational policy, with additional details to be added by the end user. Web general information this guide is intended to help applicants complete the fiscal year (fy) 2023 tcgp cybersecurity plan template and includes key tips and instructions for specific sections of the template in the order in which they appear on the form. (link is external) (a free assessment tool that assists in identifying an organization’s cyber posture.) baldrige cybersecurity excellence builder. Web cybersecurity program templates | tiffin cyber tiffin cyber provides cybersecurity services for the smb and m&a markets ranging from current state and gap analysis to full remediation, solutions and oversight. A cyber security strategy is a plan of action designed to achieve a Web get ahead of your 2023 security goals. Web the cyber readiness program also provides a template for an incident response plan that your organization can customize. Final date by which all management, operational, and technical cyber security controls will be implemented for cdas is provided within the [licensee] proposed implementation schedule. This platform provides a range of resources chosen based on the needs of the small business community. Axio cybersecurity program assessment tool. Ad code42® delivers faster, more comprehensive responses to insider risk. Apply by july 1 to start august 26. Web protecting investors means protecting their data, too. Even though half of all people are adhering to the five core security behaviors, there’s still lots of room for improvement, according to this year’s. Concise & clear cybersecurity & privacy documentation based on industry best practices.Present your cyber security firm’s objectives with this business plan
Cyber Security PowerPoint Template Designs SlideSalad
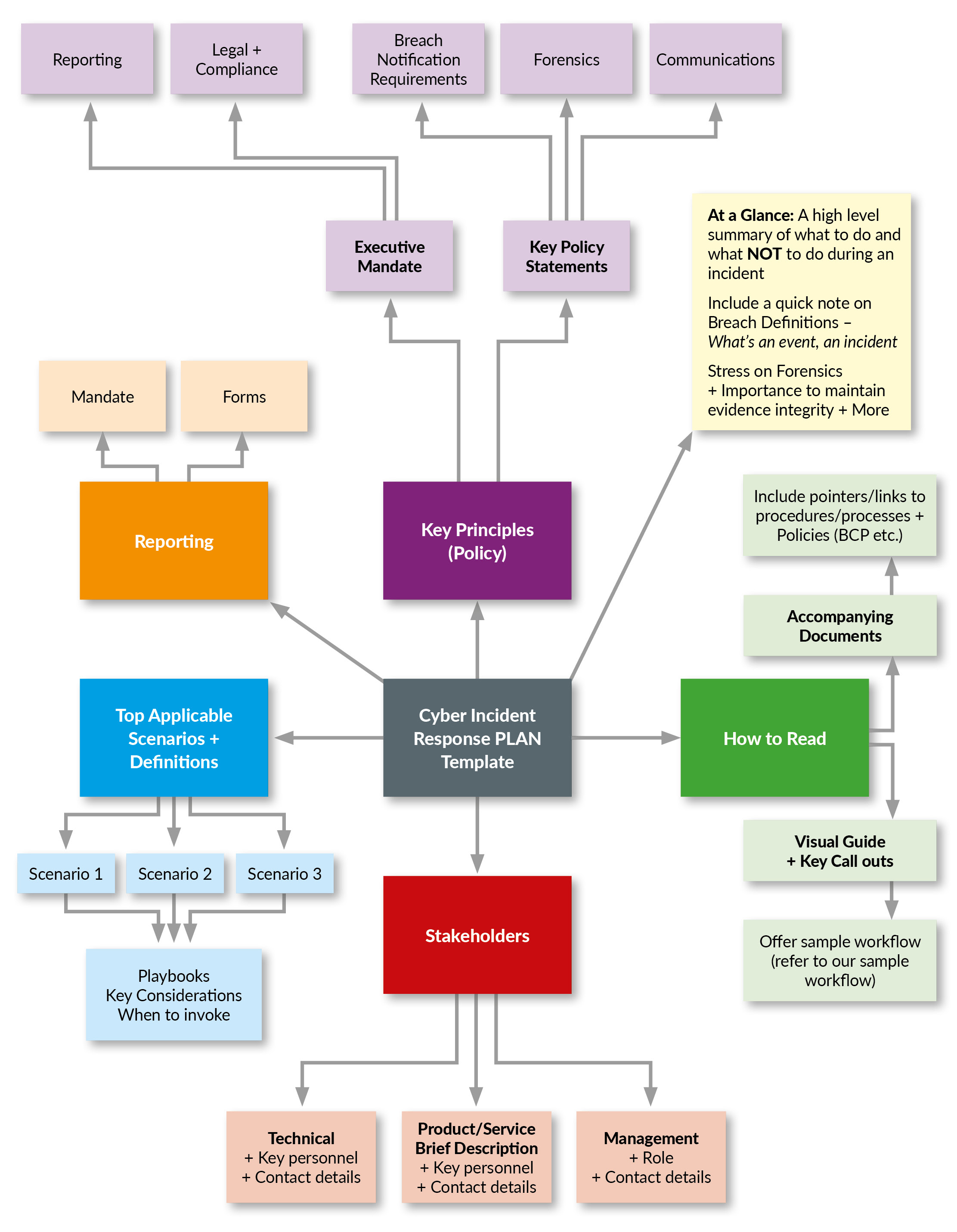
Cybersecurity Incident Response Plan Template and Example UK Cyber
Effective Cyber Security Template PPT Slide Designs
Best Cyber Security PowerPoint Slide Template Designs
Flyer Cyber Security Programs
Cyber Security Business Plan Google Slides & PPT Template
Cybersecurity Enhancement Program Data Sheet CrowdStrike
Ready To Use Cyber Security Template PPT With Six Nodes
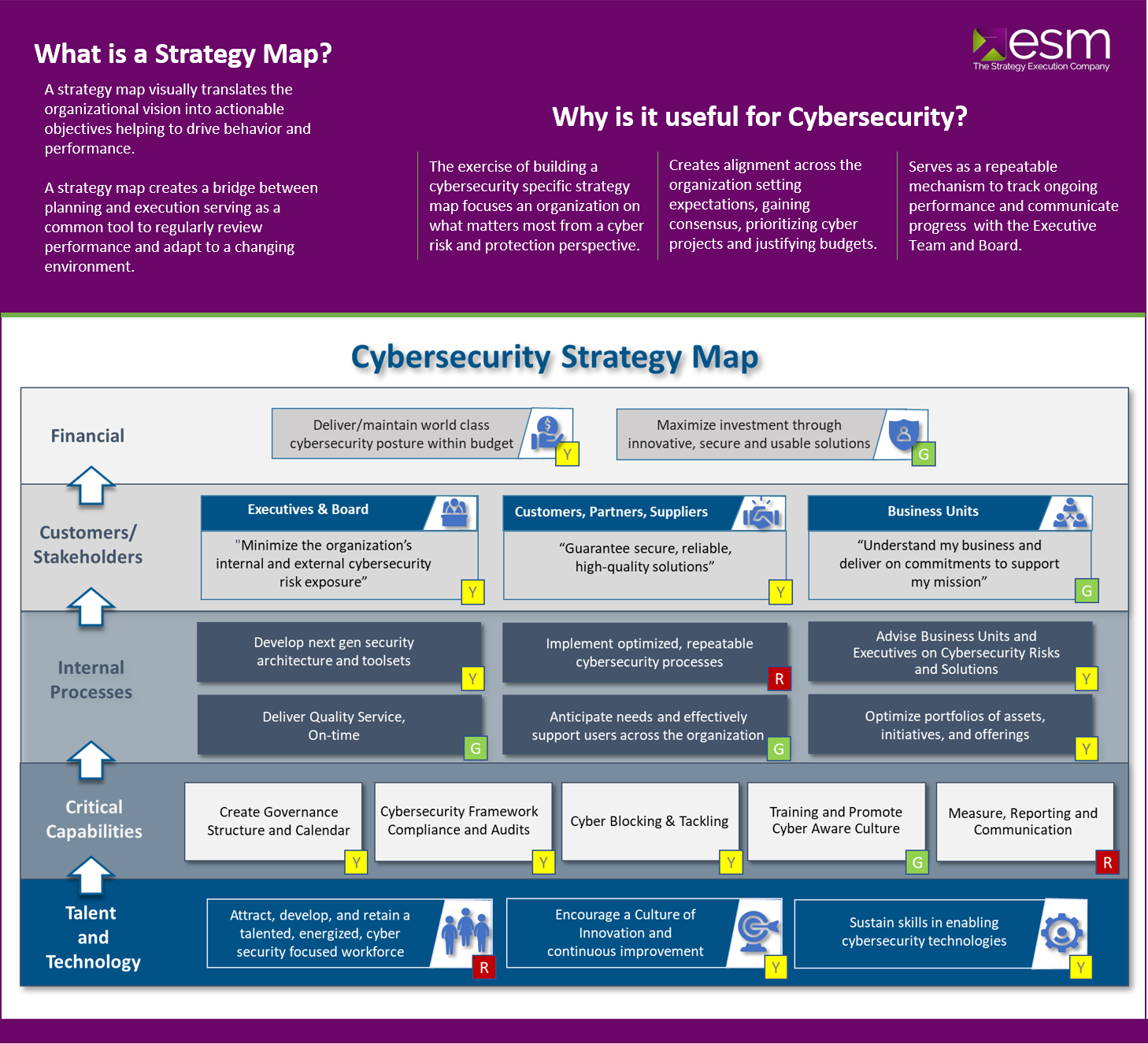
Building a Winning Cybersecurity Program Part 1
Related Post: