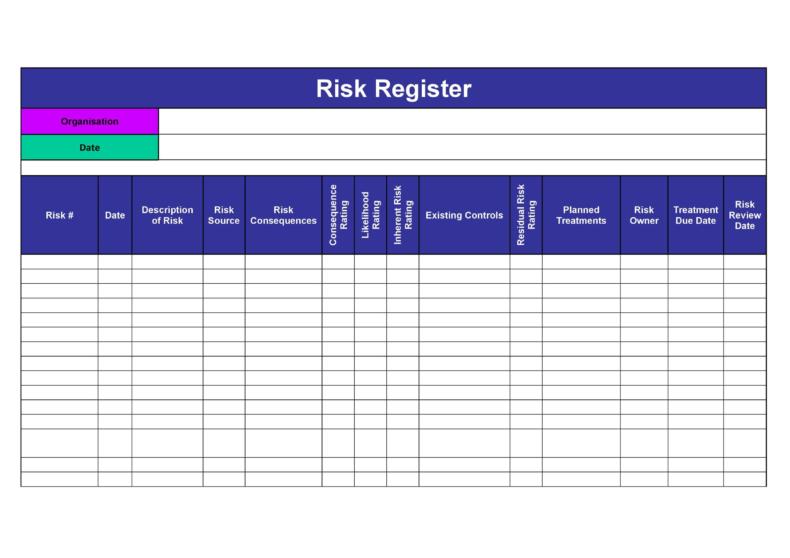
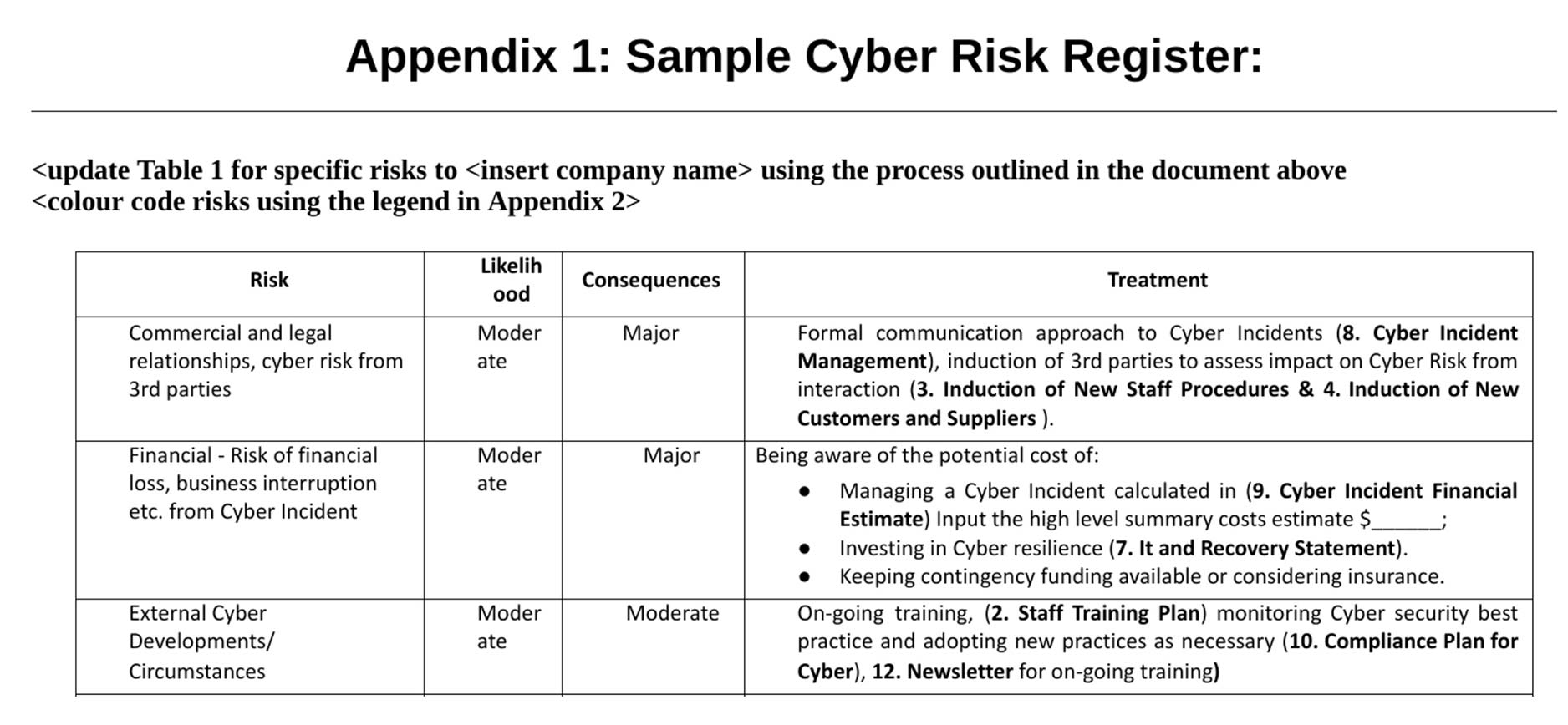
Cyber Security Risk Register Template
Cyber Security Risk Register Template - Current risks are comprised of both accepted risks and risk. You can download our free risk register template for excel. Integrating cybersecurity and enterprise risk management (erm) nist cybersecurity framework (csf) risk management framework (rmf) privacy. Web “that is not the answer, emphatically. Risk identification your first task it to determine any. It’s a starting point for building out your own risk register. Web clickup's cyber security risk register template is designed to help you effectively manage and mitigate cyber risks. Concise & clear cybersecurity & privacy documentation based on industry best practices. In hyperproof, organizations can set up multiple risk registers to track different types of risks and customize the scales/risk scoring for each risk register. For example, section 4.8 of the ai. Putting solid security in place is key to getting the coverage you need. Evaluate the scope for the risk assessment. Stay ahead of online threats with microsoft defender for business or individuals. Web resources include, but are not limited to: Share the financial impact of cyber risk with the business & prioritize what matters most Web december 20, 2022 floq.to/aotmu the following risk register is designed to help you identify and manage the risks that your organization faces. Current risks are comprised of both accepted risks and risk. Stay ahead of online threats with microsoft defender for business or individuals. Web to conduct a cybersecurity risk assessment, we recommend following these five steps. Web focusing. Web how to build and maintain a risk register (plus examples & a risk register template) by hyperproof team on september 18, 2023 as security,. Stay ahead of online threats with microsoft defender for business or individuals. Identify all potential cyber risks 2. Web resources include, but are not limited to: Web to conduct a cybersecurity risk assessment, we recommend. Evaluate the scope for the risk assessment. Web the cyber security risk register is developed in four stages, following the framework outlined in iso 27005: Web clickup's cyber security risk register template is designed to help you effectively manage and mitigate cyber risks. Web focusing on the use of risk registers to set out cybersecurity risk, this document explains the. Ad code42® delivers faster, more comprehensive responses to insider risk. Web best guide to building a risk register (plus examples & template) by jingcong zhao on december 7, 2020 as security, compliance, and risk management. Web a tool like a risk register is a centralized record of identified cybersecurity threats that can be managed and tracked for all business units. Putting solid security in place is key to getting the coverage you need. In hyperproof, organizations can set up multiple risk registers to track different types of risks and customize the scales/risk scoring for each risk register. Web 6 ai innovation and risk for national security systems must be managed appropriately, but these systems are governed through other policy. Web. The case for using multiple risk registers. Identify all potential cyber risks 2. Ad microsoft defender online security solutions to help secure your business & family. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. • understand your risk landscape through a. It’s a starting point for building out your own risk register. Web best guide to building a risk register (plus examples & template) by jingcong zhao on december 7, 2020 as security, compliance, and risk management. Web a tool like a risk register is a centralized record of identified cybersecurity threats that can be managed and tracked for all business. Current risks are comprised of both accepted risks and risk. Web to conduct a cybersecurity risk assessment, we recommend following these five steps. Web nist privacy risk assessment methodology (pram) the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess,. Stay ahead of online threats with microsoft defender for business or individuals.. Web 6 ai innovation and risk for national security systems must be managed appropriately, but these systems are governed through other policy. Web a tool like a risk register is a centralized record of identified cybersecurity threats that can be managed and tracked for all business units to use within risk treatment plans. Web how to build and maintain a. Stay ahead of online threats with microsoft defender for business or individuals. Ad microsoft defender online security solutions to help secure your business & family. Here are the main elements of this folder template:. Identify all potential cyber risks 2. A central record of current risks, and related information, for a given scope or organization. Web clickup's cyber security risk register template is designed to help you effectively manage and mitigate cyber risks. Web to conduct a cybersecurity risk assessment, we recommend following these five steps. It’s a starting point for building out your own risk register. The case for using multiple risk registers. Evaluate the scope for the risk assessment. Web nist privacy risk assessment methodology (pram) the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess,. For example, section 4.8 of the ai. Web how to build and maintain a risk register (plus examples & a risk register template) by hyperproof team on september 18, 2023 as security,. Discover how to easily & efficiently spot unusual data behavior to protect your business. Concise & clear cybersecurity & privacy documentation based on industry best practices. Share the financial impact of cyber risk with the business & prioritize what matters most Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. It is not intended to be a. The first step in conducting a. Web the cyber security risk register is developed in four stages, following the framework outlined in iso 27005:Risk Register Examples for Cybersecurity Leaders Security Boulevard
Cyber Crime Risk Assessment Adam M. Erickson
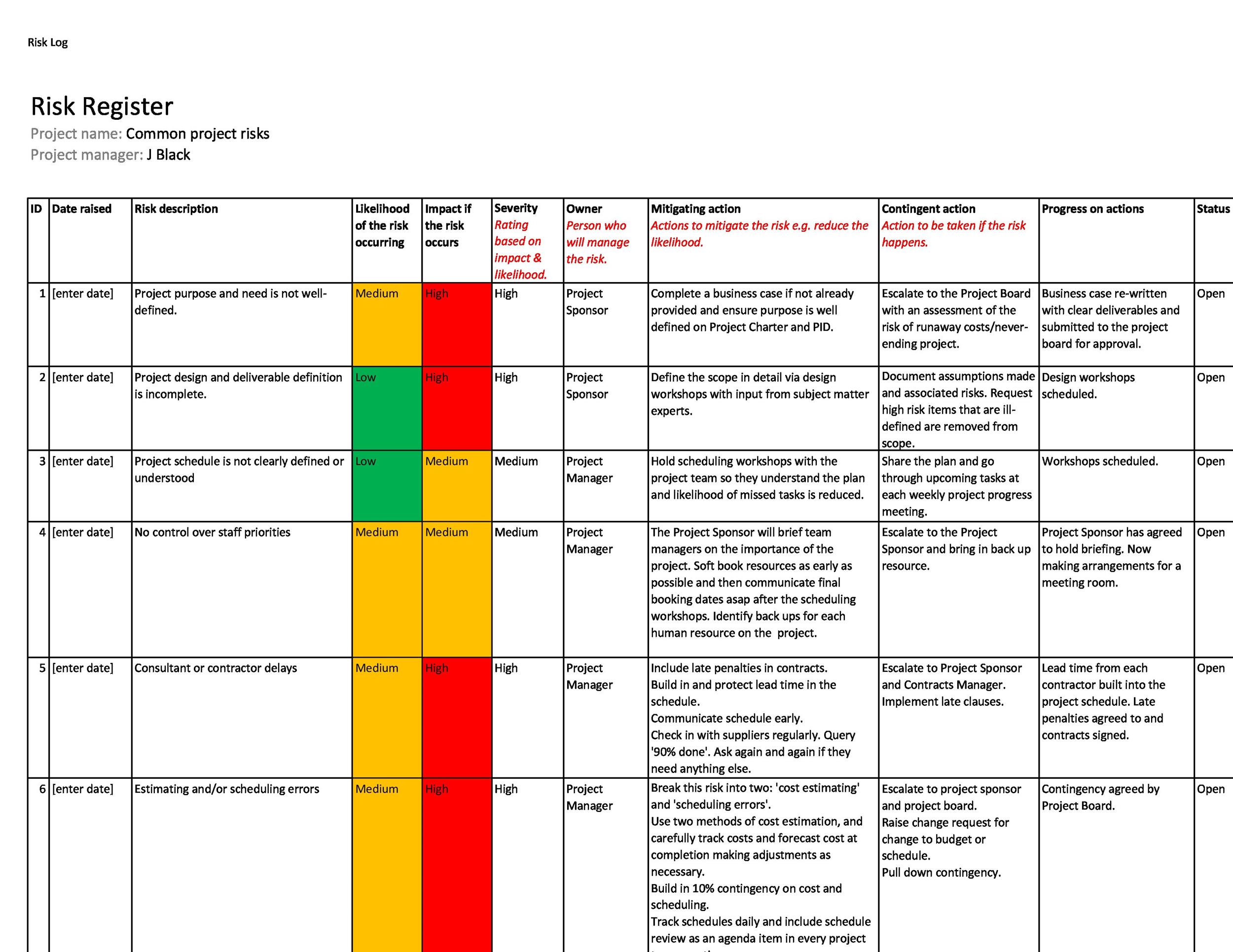
Creating A Risk Register For Information Security Risk And Compliance
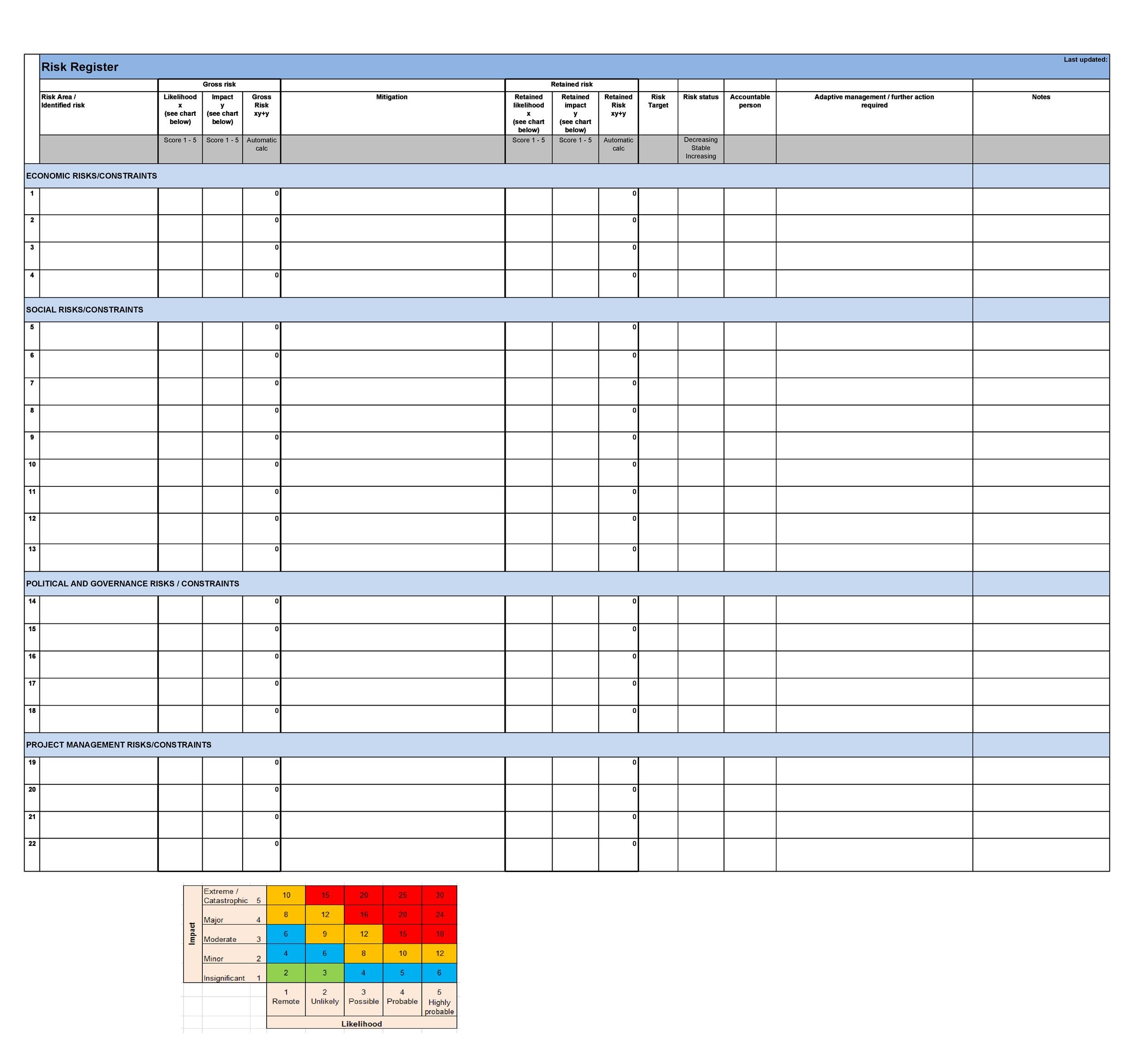
45 Useful Risk Register Templates (Word & Excel) ᐅ TemplateLab
45 Useful Risk Register Templates (Word & Excel) ᐅ TemplateLab
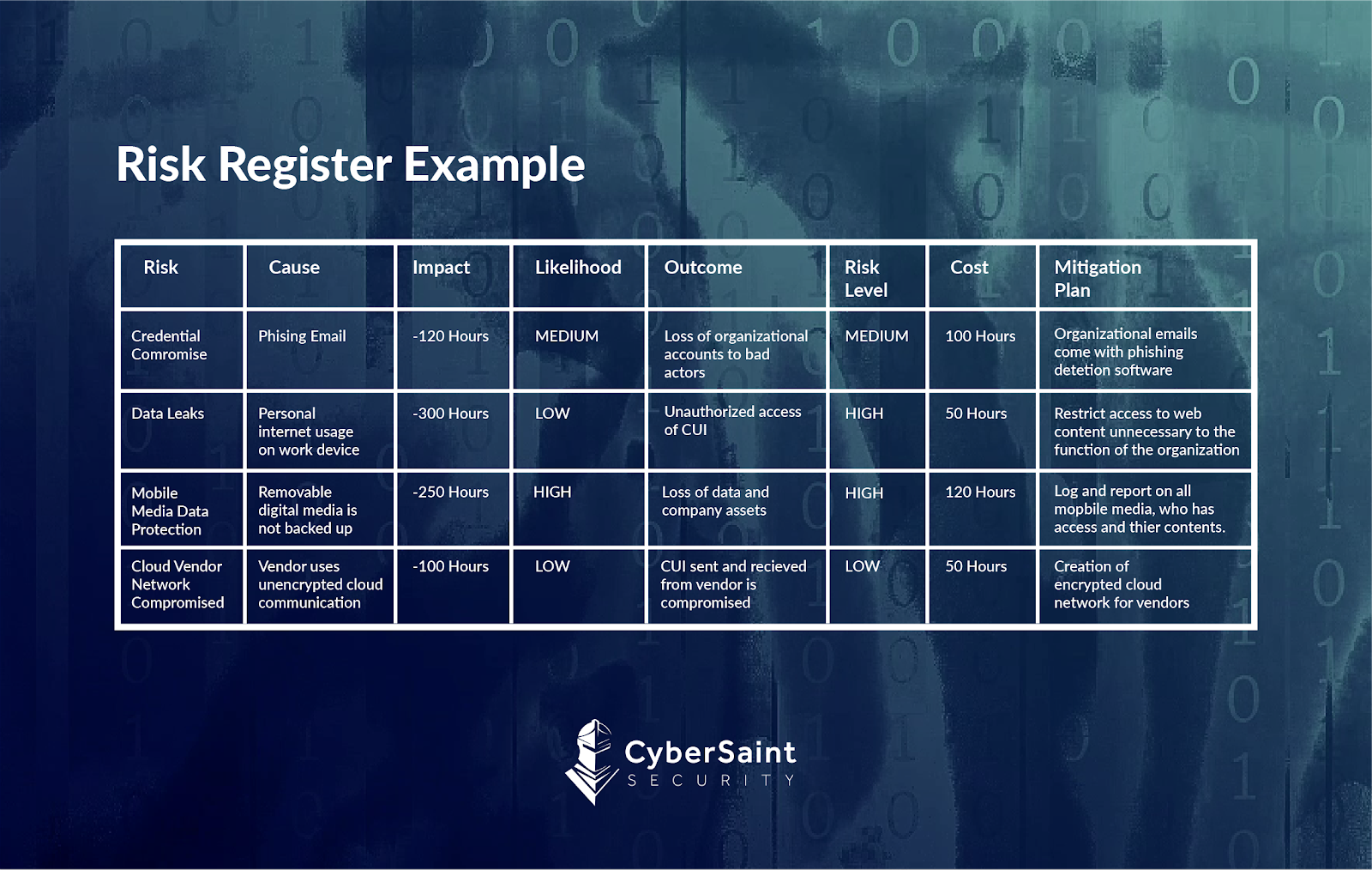
Risk Register Example Risk Risk Management
45 Useful Risk Register Templates (Word & Excel) ᐅ TemplateLab
Cybersecurity Risk Assessment Template for creating cybersecurity
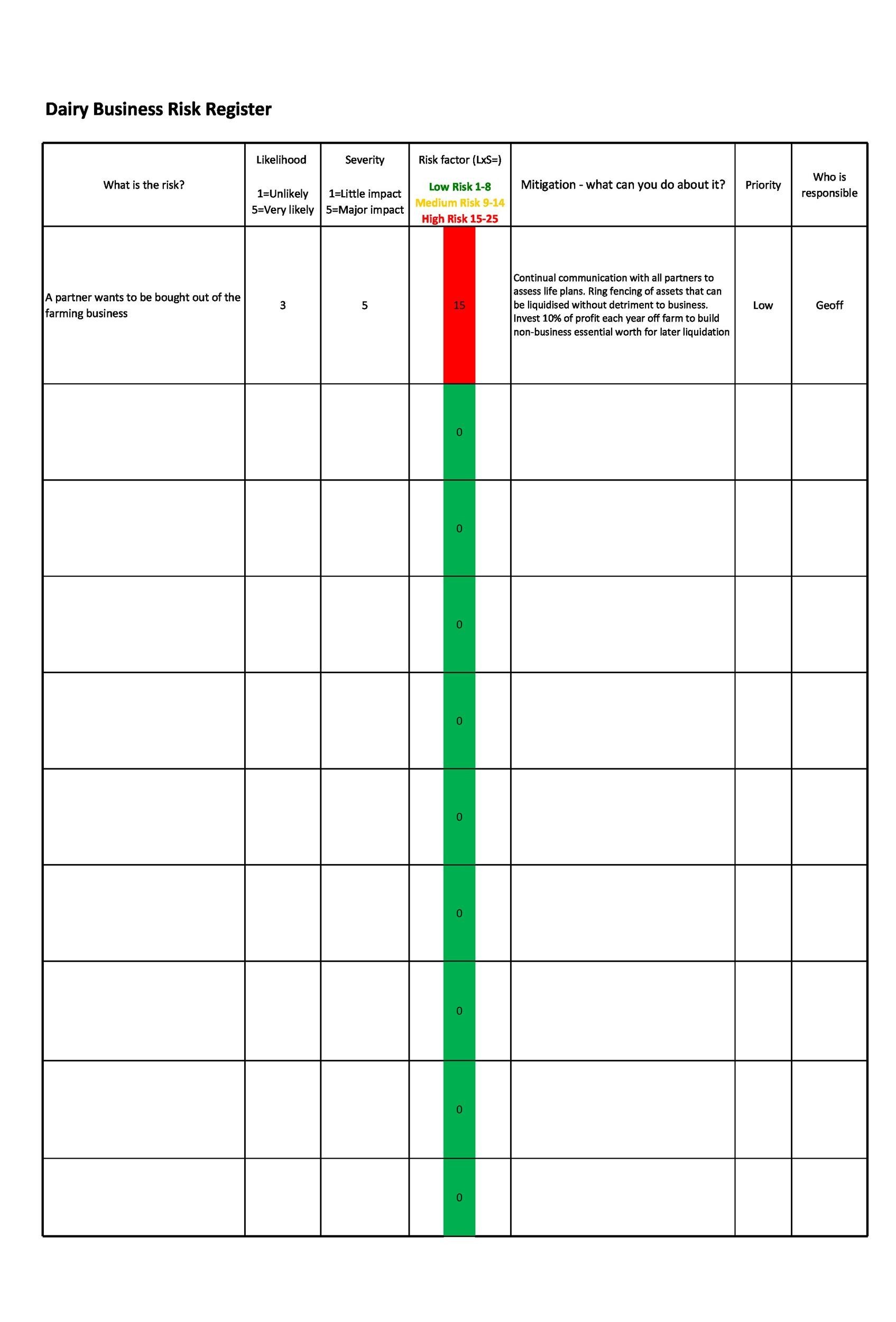
53 Useful Risk Register Templates (Word & Excel) ᐅ TemplateLab
Cyber Procedures to Tailor and Implement Pink Cyber Cyber security
Related Post: